CCME BYTE
What is Spear Phishing Attack – A Complete Guide for Motives, Techniques & Prevention Methods
Each and Every day tens of thousands of Spear phishing emails are sending across the millions of victims around the
What is Deception Technology and Why Virtual Reality will be the Ultimate Weapon Against Cyberattacks
Development with technologies such as Deception Technology has become either a boon for cyber professionals or hackers, and this can
What is XSS (Cross Site Scripting) ? – A Detailed Understanding the Type of XSS
XSS is a very commonly exploited vulnerability type which is very widely spread and easily detectable and also it is
What is Network Security Key? How to Find it in Your Network – Router, OS, Mobile
A device’s network security key is a password or pass-phrase used to authenticate with a local area network (LAN). The
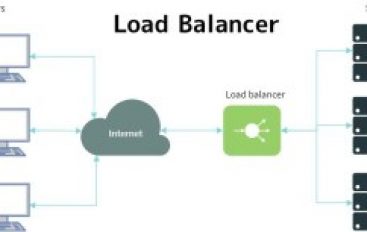
Load Balancer – How Does it Work With Reconnaissance Phase During Penetration Testing?
Load Balancer basically helps to distribute the network traffic across the multiple servers to improve the network, application performance. the
How to Perform Manual SQL Injection While Pentesting With Single quote Error Based Parenthesis Method
If you are trying to hack the databases with methods like single quotes error based injection, Integer based injection or
Web Application Penetration Testing Checklist – A Detailed Cheat Sheet
Web Application Pentesting is a method of identifying, analyzing and Report the vulnerabilities which are existing in the Web application
A Complete Penetration Testing & Hacking Tools List for Hackers & Security Professionals
Penetration testing & Hacking Tools Tools are more often used by security industries to test the vulnerabilities in network and