Archive
Sephora Warns Users of Data Breach
Sephora has notified customers in the Asia-Pacific region who have online accounts that the cosmetics and beauty products retailer suffered a data breach, according to Malay Mail. Customers reportedly received an email in which the company explained that an unauthorized
95% of Pen Test Problems Can Be Easily Resolved
The most common configuration problems found in the majority of penetration tests can be easily resolved with straightforward fixes. Analysis from more than 50 engagements in the first half of 2019 by Lares, shared exclusively with Infosecurity, found that the
LAPD Breach Exposes Thousands of Officers
Personal information on thousands of Los Angeles Police Department (LAPD) officers and applicants appears to have been stolen in a breach of local government security. The suspected hacker claims they have their hands on the data of 2500 LAPD officers,
MoD Data and Device Losses Soar 300%
Total losses of data and devices by the UK’s Ministry of Defence (MoD) have risen by nearly 300% over the past two years, according to official figures. The figure jumped from 117 incidents in 2017-18 to 463 in 2018-19, according
Capital One has announced a major breach of customers’ personal data, affecting over 100 million Americans and a further six million in Canada. The financial institution blamed “unauthorized access by an outside individual” who has been arrested by the FBI
11 Zero-Day Vulnerabilities Found in VxWorks RTOS – 2 Billion Devices are Vulnerable to Remote Hack
Researchers discovered 11 zero-day vulnerabilities dubbed “URGENT/11” in the most widely used operating system VxWorks, a Real-Time Operating System (RTOS) family. VxWorks is Developed as proprietary software by Wind River Systems used in 2 billion devices including Firewalls, MRI machines,
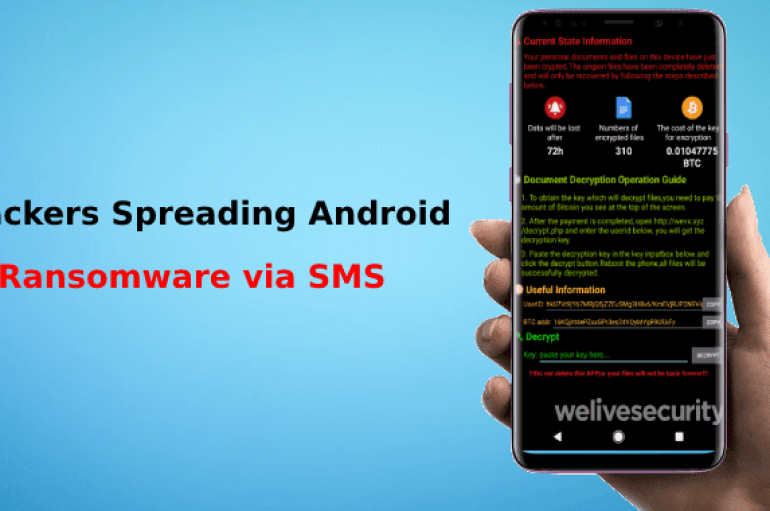
Hackers Spreading Android Ransomware via SMS to your Contacts and Encrypt your Device Files
A new family of Android Ransomware dubbed Android/Filecoder.C distributed various online forums and further uses the victim’s contact list to SMS with a malicious link. ESET detected the ransomware activity since July 12th, 2019, “Due to narrow targeting and flaws
Capital one hacked, the hack exposed more than 100 million customers data across the US and Canada. The breach was learned by Capital One Financial Corporation on July 19, 2019. Following are the personal information affected with the breach that
