Archive
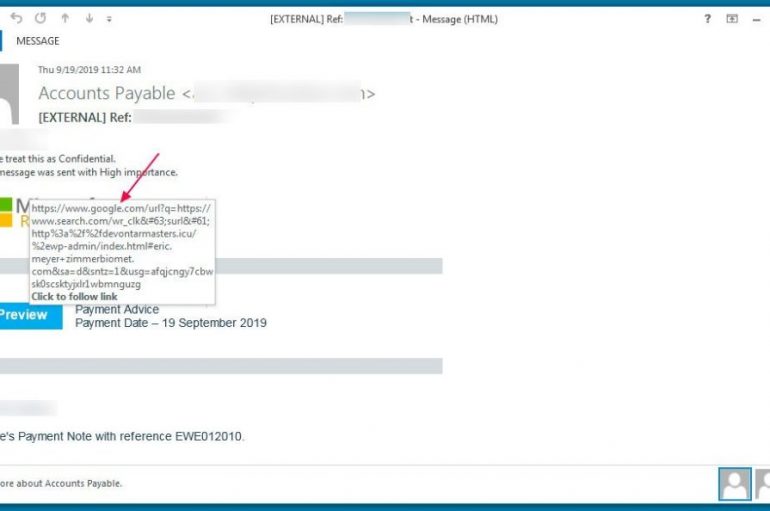
Experts reported that phishing campaigns are leveraging Google and Adobe open redirects to bypass spam filters and redirect users to malicious sites. Phishers are abusing Google and Adobe open redirects to bypass spam filters and redirect users to malicious sites.
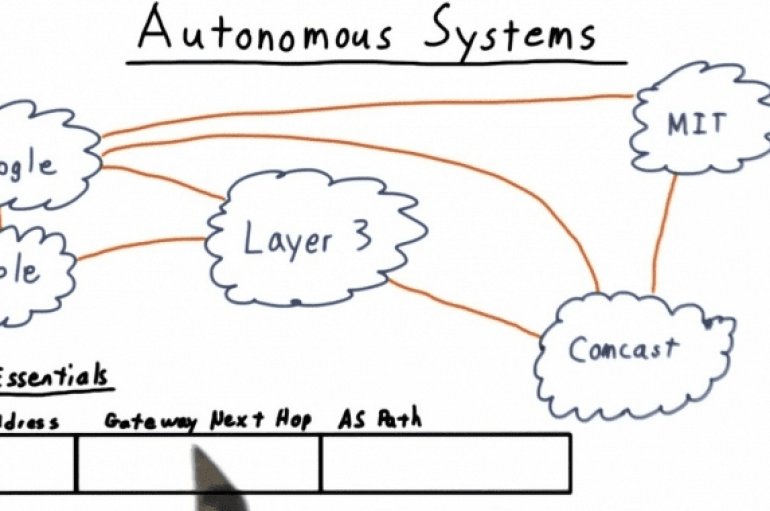
The ‘net’ in ‘internet’ stands for network. So technically it’s an internetwork–a network of computer networks. Are you confused yet? When we discuss routing, we refer to these independent computer networks as autonomous systems. A single autonomous system routes packets
Magecart Hackers Group Attack High-grade Wi-Fi Routers To Take Control The Public-WiFi Networks
A financially motivated hacking group called ” Magecart Group 5 (MG5) “targeting high-end commercial-grade layer 7 (L7) WiFi routers and take taking control over the public Wi-Fi networks that deployed in airports, casinos, hotels, and resorts. Threat actors initiate the
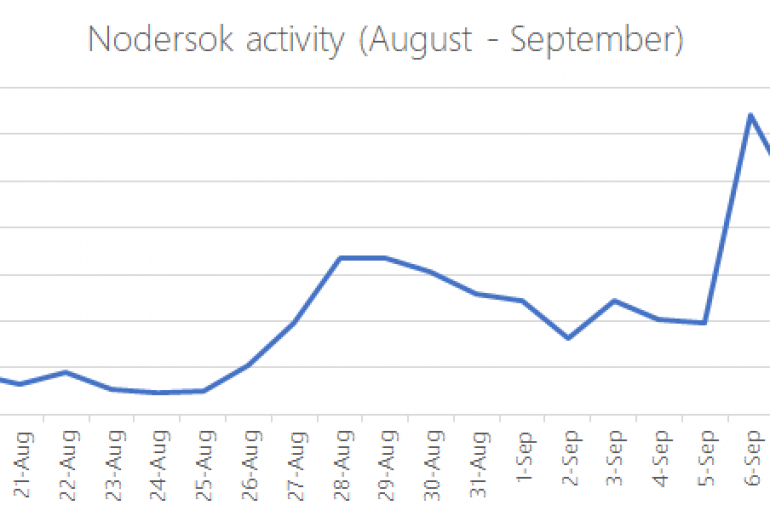
Microsoft researchers observed a campaign delivering malware, dubbed Nodersok, relying on advanced techniques and elusive network infrastructure. Microsoft experts observed a malware campaign, tracked as Nodersok, relying on advanced techniques and elusive network infrastructure. Microsoft uncovered the campaign in mid-July
Checkm8 – Hacker Published “Unpatchable”; Jailbreak for Millions of iOS Devices from iPhone 4S to iPhone X
An iOS security researcher with twitter handle Axi0mX released an Epic Jailbreaking tool dubbed Checkm8, exploit iOS device form iPhone 4S (A5 chip) to iPhone 8 and iPhone X (A11 chip). The tool is compatible with Mac and Linux and
PCI DSS Non-Compliance impacting the business in various ways and leads to a variety of consequences. PCI DSS is a set of information security standards for corporations that help safeguard payment card data from data loss, theft, or other accidents.
