Telecom Security
How to Protect Your Smart Home from IoT Threats?
Our world is increasingly becoming digital as we are moving towards a society that is interconnected through a web of
SOC Analyst Training – Cyber Attack Intrusion Analysis With SIEM Tools | From Scratch To Advanced
SOC Training is one of the most important concern in order to build a Quality Security Operation Center Team to
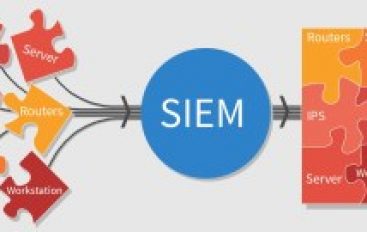
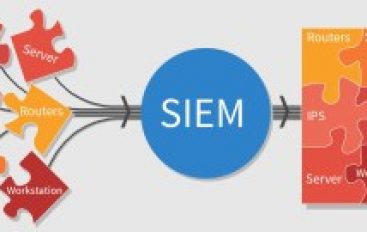
Indicator Of Attack(IoA’s) And Activities – SOC/SIEM – A Detailed Explanation
What is an Indicator of Attack (IOA) IoA’s is some events that could reveal an active attack before indicators of
Modern CyberSOC – A Brief Implementation Of Building a Collaborative Cyber Security Infrastructure
In earlier years, everyone depends on SOC (includes firewalls, WAF, SIEM,etc.) and the prioritize in building the SOC provides security
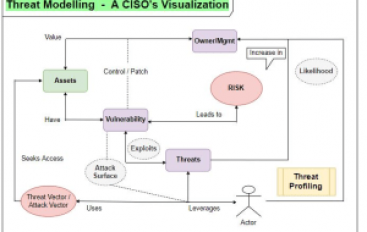
SOC Second Defense Phase – Understanding the Cyber Threat Profiles
In the first phase of architecturing the SOC, we have seen the basic level understanding of the attacks and necessary
SOC First Defense phase – Understanding the Cyber Attack Chain – A Defense Approach with/without SOC
This article will help you to understand the modern cyber threats and the most commonly used attack surfaces behind any
Indicator Of Attack(IoA’s) And Activities – SOC/SIEM – A Detailed Explanation
What is an Indicator of Attack (IOA) IoA’s is some events that could reveal an active attack before indicators of
Modern CyberSOC – A Brief Implementation Of Building a Collaborative Cyber Security Infrastructure
In earlier years, everyone depends on SOC (includes firewalls, WAF, SIEM,etc.) and the prioritize in building the SOC provides security
Five Key Capabilities To Look for in a Managed Web Application Firewall (WAF) Provider
Web-based applications security relies on a number of factors among them is a Web Application Firewall (WAF). Cyberattacks are pouring
SOCs Struggle with Staffing, Reporting and Visibility
Staffing remains an issue for security operations centers (SOCs), which continue to struggle with reporting and documentation while barely being
Intrusion Detection System (IDS) and Its Detailed Working Function – SOC/SIEM
An intrusion detection system (IDS) is a type of security software designed to automatically alert administrators when someone or something
Cyber Security is Not an Easy Game for CISO – It’s an Absolute End Game!
Let’s breakdown the little pieces and the critical dots to connect in the perspective of a CISO and a point-of-view
IoT Devices at a Risk
Security researchers at Senrio, an IoT focused security firm, have a discovered a stack buffer overflow vulnerability (CVE-2017-9765) in an
Managed Firewall for Financial Applications
News of the second Kmart credit-card breach in three years at the retailer and the number of breaches at financial
Top 5 VoIP Security Tips for Businesses
VoIP, short for Voice over Internet Protocol, allows businesses to make free, or very low-cost, telephone calls over the Internet.
Why Managed DNS Means Secure DNS
Home security systems are designed to keep intruders out. But even with the most advanced systems in place, vulnerabilities still