Posts From CCME
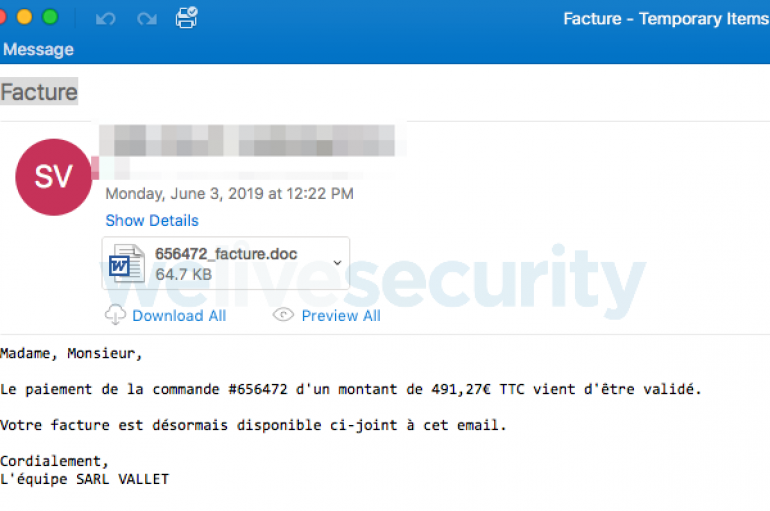
A new Spambot Trojan, tracked as Varenyky was spotted white targeting users as part of a new alleged sextortion campaign. The malware records the victim’s screen when they are visiting adult-related sites. Varenyky was discovered by researchers at ESET in
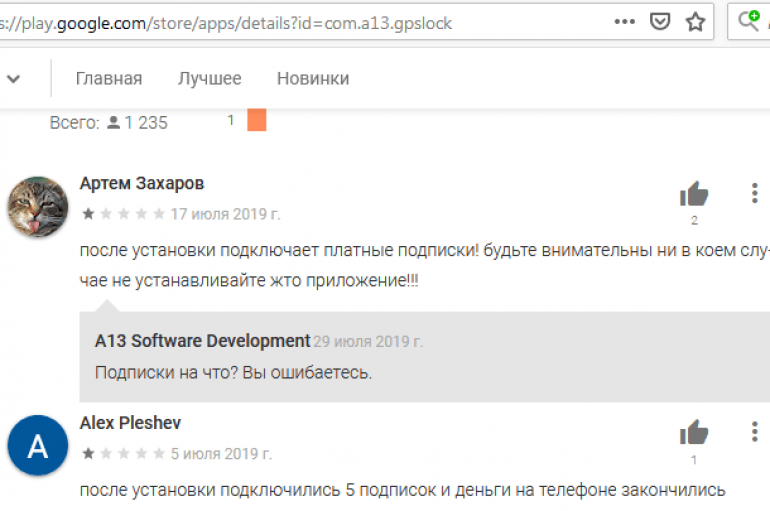
Experts at Dr Web discovered that a set of Android Apps with over 100 million installations that contains a clicker Trojan tracked as Android.Click.312.origin. Malware researchers at antivirus firm Dr Web discovered more than 33 Android Apps in the Google
Businesses that are growing are always trying to expand in all departments and to do that they need a website that portrays their business, customers, the value they generate and the positivity they deliver in their product. The Website being
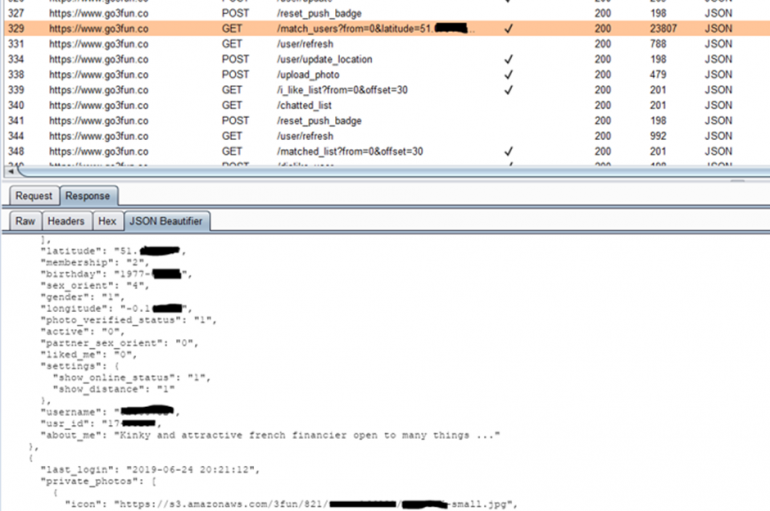
The 3Fun dating mobile app for “curious couples & singles” exposed the location of its members and their personal details. What do you think about the privacy of dating apps? Well, users of 3Fun, a mobile app for arranging threesomes
#dianainitiative2019: Certifications, Careers and Prohibitors for Women in Cybersecurity
Speaking on a panel at the Diana Initiative conference in Las Vegas, moderator Kathleen Smith, CMO of CyberSecJobs, asked the panelists about their careers, certifications and challenges. Saying that “no one has a straight path in the career,” Kathleen Smith
Apple’s $1 Million Bug Bounty Comes Under Fire
Apple’s decision to offer a $1m bug bounty has been criticized as potentially creating collusion opportunities and perverse incentives. According to The Verge, Apple announced that it has expanded its existing bug bounty program to include macOS, tvOS, watchOS and
Ransomware Soars 365% Year-on-Year in Q2
Ransomware Soars 365% Year-on-Year in Q2 Ransomware detections soared by 365% year-on-year in the second quarter of 2019, according to the latest report from Malwarebytes. This figure is even higher than the 235% increase in overall threats aimed at businesses
Broadcom Snaps Up Symantec Enterprise Security Biz For $10.7bn Symantec has announced the $10.7bn sale of its enterprise business to chip giant Broadcom, whilst cutting around 7% of its global workforce. The deal will see the Symantec name also taken