CASB definition Think of cloud access security brokers (CASBs) as central data authentication and encryption hubs for everything your enterprise uses, both cloud and on-premises and accessed by all endpoints, including private smartphones and tablets. Before the CASB era, enterprise
Flaws Allow Hacker to Bypass Card Limits
New vulnerabilities give hackers the ability to bypass the payment limits on Visa contactless cards regardless of the card terminal, according to new research from Positive Technologies. In a July 29 press release, Positive Technologies said that researchers tested the
Malware Cited As Exploit Most Seen By SOC Teams
Working in the security operations center (SOC) is growing increasingly more painful because of an increasing workload and alert fatigue, according to new research, Improving the Effectiveness of the Security Operations Center, published by the Ponemon Institute and sponsored by
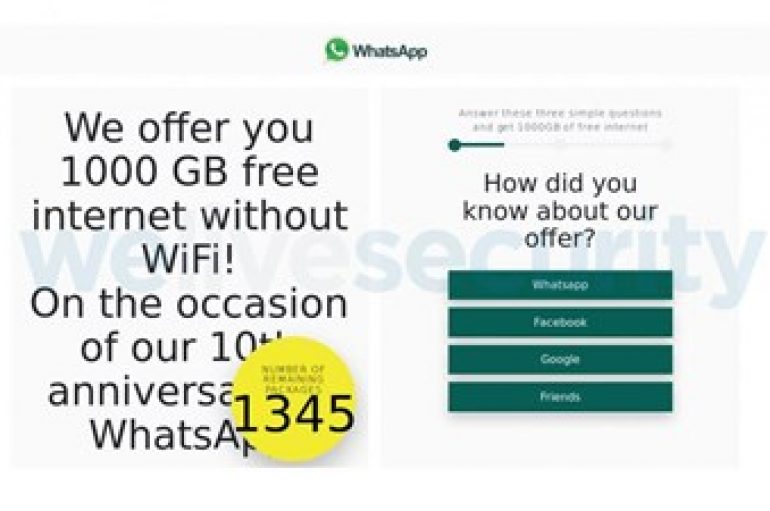
Fake Version of WhatsApp Giving ‘Free Internet’
A new scam is impersonating WhatsApp and using the fraudulent claim that its victims will receive “free internet,” according to ESET researchers. “Researchers in Latin America received a message on WhatsApp stating that the app was giving away 1,000 GB
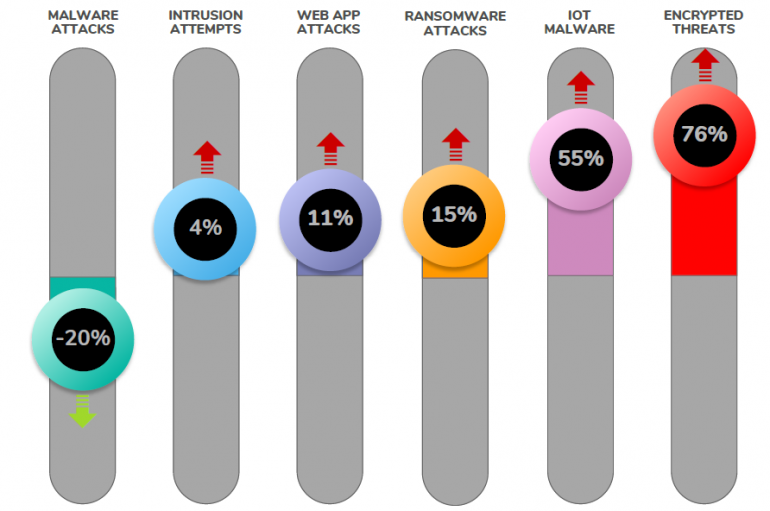
Sonicwall Warns of a Spike in the Number of Attacks Involving Encrypted Malware and IoT Malware
According to experts at Sonicwall, scanning of random ports and the diffusion of encrypted malware are characterizing the threat landscape. In 2018, global malware volume recorded by SonicWall hit a record-breaking 10.52 billion attacks. The situation is better in the
Watch out! Playing a video on Android devices could be a dangerous operation due to a critical CVE-2019-2107 RCE flaw in Android OS between version 7.0 and 9.0. Playing a specially-crafted video on devices with the Android’s native video player
Chinese Hackers Launching Zegost Malware to Attack Government Networks Via Weaponized MS Powerpoint
Researchers discovered a new campaign with Zegost info stealer malware that believed to be originated from Chinese based threat actors who is targeting government networks in China. Zegost uncovered back to 2011 since then attackers updated with various new functionalities
Multistage Attack Delivers BillGates/Setag Backdoor to Turn Elasticsearch Servers into DDoS Botnet
A new multistage attack exploiting Elasticsearch servers using the old unpatched vulnerability to invoke a shell with a crafted query and encoded Java commands. The attack aims to deliver BillGates/Setag Backdoor against vulnerable Elasticsearch servers. The attack targets the already