Posts From CCME
Avast spotted a new strain of Clipsa malware that is used to mine and steal cryptocurrencies along with carrying out brute-force attacks on WordPress sites. Clipsa is a malware that is well known to cyber security community is able to
Researchers at ESET have discovered malware-distributing spam campaigns targeting people in France. Dubbed Varenyky, the malicious payload comes with several dangerous functionalities. Not limited to the sending of spam, it can also steal passwords and even spy on victims’ screens
FireEye Identifies Prolific Chinese Cyber-Threat Group FireEye has identified a new advanced persistent threat (APT) group, dubbed APT41. As the firm explained in a blog post, APT41 is “a prolific Chinese cyber-threat group that carries out state-sponsored espionage activity in
Researchers Reveal 35 Flaws in Six Printers
Researchers Reveal 35 Flaws in Six Printers Researchers at NCC Group have uncovered 35 “significant” vulnerabilities in models from six popular enterprise printer brands. The risk mitigation consultancy tested kit produced by HP, Ricoh, Xerox, Lexmark, Kyocera and Brother –
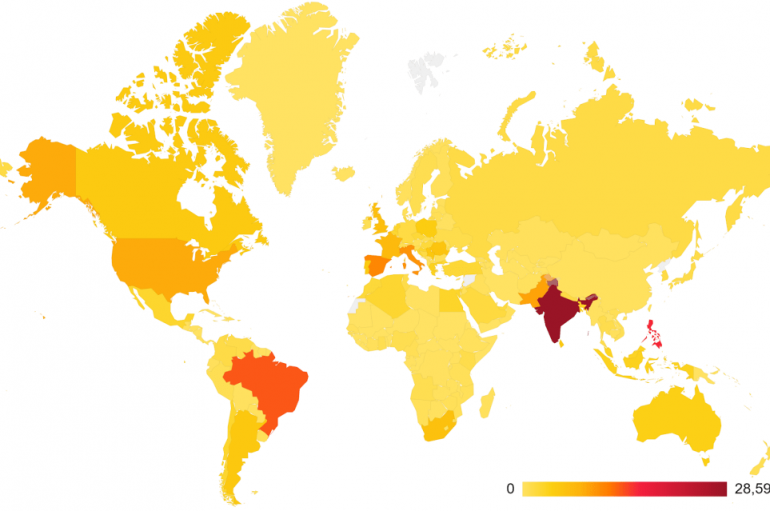
Northernmost Korean Hackers Amass $2bn Via Cyber-Attacks North Korean hackers have earned the Kim Jong-un regime in the region of $2bn after targeting banks and cryptocurrency exchanges, according to a new UN report. The effort was likely coordinated by the
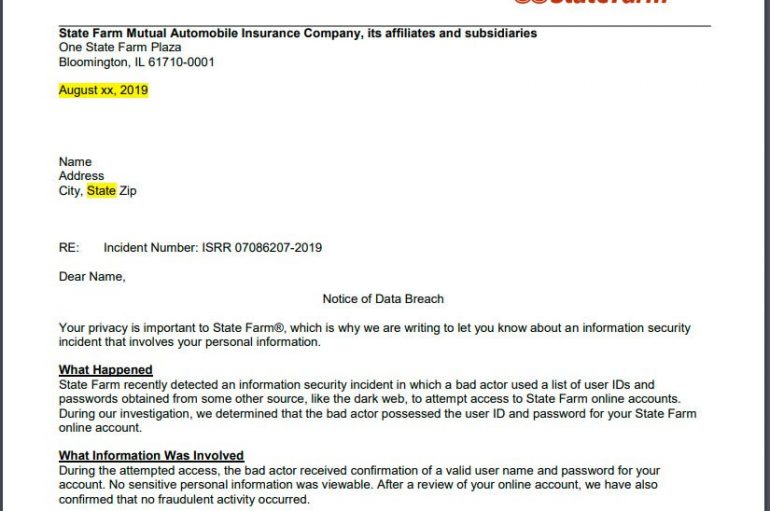
The American group of insurance and financial services companies State Farm disclosed a credential stuffing attack it has suffered in July. The American group of insurance and financial services companies State Farm revealed that it was the victim of a
A recruiter from AT&T charged in a 14-count, U.S to have a paid insiders to planting malware on telecommunications giant AT&T Network for committing unauthorized access and computer networks to unlock cellphones. Muhammad Fahd, 34, was arrested in Hong Kong
LokiBot Gets Sneakier With Steganography
LokiBot Gets Sneakier With Steganography The LokiBot malware continues to evolve and is now using steganography to cloak its malicious files, according to a report from Trend Micro this week. Recently highlighted as one of the top three malware strains
