Posts From CCME
Weaponized iPhone Charging Cable Comes with Payload that Allow Hackers to Hijack Your Computer
An iPhone charging cable comes with preloaded payload, scripts, and commands that allows hackers to remotely open the terminal on Mac book screen and control the computer. The lightning cable looks like an ordinary that often used by iPhone users
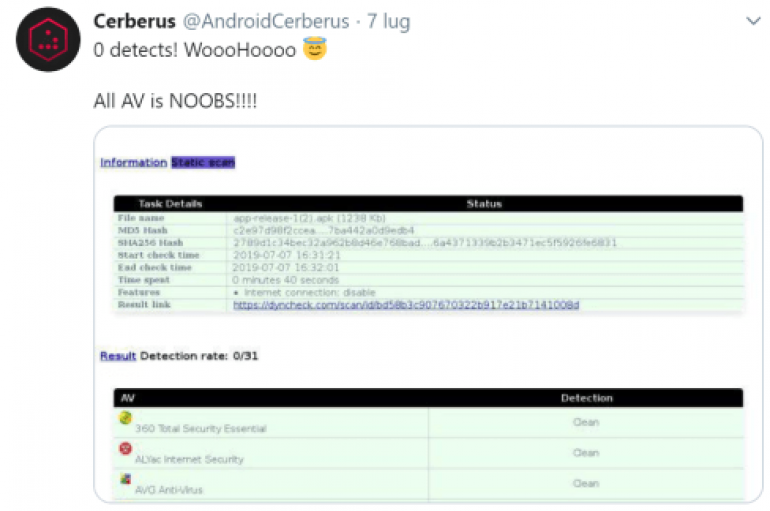
Security experts analyzed a new interesting Android banking Trojan, dubbed Cerberus, that is offered for rent by its author. A new malware-as-a-service dubbed Cerberus has emerged in the threat landscape, it is an Android RAT developed from scratch that doesn’t
Security researchers have warned organizations that unsolicited blank emails could be a warning sign they are being actively targeted by BEC scammers. Agari has been tracking professional BEC gangs such as London Blue, Scarlet Widow and Curious Orca for over
Industry stakeholders are considering reducing the lifespan of HTTPS certificates to just 13 months, around half of the current duration, in order to improve security. The CA/Browser Forum proposal would seek to make the changes from March 2020. It comes
Security expert discovered multiple flaws in 4G routers manufactured by several companies, some of them could allow attackers to take over the devices. G Richter, a security researcher at Pen Test Partners discovered multiple vulnerabilities 4G routers manufactured by different
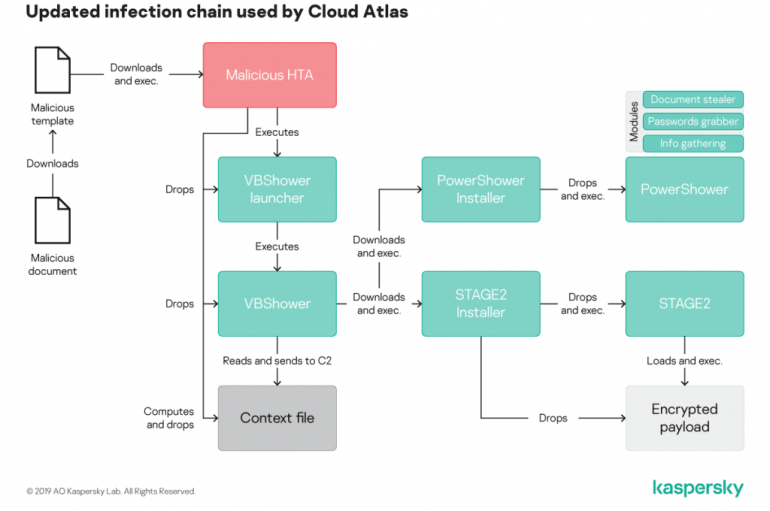
Cloud Atlas threat actors used a new piece of polymorphic malware in recent attacks against government organizations. The Cloud Atlas cyberespionage group, aka Inception, continues to carry out attacks against government organizations and was observed using a new piece of
Multiple Bugs in Canon DSLR Camera Let Hackers Infect with Ransomware Over a Rouge WiFi Access Point
Researchers discovered multiple critical vulnerabilities in Picture Transfer Protocol (PTP) that allows attackers to infect the Canon DSLR camera with ransomware to encrypt the pictures and demand the ransom. An attacker who is very close with the victim’s WiFi or
There are a lot of different risks to personal privacy, but one of the biggest could well be users themselves. In a session at the Crypto and Privacy Village within the DEF CON 27 conference in Las Vegas, Cat Murdock,
