IT Security
Ivanti Adds VPN and MDM Technolgies in Double Acquisition
Ivanti has announced the acquisitions of mobile device management vendor MobileIron and secure access and VPN provider Pulse Secure. Under
ATM Penetration Testing – Advanced Testing Methods to Find The Vulnerabilities
ATM Penetration testing, Hackers have found different approaches to hack into the ATM machines. Programmers are not restricting themselves to
Cynet Unveils Complete Cybersecurity with Integrated XDR, MDR and Response Automation
As cybersecurity leaders struggle with a mix of point solutions to defend against a wide range of vulnerabilities and endpoint
Fastly to Acquire Signal Sciences
California edge cloud computing company Fastly has entered into a definitive agreement to acquire American cybersecurity company Signal Sciences. Stock
A Complete Guide to Perform External Penetration Testing on Your Client Network | Step-by-Step Methods
This write-up walks us through one of my many journeys in my external penetration testing and how I compromised the
Lesser-Known Ways to Improve Your Website Security From Cyber Attacks
In many cases, the simplest solutions are the best ones as well. However, when it comes to protecting your website
10 Best Vulnerability Scanning Tools For Penetration Testing – 2020
A Vulnerability Scanning Tools is one of the essential tools in IT departments Since vulnerabilities pop up every day and
Spyse – A Cybersecurity Search Engine For Pentesters
Spyse is a cybersecurity search engine that has caught the attention of many pentesters due to its unique data-gathering design.
Threats on Public Networks: How to Use Them Safely
Navigating through the web can seem like a minefield. It looks like new threats emerge daily, and people need to
Benefits of Vulnerability Assessment
We all know that vulnerability assessment is very important nowadays, and that’s why most of the companies use this assessment.
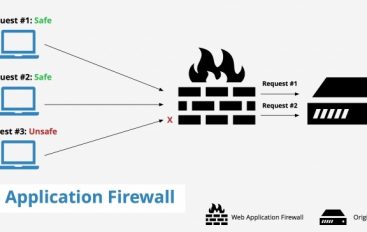
What is a Web Application Firewall (WAF)? Different Types of WAF
A web application firewall is a firewall that monitors, filters and blocks statistics packets as they journey to and from
What is Vulnerability Scoring? A Detailed Report to CVSS
A vulnerability is some aspect of a system functionality, architecture, or configuration that enables cybercriminals to execute attacks, exploit services,
Endpoint Security: How Does It Perform a Vital Role in Enterprise Network Security
A vital part of any comprehensive security program includes endpoint protection. Also known as endpoint security. But both terms refer
10 Most Important Cyber Security Tips To Protect Your Enterprise Network
With its multitude of benefits, one can easily forget that the internet also serves as a grooming ground for cybercriminals.
Web Application Attacks – Types, Impact & Mitigation – Part-4
With this article, we list some of the common web application attacks, impacts, and possible mitigation. In part -4 we
Web Application Attacks – Types, Impact & Mitigation – Part-3
With this article, we list some of the common web application attacks, impacts, and possible mitigation. In part -3 we