TfL Suspends Oyster Site After Credential Stuffing Blitz Transport for London (TfL) was forced to temporarily suspend the website for its Oyster system this week after an apparent credential stuffing attack on customers. The top-up card allows users to travel
Steam Windows Client Zero-day Privilege Escalation Vulnerability Affects Over 125 Million Users
The Steam windows client privilege escalation vulnerability allows an attacker with normal user privilege can run arbitrary code as an administrator. The Zero-day vulnerability was discovered by Vasily Kravets and the vulnerability resides in the Steam Client Service which was
Commando VM 2.0 – A New Version of Offensive PenTesting VM Updated With Kali Linux & New Hacking Tools
Commando VM 2.0, a new version of Windows-based security distribution released for penetration testing community and red teamers with updated hacking tools and new features such as Kali Linux, Docker containers. Earlier of 2019, FireEye released a Commando VM with
Warshipping is a new form of attack that counters the limitations with wardialing and wardriving techniques and improves the accuracy dramatically. An attacker could gain access to the system remotely from anywhere all they need is to ship a tiny
#BHUSA: How GDPR Can Help Attackers Steal Identities The GDPR (General Data Protection Regulation) is supposed to help individuals keep their information private, but as it turns out, it could also potentially serve to help attackers as well. In a
#BHUSA Scope of Russia’s Dark Web Revealed
#BHUSA Scope of Russia’s Dark Web Revealed Revealing new research around the Russian dark web, Ariel Ainhoren, research team leader at IntSights told Infosecurity that local websites to Russia were a “unique part of the dark web” due to local
At Black Hat Las Vegas on August 08 2019, Rebecca Lynch of Duo Security gave a talk on hiring, and just as importantly retaining, women in the cybersecurity industry. The statistics for gender diversity in the industry, Lynch pointed out,
In session at the Black Hat USA conference in Las Vegas, F5 Networks researchers outlined the challenges of morphing DDoS attacks and announced the release of a new open source tool called SODA in an effort to help test defenses