New Lord Exploit Kit Appears in the Threat Landscape
Security experts discovered a new exploit kit, dubbed Lord Exploit Kit, that is currently targeting vulnerable versions of Adobe Flash Player.
Security experts at Malwarebytes have recently discovered a new exploit kit, dubbed Lord Exploit Kit, that is targeting vulnerable versions of Adobe Flash Player
The Lord Exploit Kit was first detected by Adrian Luca, researcher at Virus Bulletin, it was involved in a malvertising campaign leveraging the the PopCash ad network.
Is this actually a Exploit Kit? I’ve catched only first part.
popcash -> hxxp://liader[.]com[.]ua/ -> a page that look like a landing page named itself #LordEK and post back my flash version/ip/location. pic.twitter.com/BVxJJ5IiiX— Adrian Luca (@adrian__luca) August 1, 2019
“The first tweet from @adrian__luca about Lord EK came out in the morning of August 1st and shows interesting elements. It is part of a malvertising chain via the PopCash ad network and uses a compromised site to redirect to a landing page.” reads the analysis published by Malwarebytes.
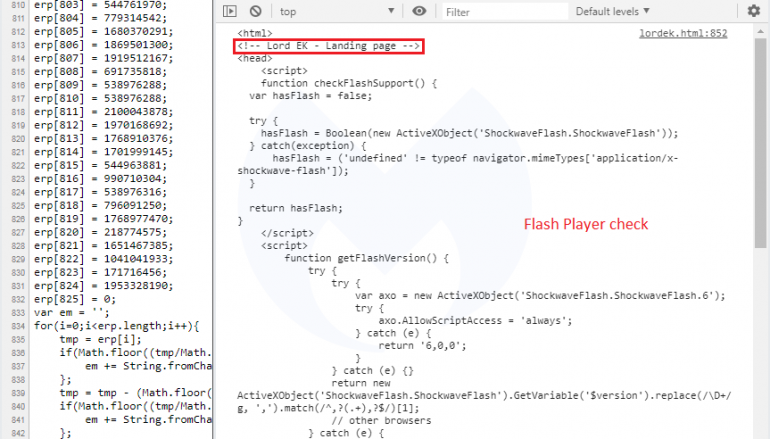
“We can see a very rudimentary landing page in clear text with a comment at the top left by its author that says: <!– Lord EK – Landing page –>. By the time we checked it, it had been obfuscated but remained essentially the same.”

The landing page used in the campaign involving the new EK was designed to check for the presence of Flash Player to trigger the CVE-2018-15982 flaw and gather system information.
The peculiarity of the Lord Exploit Kit is represented by the URLs it uses, they are very unusual and result from the adoption of the ngrok service to craft custom hostnames.
“This is rather unusual at least from what we have observed with exploit kits in recent history. As per ngrok’s documentation, it exposes a local server to the public internet.” continues the analysis “The free version of ngrok generates random subomains which is almost perfect (and reminds us of Domain Shadowing) for the exploit kit author,”
Once exploited the CVE-2018-15982 vulnerability, the Lord Exploit Kit launches shellcode to download and execute a payload. Experts initially observed the use of the EK to deliver the njRAT backdoor, but the operators behind this campaign rapidly switched to the ERIS ransomware.
Malwarebytes researchers also discovered that once exploited the flaw, the Lord exploit kit redirects the victim to the Google home page. This behavior was previously observed with the Spelevo exploit kit.
The Lord EK appears to be under active development, but it is difficult to predict how long it would be used by threat actors.
Malwarebytes also published Indicators of Compromise (IoCs) for the threat.
The post New Lord Exploit Kit appears in the threat landscape appeared first on Security Affairs.