Posts From CCME
Operating Systems can be detected using Ping Command, Ping is a computer network administration software utility, which used to find the Availability of a host on an Internet Protocol (IP) network. Ping operates by sending Internet Control Message Protocol (ICMP)
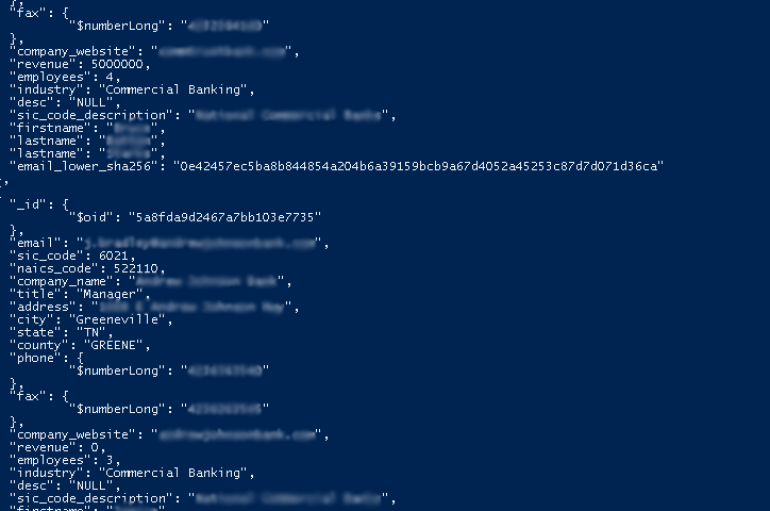
Experts found an unprotected server exposing online 4 MongoDB databases belonging to the email validation company Verifications.io. A new mega data leak made the headlines, an unprotected MongoDB database (150GB) belonging to a marketing company exposed up to 809 million
Deep Web Search Engine is an alternative search engine when we need to search something, then Google or Bing will the first choice hit in mind suddenly. But unlike the Deep Web Search Engine, Google and Bing will not give
Hackers Purchasing Abused SSL/TLS certificates From Dark Web Markets to Victimize their Targets
SSL/TLS certificates are the backbones of secure communication, it encrypts the sensitive information that sent across the internet, so that, only the intended recipients can get access to it. The SSL/TLS certificates provides trust with lock icon and also provides
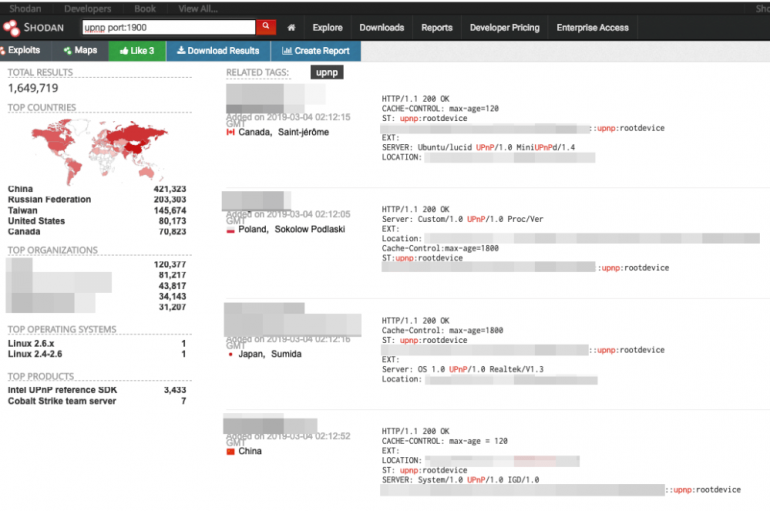
UPnP-enabled devices running outdated software are exposed to a wide range of attacks exploiting known flaws in UPnP libraries. A broad range of UPnP-enabled devices running outdated software are exposed to attacks exploiting known flaws in UPnP libraries, Tony Yang,
Researchers discovered the 150GB volume of biggest and most comprehensive email unprotected MongoDB that leaked 800 Million Email data online that belongs to Verifications.io. The leaked email contains sensitive information including personally identifiable information (PII) and the complete data being
Best Operating system for Ethical Hacking and Penetration Testing with Linux is the best option for every Security Researcher or Ethical Hacker. Here is the list of Top 10 Penetration Testing & Ethical Hacking Linux 2019. Linux is open source
Massive Ryuk Ransomware Attack on Entire Computers of Jackson County, Georgia – $400,000 Ransom Paid
Rural Jackson County, Georgia computer systems are infected with Massive Ryuk ransomware attack that leads to shut down all the operations. Since there is no way to recover the files back without the decryption key, officials paid $400,000 as a