Dunkin’ Sued for Keeping Data Breach Secret
New York is suing Dunkin’ for allegedly failing to inform its customers of multiple cyber-attacks that compromised customer accounts. According to the lawsuit, filed in state Supreme Court in Manhattan, money was stolen by cyber-criminals, who hacked into the online
A new piece of spyware, designed to steal sensitive information from users of the messaging app Telegram, is for sale on the black market. Trojan-delivered Masad Stealer and Clipper was clocked by researchers at Juniper Threat Labs. The spyware uses
Global consumers overwhelmingly reject government arguments that encryption backdoors will make them safer from terrorists, according to new research from Venafi. The security vendor polled over 4100 consumers in the US, UK, France and Germany to better understand their attitudes
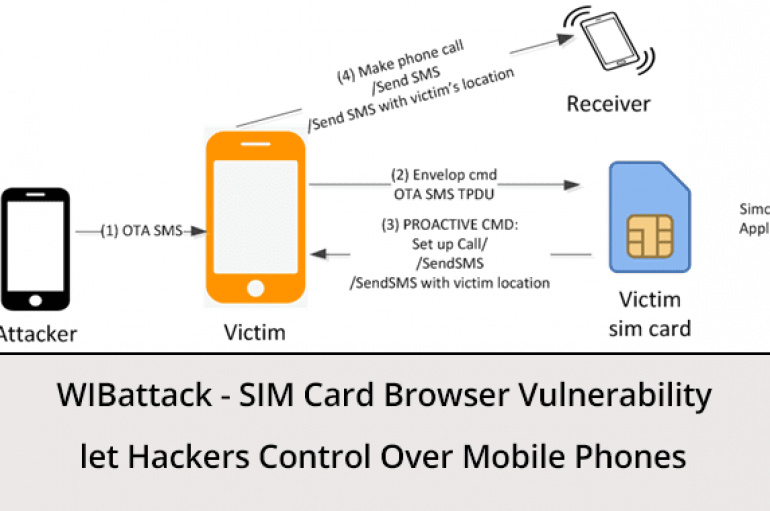
WIBattack – SIM Card Browser Bug Let Hackers Take Control Over Mobile Phones to Make Calls & SMS
The WIBattack vulnerability impacts hundreds of millions of telecom subscribers worldwide. The vulnerability comes from the sim card and it doesn’t depend on the mobile phone or the operating system. The vulnerability in WIB sim browser let hackers take control
REvil Ransomware links With GandCrab to Attack Windows Users via RDP Servers and Exploit kits
A financially motivated hacking group called “GOLD SOUTHFIELD” launch a newly developed REvil Ransomware (aka Sodinokibi) which is used the GandCrab ransomware code and infected the Windows users around the world. Threat actors distributing various medium including software installers with
Emsisoft security firm has released a new free decryption tool for the Avest ransomware, a few days after the release of WannaCryFake decryptor. Emsisoft security firm has released a new free decryption tool for the Avest ransomware, a few days
Experts are urging Thomas Cook customers not to respond to unsolicited messages in the wake of the UK travel company’s bankruptcy, as scammers are trying to harvest their bank details. The 178-year-old firm collapsed on Monday, leaving a GBP3bn black
Microsoft blocked 38 file extensions in Outlook web to prevent user’s from downloading attachments with those files extensions. Outlook contains built-in spam mail filter which prevents the junk mail getting into the inbox. Now Microsoft added 38 file extensions to
The daily war waged between cyber-criminals and security experts will be played out in miniature in Abu Dhabi next month using an accurate model of a real city. As part of the week-long HITB + Cyber Week security conference taking
Health Industry Cybersecurity Matrix Launched
America’s Healthcare and Public Health Sector Coordinating Council (HSCC) has launched an information-sharing resource aimed at improving the cybersecurity of the healthcare sector. The new Health Industry Cybersecurity Matrix of Information Sharing Organizations (HIC-MISO) helps users stay on top of