New Strain of Clipsa Malware Launches Brute-force Attacks on WordPress Sites
Avast spotted a new strain of Clipsa malware that is used to mine and steal cryptocurrencies along with carrying out brute-force attacks on WordPress sites.
Clipsa is a malware that is well known to cyber security community is able to steal cryptocurrency via clipoard hijacking and mine cryptocurrency after installing a miner.
Avast recently discovered a new strain of Clipsa malware that is able to scan the Internet and launches brute-force attacks on WordPress sites.
“Avast researchers announced this week that the company has protected more than 253,000 users from Clipsa, a password stealer that steals administrator credentials from unsecured WordPress websites.” reads the blog post published by Avast.
“Once on an infected device, Clipsa can perform multiple actions, such as stealing cryptocurrency transfers and installing a cryptocurrency miner. Clipsa also uses infected PCs to crawl the internet for vulnerable WordPress websites. Once it finds a vulnerable site, it attempts to brute-force its way into the site.”
Anyway, the presence of the Clipsa malware is not difficult to notice because the malicious code may cause significant degradation of the PC’s performance due to the mining activity, as well as the crawling of the web for vulnerable WordPress sites.
The experts observed Clipsa spreading as a malicious executable file, for example, disguised as codec pack installers for media players.
The ability to launch brute-force attacks in unusual for a password stealer as explained by Jan Rubín, a malware researcher at Avast.
“Clipsa is an unusual password stealer, in that it supports a wide range of functionalities. Instead of just focusing on passwords and cryptowallets present on the victim’s computer, Clipsa also makes PCs do the cybercriminals’ dirty work, like searching for vulnerable WordPress websites on the internet and brute-forcing their credentials.” states Rubin. “The more machines that are infected, the more computational power Clipsa has,”
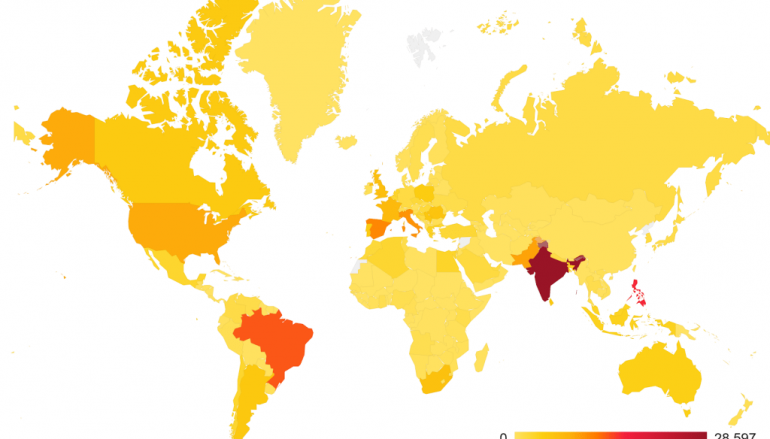
The campaign appears to be more active in India, where Avast has blocked the largest number of Clipsaattacks (over 43,000) against more than 28,000 users.

The higher number of infection was observed in the Philippines and in Brazil. Avast declared that it has protected more than 253,000 users since August 1, 2018.
Experts pointed out that it is rage to detect desktop malware launching brute-force attacks on WordPress sites, they believe the bad actors behind this campaign can steal further data from the hacked websites.
Avast researchers also believe that threat actors could use the compromised WordPress sites as secondary C&C servers to host download links for miners or to upload and store stolen data.
Clipsa was mainly developed to mine cryptocurrency and steal funds from the victims. It scans the victim’s PC wallet.dat files uploads them to a remote server, then use the content of the file to steal funds.
Clipsa also scans the PC for TXT files containing strings in the BIP-39 format used for storing Bitcoin mnemonic seed recovery phrases.
“Clipsa also focuses on text files that contain words with specific patterns. These patterns form bip-39 mnemonic seed recovery phrases (or “mnemonic word sequences”) which are used as a seed for a pseudo-random generator.” reads the analysis. “If a user knows the seed, they can deterministically generate the same wallet keys that were generated when the user first created their wallet. Thus, Clipsa in this phase actually focuses on stealing mnemonic word sequences to crack cryptocurrency wallets.”
As anticipated, Clipsa also monitor the clipboard to detect Bitcoin or Ethereum addresses and replace them with ones under the control of the attacker in the attempt of hijacking transactions.
Is this Clipsa campaign profitable?
Experts at Avast analyzed the balances of 9,412 Bitcoin addresses associated with Clipsa malware. The researchers discovered that operators earned a total of 3 Bitcoin stored in 117 of these addresses. This means that the profit for clipboard hijacking was about $35,000 per year.
Experts speculate that the crooks’ profits could be much greater if we consider funds gained by cracking the stolen wallet.dat files and the mining activity.
Avast published technical details about this campaign, including Indicators of Compromise (IoCs), here.
The post New strain of Clipsa malware launches brute-force attacks on WordPress sites appeared first on Security Affairs.