Latest News
Hackers Exploiting Oracle WebLogic Zero-Day With New Ransomware To Encrypt User Data
Hackers exploiting the recently disclosed Oracle WebLogic Server remote code execution vulnerability to install a new variant of ransomware called
Most Important Cyber Incident Response Tools List for Ethical Hackers and Penetration Testers
Cyber Incident Response Tools are more often used by security industries to test the vulnerabilities and provide an emergency incident
Newly Emerging DDoS Botnet Attack on Electrum Takes 152,000 Hosts Under its Control
Newly Emerging DDoS botnet attack that targets one of the most popular bitcoin wallet Electrum and now it reaches the
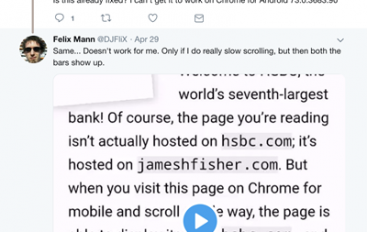
Developer Reveals Phishing Exploit in Chrome
In a proof-of-concept (PoC) blog post published earlier this week, developer James Fisher disclosed a new phishing method in Chrome
Norsk Hydro Estimates March Cyber Attack Cost at $50 Million
Aluminum producer Norsk Hydro estimated the cost of the massive attack cyber attack targeting the company in March at around
Saint Ambrose Catholic Parish – Crooks stole $1.75M in BEC Attack
Crooks have stolen $1.75 million in a church BEC (Business Email Compromise) attack, the victim is the Saint Ambrose Catholic
Hackers Exploiting SS7 Protocol & Inject ATM Malware to Attack Banks and Financial Sectors
The Banking and Financial sectors were hit with a constant stream of cyber attacks when compared to any of the
Credential Stuffing Costs Firms $4m Each Year
Credential stuffing attacks are costing EMEA businesses on average $4m each year, according to new research from Akamai. The content
ElectrumDoSMiner Botnet Reached 152,000 Hosts
Researchers at Malwarebytes are monitoring the evolution of the ElectrumDoSMiner DDoS botnet that reached 152,000 infected hosts. MalwareBytes researchers are
80 Million U.S Households Sensitive Personal Data Exposed Online From Unprotected Mystery Database
An unknown mystery database exposed nearly 80 million U.S households data that impacting up to 65% of US households. Security
How the Industrial Internet of Things (IIoT) Puts SCADA Systems at Risk
The Industrial Internet of Things (IIoT) is made up of interconnected sensors, instruments and other devices networked together with ICS/SCADA
How Does Cyber Threat Intelligence Benefits at Security Operation Centre Defense Phase
Cyber Threat intelligence is one of the most important concerns in the evolving threat environment of rapid day-zero attacks, cyber-criminality
Security Flaws in P2P Leave IoT Devices Vulnerable
Malicious actors could exploit critical security vulnerabilities in a peer-to-peer (P2P) communications technology used across millions of internet of things
FinServ Sees 60% Spike in Business Email Compromise
Financial services organizations are increasingly targeted by attackers using impostor emails attempting to commit fraud, according to the 2019 Email
Quantum Computing Technology and Its Benefit for Cybersecurity – A Complete Analysis
When We talking about Quantum Computing, Human Brilliance has now brought the computers a long way, and it’s completely different
Microsoft Removes Password-Expiration Policy in Security Baseline for Windows 10
Microsoft presented a series of security enhancements for its Windows 10, including the removal of the password-expiration policy. Microsoft announced