Managed SOC
SOC Analyst Training – Cyber Attack Intrusion Analysis With SIEM Tools | From Scratch To Advanced
SOC Training is one of the most important concern in order to build a Quality Security Operation Center Team to fight against advanced threats that target the organization network. Sophisticated detection and prevention technologies are mandatory implementations by the security
What is an Indicator of Attack (IOA) IoA’s is some events that could reveal an active attack before indicators of compromise become visible. Use of IoA’s provides a way to shift from reactive cleanup/recovery to a proactive mode, where attackers
Modern CyberSOC – A Brief Implementation Of Building a Collaborative Cyber Security Infrastructure
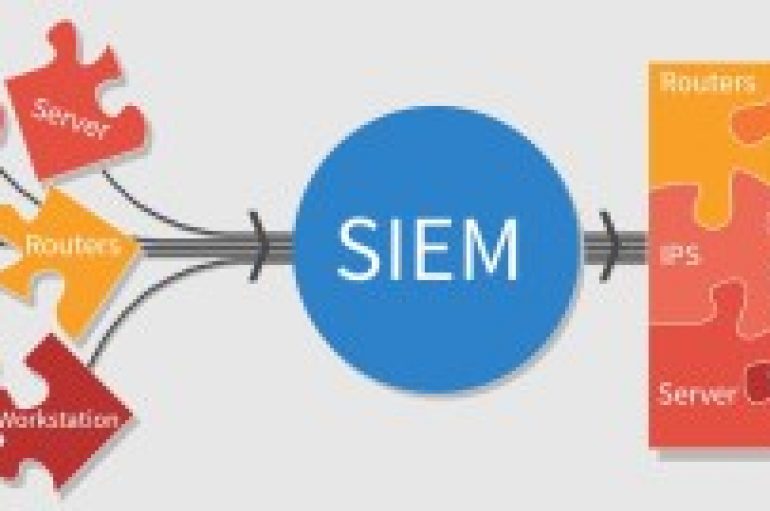
In earlier years, everyone depends on SOC (includes firewalls, WAF, SIEM,etc.) and the prioritize in building the SOC provides security and the CIA was maintained. However, later the emerge of the attacks and the threat actors becomes more challenge and
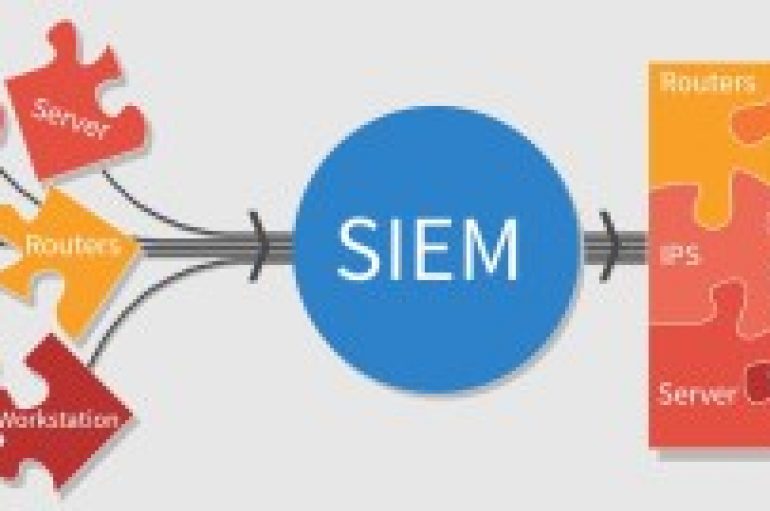
In the first phase of architecturing the SOC, we have seen the basic level understanding of the attacks and necessary steps to breaking the Attack Chain. Let’s move on to the phases of SOC and advanced level of protecting the
SOC First Defense phase – Understanding the Cyber Attack Chain – A Defense Approach with/without SOC
This article will help you to understand the modern cyber threats and the most commonly used attack surfaces behind any malware/cyber-attacks. In most times, the cyber attacks are getting executed in stages. So the SOC team must understand the attack
What is an Indicator of Attack (IOA) IoA’s is some events that could reveal an active attack before indicators of compromise become visible. Use of IoA’s provides a way to shift from reactive cleanup/recovery to a proactive mode, where attackers
Modern CyberSOC – A Brief Implementation Of Building a Collaborative Cyber Security Infrastructure
In earlier years, everyone depends on SOC (includes firewalls, WAF, SIEM,etc.) and the prioritize in building the SOC provides security and the CIA was maintained. However, later the emerge of the attacks and the threat actors becomes more challenge and
Staffing remains an issue for security operations centers (SOCs), which continue to struggle with reporting and documentation while barely being able to stay afloat in a sea of alerts and false positives, according to the annual State of the SOC
An intrusion detection system (IDS) is a type of security software designed to automatically alert administrators when someone or something is trying to compromise information system through malicious activities such as DDOS Attacks or through security policy violations. An IDS
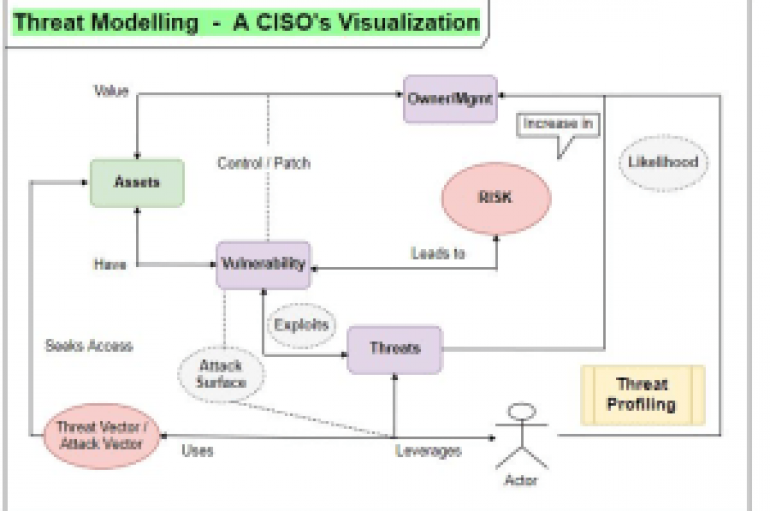
Let’s breakdown the little pieces and the critical dots to connect in the perspective of a CISO and a point-of-view from CyberSpace. The threats and the risks are potentially increasing in Cyber Space and no organization is 100% safe, every