Posts From CCME
Data Sharing Critical to AI’s Use in Cybersecurity Strategies for enabling the effective use of AI technologies in cyber-defense were highlighted by a panel of experts during the RSAC 365 webinar ‘AI Meets Cybersecurity: Crossing the Streams and How to Manage the Dynamic
Cyber-Attack on Woodland Trust
Cyber-Attack on Woodland Trust A charity that protects and restores woodland in England, Northern Ireland, Scotland, and Wales has been targeted by a “sophisticated, high level” cyber-attack. According to a security incident notification published by the Woodland Trust on its website, attackers gained unauthorized
South Carolina Plans Cyber-Ecosystem
South Carolina Plans Cyber-Ecosystem The University of South Carolina (UofSC) has struck up a partnership with the Palmetto State to develop a statewide cyber-ecosystem aimed at making South Carolina a highly competitive player in the cyber-industry. The new alliance was announced Thursday,
Government Security Supplier Suffers Double Breach A French cybersecurity company with government clients revealed this week that an unauthorized third party has stolen customer data and some of its source code. Airbus subsidiary Stormshield counts the French government among its
Financial Regulator Hit by 240,000 Malicious Emails in Q4 2020 The UK’s financial regulator was bombarded with nearly a quarter of a million malicious emails in the final quarter of 2020, FOI data has revealed, highlighting the continuous pressure high-profile
Researchers from TIM’s Red Team Research (RTR) discovered 2 new zero-day vulnerabilities in WordPress Plugin Limit Login Attempts Reloaded Italy also joins the security bug research, with the Red Team Research laboratory of TIM, an important Italian telecommunications company. Among
HelpSystems Expands Cybersecurity Portfolio Through Latest Acquisition HelpSystems has announced a new acquisition to further boost its security product offerings. Cloud security company Digital Defense will join HelpSystems’ growing cybersecurity portfolio to enable customers to access a more comprehensive security
White Ops Acquired by Goldman Sachs
American cybersecurity company White Ops announced today that it has been acquired by Goldman Sachs’ Merchant Banking Division in partnership with ClearSky Security and NightDragon. Terms of the transaction, which follows Goldman Sachs’ and ClearSky’s initial investment in White Ops earlier this year, were not disclosed. The business was
SolarWinds Hackers Aimed to Access Victim Cloud Assets after deploying the Solorigate Backdoor
Microsoft security researchers have continued to investigate Solorigate which caused supply chain compromise and the subsequent compromise of cloud assets and have said that the ultimate ambition of the compromise was to pivot to the victims’ cloud assets after deploying
It’s safe to assume that pretty much everyone is ready to move on from 2020. Between the COVID-19 pandemic, political battles, and social unrest, this has been a stressful year in so many ways. It has also been a very active year for cybercriminals
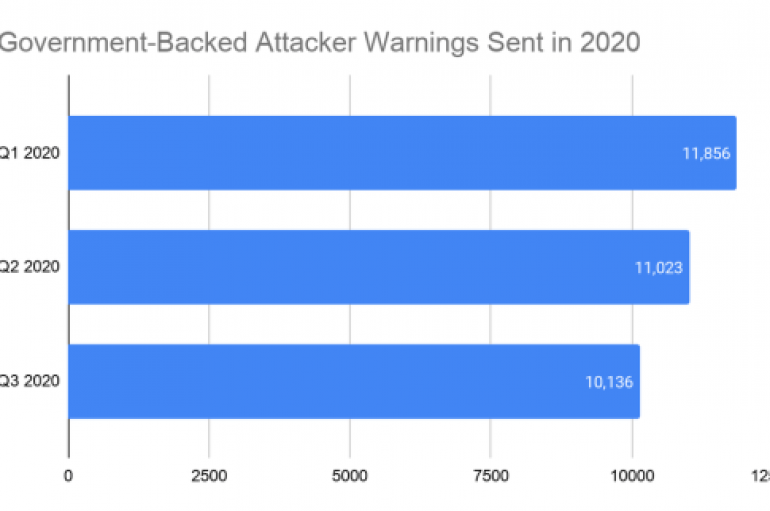
Google delivered over 33,000 alerts to its users during the first three quarters of 2020 to warn them of attacks from nation-state actors. Google delivered 33,015 alerts to its users during the first three quarters of 2020 to warn them
Spawn of Demonbot Attacks IoT Devices
Threat researchers have spotted a new kind of cyber-attack that uses a variant of Mirai malware to target a port used by IoT devices. The attack, orchestrated by someone using the alias “Priority,” was detected by a team at Juniper
Internal culture is a major determinant in how effective organizations’ cybersecurity practices and behaviors, according to a panel discussion at this week’s Digital Transformation Expo. They began by looking at how organizations can maintain a strong cybersecurity culture even while
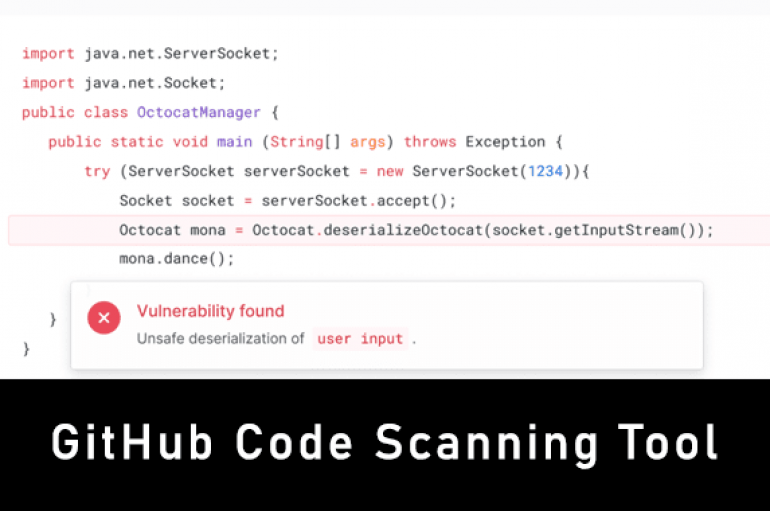
GitHub Launches Code Scanning Tool to Find Security Vulnerabilities – Available for All Users
GitHub launches a new code scanning tool that helps developers to detect vulnerability before the application reaches production. The tool was announced initially in May at the GitHub Satellite conference, since that time it is available for GitHub beta testers.
Researchers at an Israeli operational technology (OT) company have discovered multiple critical vulnerabilities in two popular industrial remote access software solutions. The flaws can be exploited to access industrial production floors, break into company networks, tamper with data, or steal