IBM’s Warshipping Attacks Wi-Fi Networks From Afar You’ve heard about wardriving, but what about warshipping? Researchers at IBM X-Force Red have detailed a new tactic that they say can break into victims’ Wi-Fi networks from far. The company calls the
Children’s Tablet Revealed Location, Researchers Found Researchers at the Black Hat security conference this week have revealed vulnerabilities in a leading child’s tablet product. The researchers, from security company Checkmarx, found several flaws in the LeapPad Ultimate, a rugged tablet
Over 50% of Enterprises Are Failing on Cloud Security Over half of organizations are struggling to protect their workloads, claiming the maturity of their security posture can’t keep up with the rapid pace of cloud adoption, according to Symantec. The
New Intel SWAPGS Flaw Spells Bad News for Users
New Intel SWAPGS Flaw Spells Bad News for Users Security researchers are warning of a new speculative execution vulnerability affecting all modern Intel processors which could allow attackers to access sensitive data stored in the kernel. The CVE-2019-1125 flaw bypasses
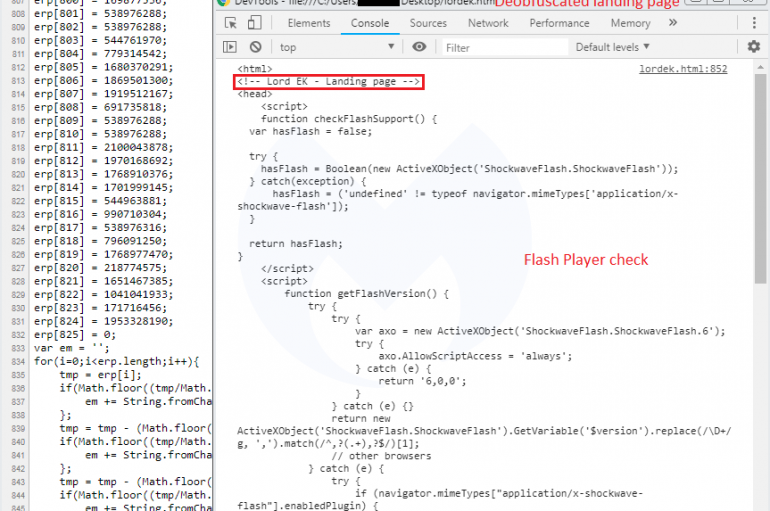
Security experts discovered a new exploit kit, dubbed Lord Exploit Kit, that is currently targeting vulnerable versions of Adobe Flash Player. Security experts at Malwarebytes have recently discovered a new exploit kit, dubbed Lord Exploit Kit, that is targeting vulnerable
QualPwn – Vulnerabilities in Qualcomm chips Allows Attackers to Compromise Android Devices Remotely
QualPwn, critical vulnerabilities in Qualcomm chips, that allows attackers to compromise Android device remotely over-the-air. The flaw resides in the Qualcomm’s Snapdragon WLAN component. The series of vulnerabilities dubbed QualPwn, discovered by Tencent Blade Team, the first two vulnerabilities reside
Preventing zero-day attack, one of a developer’s worst nightmares. In this guide, we’ll tackle the A to Zs of these attacks. Keeping your software bug-free and challenging to compromise is one of the biggest challenges that you will ever face
Microsoft, Apple Level Up Bounties
Microsoft, Apple Level Up Bounties Microsoft and Apple have both leveled up their bug bounty programs with new incentives for security researchers. Microsoft has doubled the top bounty reward for vulnerabilities in its Azure cloud software to $40,000. It also