Archive
A key highlight of any RSA Conference in San Francisco is the annual “Top 5 Most Dangerous New Attack Techniques and How to Counter Them” session led by experts from the SANS Institute. For the 2020 edition, however, many of
A data breach that exposed patients’ personal health information (PHI) for almost three months went undetected for half a year at a Michigan healthcare group. Hackers gained access to patient data placed in the safekeeping of Munson Healthcare Group by
Delivering a keynote talk at the RSA Conference in San Francisco, Mary T Barra, chairman and CEO of General Motors Company, said “all of you today are the best and strongest line of defense in this on going and even
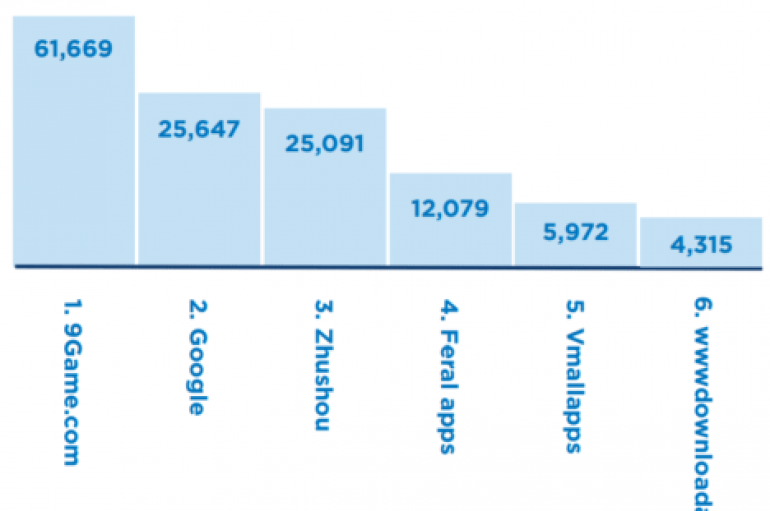
An interesting report published by RiskIQ on 2019 Mobile App Threat Landscape, lists the most dangerous mobile app store online. Mobile users downloaded over 200 billion apps in 2019 and the overall expense in app stores worldwide has been estimated
Free HTTPS tool Let’s Encrypt yesterday announced it has issued its billionth certificate, in what it claims to be a milestone for user privacy and security. Backed by the non-profit Internet Security Research Group (ISRG), the initiative has good reason
A US TV star has lost nearly $400,000 in a classic email fraud scam after a fraudster persuaded her bookkeeper to wire funds to a new bank account. Multi-millionaire Barbara Corcoran describes herself as an “NYC real estate queen” and
Iranian APT Hackers Attack Government Organizations via Weaponized Excel Files to Steal Network Credentials
Researchers observed a new malware called ForeLord from the Iranian APT hackers via weaponized MS excel document to attacker government organizations. Iranian Threat group called COBALT ULSTER aka MuddyWater, Seedworm, TEMP.Zagros is behind this attack and believed to be a
Speaking in a keynote talk at the RSA Conference in San Francisco, Mary T. Barra, chairman and CEO of General Motors Company, said that she acknowledged that “no one in this room needs convincing that there are virtually no industries
#RSAC: How to Hack Society
The method, procedures, and practices used by cybersecurity professionals have relevance beyond just the technology sphere; they can also be used to hack society. That’s the view espoused by Bruce Schneier, security technologist, researcher, and lecturer at the Harvard Kennedy
After three months from the first detection, the Lampion origin was identified. A webserver named “portaldasfinancas” is available in Turkey and has been used to spread the threat in Portugal. Lampion malware is the most critical malware affecting Portuguese users’ last
Criminals are using a combination of server exploitation, email, and voice calls to execute voice phishing attacks, often referred to as vishing. In a session at the RSA Conference in San Francisco, John LaCour, founder and CTO at PhishLabs, and
In a talk at the RSA Conference in San Francisco, Lexis Nexis Risk Solutions director of product management Daniel Ayoub and VP of product management Dean Weinert talked about the reality of which metrics and identifiers browsers release on users.
University Fools Hackers into Sharing Tactics
Researchers at the University of Texas have found a way to bamboozle malicious hackers into giving away their secrets. The DEEP-Dig (DEcEPtion DIGging) method tricks hackers onto a decoy site set up to record whatever sneaky tactics are thrown at
Last year’s data breach at the Desjardins Group will cost the co-operative far more than initially anticipated. Original estimates by the Quebec-based financial institution set the cost of recovering from the breach at $70m. The co-operative has now said that
Traditional organized crime gangs are now making efforts to succeed in financial cybercrime in Latin America. According to research by IntSights into cybercrime activities in central and south America, persistent cyber-criminals are operating extensive schemes targeting banks, hospitality services,and retail
America’s Democratic National Committee has warned its electoral candidates to be wary after a phony Bernie Sanders campaign staffer used a fake domain to contact other political campaigns. The cyber-imposter attempted to set up conversations with at least two other