Archive
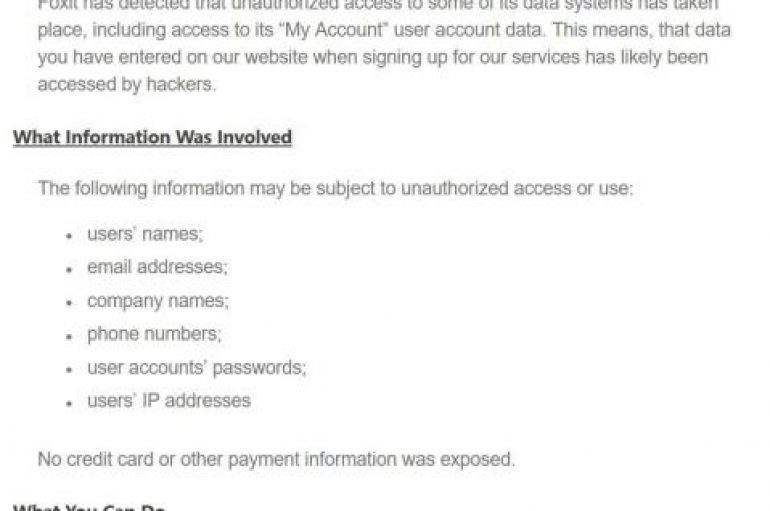
Foxit Software, the company behind the Foxit PDF reader app, disclosed a data breach that exposed customers’ information, including passwords. Foxit Software, the PDF software provider behind the Foxit PDF reader app disclosed a security breach that took place recently
Researchers from Google Project Zero team uncovered a five dangerous iOS exploit chain in wide that can hack almost every iPhone running with iOS 10 to 12 by just trick them to visit the hacked website. An unknown hacking group
Hack Exploited Apple Users for Two Years
Researchers from Google’s Project Zero have discovered a threat campaign that operated against users of Apple iOs devices for two years. Earlier this year Google’s Threat Analysis Group (TAG) discovered that a small collection of hacked websites was being used
Critical Vulnerability in Cisco REST API Container Let Hackers Remotely Bypass Cisco IOS XE Device
Cisco released a new security update for several products and fixed a critical authentication bypass vulnerability that resides in Cisco REST API virtual service container. Totally 11 vulnerabilities are fixed, 1 vulnerability categorized under “critical” severity, 5 of them are
Fileless Malware Detections Soar 265% in 2019
Fileless malware, BEC, digital extortion and ransomware attacks all grew significantly between 2018 and the first six months of this year, according to new data from Trend Micro. The security giant blocked over 26.8 billion threats in the first half
Security experts at Kaspersky have spotted a new Android remote access tool (RAT) dubbed BRATA used to spy on Brazilian users. Security experts at Kaspersky have discovered a new Android remote access tool (RAT), tracked as BRATA (the name comes
HackerOne Announces Five New $1m White Hats
The UK has its first $1 million white hat hacker, after bug bounty platform HackerOne announced five new security researchers had reached the milestone. The five millionaire hackers are: Mark Litchfield (@mlitchfield) from the UK, Nathaniel Wakelam (@nnwakelam) from Australia,
Phishing Campaign Hides Malware in Resumes
For many people, applying for a new job is a soul-crushing activity on a par with cleaning the bathroom in a six-person student dorm room. Landing a new role can mean spending hours searching for positions, rewriting your resume and
The cost of global data breaches to victim organizations will rise to over $5 trillion by 2024 as regulatory fines take hold and firms become more dependent on digital systems, according to new predictions from Juniper Research. The figures come
Lumber Liquidators, a leading specialty retailer of hard-surface flooring in North America, announced that a malware attack took down its network. North American hard-surface flooring retailer Lumber Liquidators revealed that it was victim of a security incident, a malware-based attack
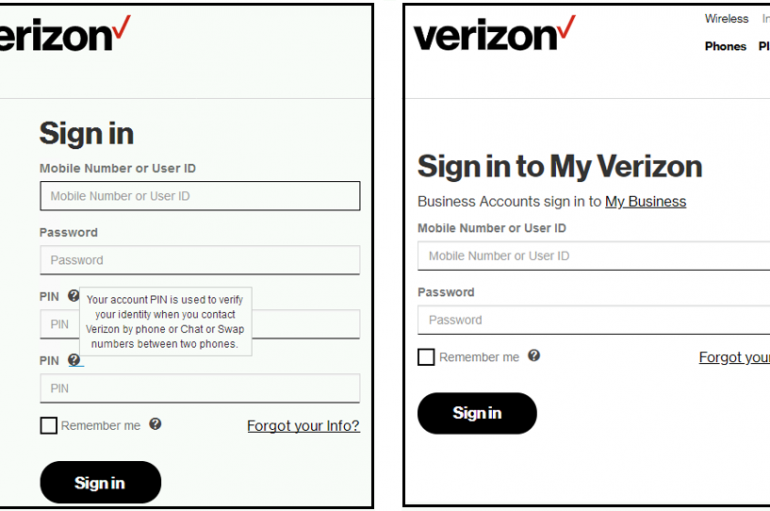
A new Trickbot Trojan variant is targeting Verizon Wireless, T-Mobile, and Sprint users, confirming the evolution of the threat. TrickBot is a popular banking Trojan that has been around since October 2016, its authors has continuously upgraded it by implementing
The woman arrested for allegedly stealing data from Capital One and over 30 other organizations has also been accused of crypto-jacking, in a new indictment filed on Wednesday. Paige Thompson, 33, was charged with wire fraud and computer fraud and
Have you thought about launching own Cryptocurrency Exchange Platform? That is a good deal, however, such a decision is accompanied by several challenges. Here some tips and a short review on how to start a cryptocurrency exchange. Let’s go today
French Cops Hijacked Retadup Botnet & Remotely Wipe The Malware From 850,000 Infected Computers
Team of French Cops from Cybercrime Fighting Center (C3N) takedown the Retadup worm command & control servers to block the further infection and remotely wipe the malware from 850,000 windows computers. Retadup is a malicious worm that can infect the
TA505 APT Hackers Drop ServHelper and FlawedAmmyy through ISO files to Gain Remote Access
TA505 hacker group continues to evolve by making small changes with their techniques, target countries and combination of techniques for each their campaigns. The group’s active campaigns found in April, June & July, in all the campaigns they continue to
The Great, Big Ransomware Revival
Trends are at play in the realm of malware as much as they are in the fashion world. And in the cyber-criminal underground the threat equivalent of the inexplicably popular skin-tight leggings that would do us all a favor if