Archive
Credential Stuffing Costs Firms $4m Each Year
Credential stuffing attacks are costing EMEA businesses on average $4m each year, according to new research from Akamai. The content delivery firm commissioned the Ponemon Institute to interview 544 IT security professionals in the region who are familiar with these
ElectrumDoSMiner Botnet Reached 152,000 Hosts
Researchers at Malwarebytes are monitoring the evolution of the ElectrumDoSMiner DDoS botnet that reached 152,000 infected hosts. MalwareBytes researchers are closely monitoring attacks against users of the popular Electrum Bitcoin wallet, in particular, the evolution of the Electrum DDoS botnet.
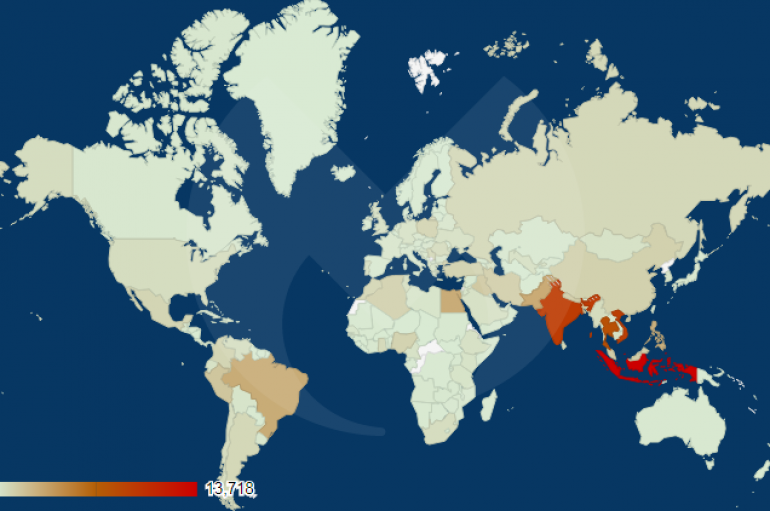
80 Million U.S Households Sensitive Personal Data Exposed Online From Unprotected Mystery Database
An unknown mystery database exposed nearly 80 million U.S households data that impacting up to 65% of US households. Security Researchers Noam Rotem and Ran Locar uncovered the 24 GB database which is hosted by a Microsoft cloud server. The
The Industrial Internet of Things (IIoT) is made up of interconnected sensors, instruments and other devices networked together with ICS/SCADA systems controlling water utilities, transportation systems, electric grids (the power grid) and other critical infrastructure systems. The Industrial Internet of
Cyber Threat intelligence is one of the most important concerns in the evolving threat environment of rapid day-zero attacks, cyber-criminality and espionage activities, the traditional approaches will be increasingly important to maintain, but will simply not be sufficient to properly
Malicious actors could exploit critical security vulnerabilities in a peer-to-peer (P2P) communications technology used across millions of internet of things (IoT) devices, according to research first reported by KrebsonSecurity. Security researcher Paul Marrapese initially reported the vulnerabilities to the device
Financial services organizations are increasingly targeted by attackers using impostor emails attempting to commit fraud, according to the 2019 Email Fraud in Financial Services report published by Proofpoint. The study analyzed more than 160 billion emails sent from 2017 to
When We talking about Quantum Computing, Human Brilliance has now brought the computers a long way, and it’s completely different from what it was when Charles Babbage invented it. With the evolution in technology, businesses are forced to enhance their
Microsoft presented a series of security enhancements for its Windows 10, including the removal of the password-expiration policy. Microsoft announced the removal of the password-expiration policy from its operating system starting with the next Windows 10 feature update (Windows 10
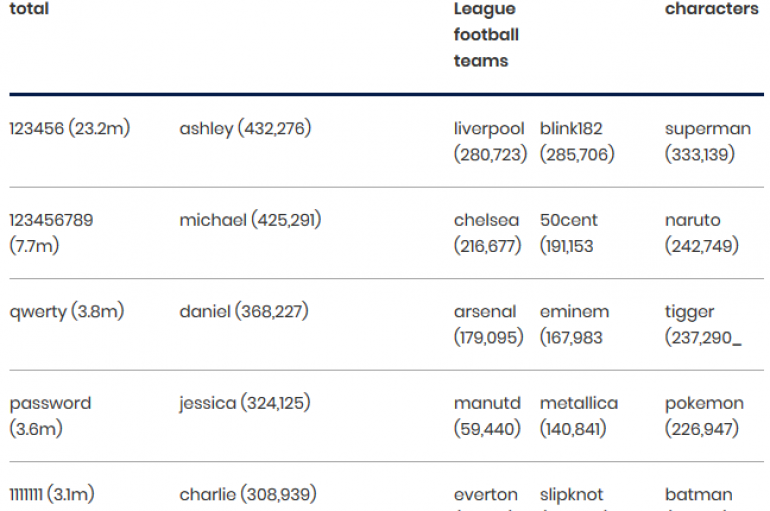
A cyber survey conducted by the United Kingdom’s National Cyber Security Centre (NCSC) revealed that ‘123456’ is still the most hacked password. Security experts at the United Kingdom’s National Cyber Security Centre (NCSC) analyzed the 100,000 most-commonly re-occurring breached passwords
Magecart Skimming Code Found on GitHub
Security experts are warning e-commerce site webmasters to be prepared for more Magecart attacks after spotting skimming code uploaded to a GitHub page. The hex-encoded piece of JavaScript code was uploaded on April 20 by user “momo33333,” who had joined
The Hong Kong office of Amnesty International has been hit by a long-running cyberattack carried out by China-linked hackers. Amnesty International’s Hong Kong office has been hit with a cyberattack launched by China-linked hackers. “This sophisticated cyber-attack underscores the dangers
US NIST updates its Automated Combinatorial Testing for Software (ACTS) research toolkit that should help experts in finding bugs in complex safety-critical applications. US NIST announced updated for its Automated Combinatorial Testing for Software (ACTS) research toolkit that should allow
Parrot Security OS 4.6 Released with New Updates for Hacking Tools & Important Vulnerability Fixes
Parrot 4.6 Released by Parrot security with so many updates that bring all the hacking tools on the table with new futures and important bug fixes for the various vulnerabilities that affected the Parrot security OS and Linux kernel. The
Experts observed several malspam campaigns using signed emails to deliver the GootKit banking Trojan (aka talalpek or Xswkit). Threat actors leverage a multi-stage malware loader tracked as JasperLoader in the malspam campaigns over the past few months. The JasperLoader was
Most Important Data Protection Policies to Keeping Your Personal, Official, Financial Data Safe
The recent compromise of Facebook privacy has caused ripples of fear as to whether any data can be safe. Yes. You can make your data safe anytime you choose to employ the right way. Discover the different options that will