Security Experts Slam Group Hook-Up App
Security experts have uncovered major new vulnerabilities in a group hook-up app, exposing private pictures, real-time location and highly sensitive personal details. Security consultancy Pen Test Partners branded the 3fun app a “privacy train wreck,” claiming the privacy issues it
McAfee has announced the acquisition of cloud security start-up NanoSec in a move designed to help reduce container-related risk for its customers and accelerate DevSecOps. Cupertino-based NanoSec is described as a pioneer in simplifying app workload protection, with a zero-trust
The new version of Nmap 7.80 released in Defcon, Vegas by Gordon Fyodor, network security and created of Nmap. This new version of Nmap 7.80 upgraded with more than 80 new cross-platform improvements, fixed some of the critical bugs, added
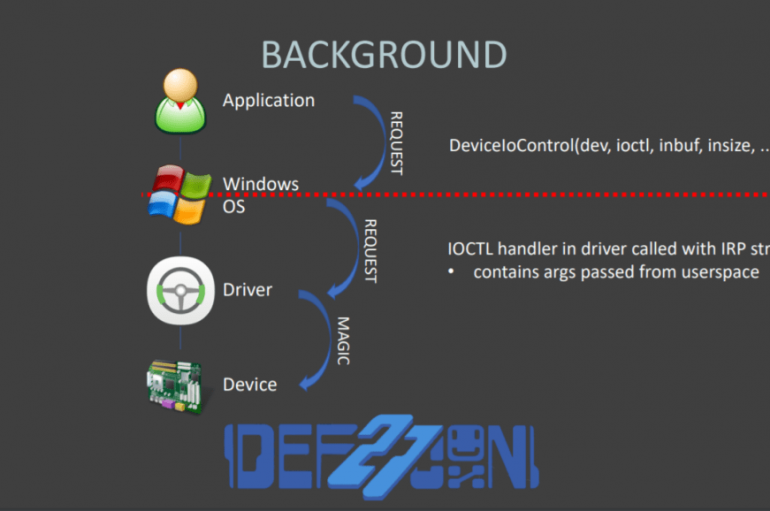
Researchers discovered multiple flaws in more than 40 device drivers from at least 20 different vendors that could to install a persistent backdoor on Windows PCs. Experts at firmware security firm Eclypsium have conducted a study on the device drivers
A group of Israeli researchers demonstrated that it is possible to take over the Simatic S7 controller one of the most secure controllers in the industry. A team of Israeli researchers demonstrated that it is possible to take control of
Apple expands its bug bounty program to cover all operating systems that include macOS, watchOS, tvOS, iPadOS, and iCloud along with the iOS bug bounty program. The tech giant has confirmed the expansion at Black Hat conference held in Las
New Clicker Trojan Found Installed in 100 Million Android Users Device From Google Play Store
A malicious module called Clicker Trojan installed on nearly 1000 million Android phones via Google play store apps such as audio players, barcode scanners, and other software. Threat actors intended to add this malicious clicker trojan to increase website visit
Security researchers at McAfee have discovered that a vulnerability patched ten years ago is still affecting several Avaya phones. Security experts at McAfee discovered that a stack-based buffer overflow flaw in the Dynamic Host Configuration Protocol (DHCP) client discovered and