Latest News
Hackers Abuse GitHub Service to Host Variety of Phishing Kits to Steal Login Credentials
Hackers abuse popular code repositories service such as GitHub to host a variety of phishing domains to make their targets
Special-Purpose Vehicle Maker Aebi Schmidt Hit by Malware
The special-purpose vehicle maker Aebi Schmidt was hit by a malware attack that disrupted some of its operations. The Aebi
Attacks on Businesses Soar 235% in Q1
A surge in ransomware and trojans in the first three months of the year led to a massive 235% year-on-year
#CYBERUK19: NCSC and ICO Clarify Roles to Assist Incident Response
The UK’s National Cyber Security Centre (NCSC) and regulator the Information Commissioner’s Office (ICO) have agreed to clarify their roles
Emotet Malware’s New Evasion Technique Lets Hacked Device Used as Proxy command and control (C&C) servers
A new wave of Emotet malware using a special type of evasion technique to fool the security software and hide
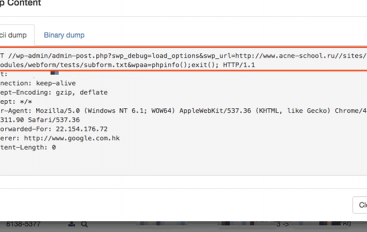
Flaws in Social Warfare Plugin Actively Exploited in the Wild
Experts uncovered hacking campaigns exploiting two critical security vulnerabilities in the popular WordPress plugin Social Warfare. Social Warfare is a
ASUS Not Alone in ShadowHammer Supply Chain Attack
Researchers believe that in last month’s malware attack, dubbed Operation ShadowHammer, the network of Taiwanese technology giant ASUS was not
Hackers Behind DNSpionage Created a New Remote Admin Tool for C2 Server Communication Over HTTP and DNS
Threat actors behind the new malware campaign DNSpionage created a new remote administrative tool that supports HTTP and DNS communication
Hackers Abuse Windows Installer MSI to Execute Malicious JavaScript, VBScript, PowerShell Scripts to Drop Malware
Hackers use malicious MSI files that download and execute malicious files that could bypass traditional security solutions. The dropped malware
Report: 42% of Used Drives Sold on eBay Hold Sensitive Data
A new report from Blancco Technology Group has warned that those looking to make some money by selling used storage
Unpatched Oracle Web Logic Server Zero-day Let Hackers Executes Arbitrary Code Remotely & Gain Network Access
New Zero-day flaw discovered in Oracle Web logic server let attackers exploit this vulnerability to remotely execute commands without authorization.
Insider Threats a Top Risk to Healthcare
Across the healthcare sector, ransomware is reportedly no longer the most prevalent security threat, according to new research from Vectra
Hackers Hosting Malware On Google Sites To Steal Data and Share It to the Remote Server
Cybercriminals abusing Google sites via drive-by download attack to host dubbed “LoadPCBanker” banking malware to steal various sensitive data from compromised
Stuart City is the New vVictim of the Ryuk Ransomware
Another city fell victim of a malware attack, systems at the city of Stuart, Fla., were infected by the Ryuk
Online Fitness Store Gets One-Upped by Hackers
Lifting weights might build strength for the body, but for customers of Bodybuilding.com, bulking up wasn’t enough to stop hackers
50 Malicious Android Apps Bypassed Google Play Protection and Infected 30 Million Android Users
More than 50 malicious apps with more than 30 Million installations found on Google play, that display annoying ads and