Lynis is an open source security auditing tool. Its main goal is to audit and harden Unix and Linux based systems. It scans the system by performing many security control checks. Examples include searching for installed software and determine possible
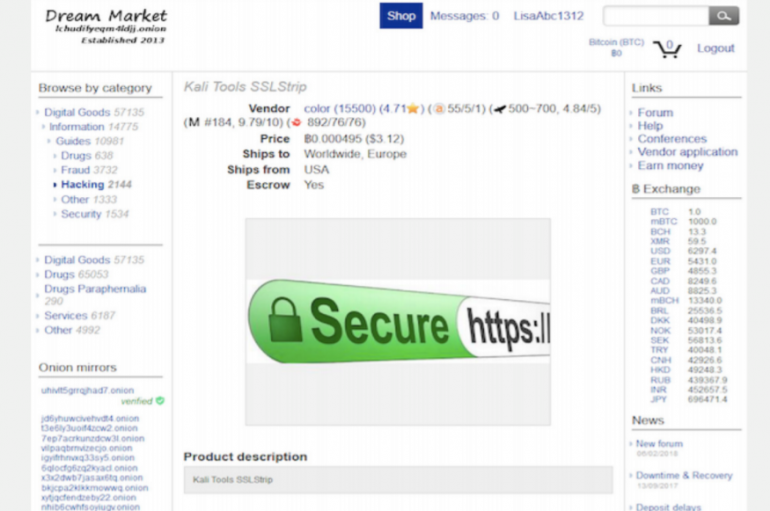
A study conducted by academics discovered that SSL and TLS certificates and associated services can be easily acquired from dark web marketplaces. A study sponsored by Venafi and conducted by researchers from Georgia State University in the U.S. and the
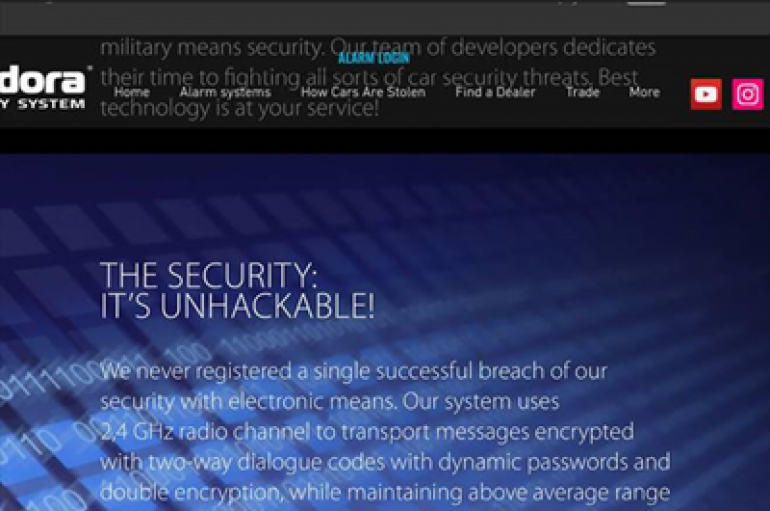
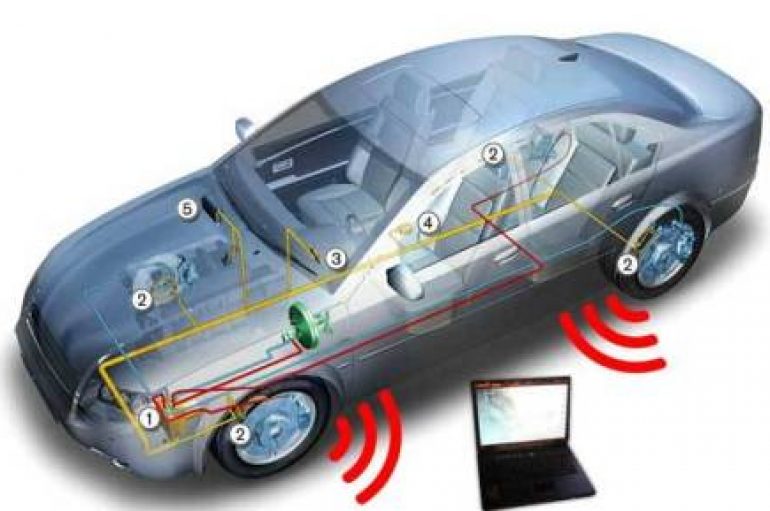
Researchers at Pen Test Partners revealed in a proof of concept (PoC) that they were able to exploit vulnerabilities in two high-end “smart” alarms. In their PoC, the pen testers debunked third-party car alarm vendors’ claim to be the solution
Reconnaissance is a process to get information in-depth about the target. Keep gathering information until penetration testing phase is a bit difficult. Here we have a Python script called TIDOS which helps Hackers or Penetration testers. This toolkit will gather
Security experts at Pen Test Partners discovered several vulnerabilities in two smart car alarm systems put three million vehicles globally at risk of hack. The flaws could be exploited by attackers to disable the alarm, as well as track and
10 Best Free SSL Checker For 2019, to Check for Certificate Installation and Vulnerabilities
SSL Checker helps you in troubleshooting the common SSL issues and the SSL endpoint vulnerabilities. With the SSL checker, just you need to submit the domain name or IP address along with the port number to analyze the configuration and
Web Application Pentesting is a method of identifying, analyzing and Report the vulnerabilities which are existing in the Web application including buffer overflow, input validation, code Execution, Bypass Authentication, SQL Injection, CSRF, Cross-site scripting in the target web Application which
Security experts at Symantec linked the massive Singapore Healthcare breach suffered by SingHealth to the ‘Whitefly’ cyberespionage group. In 2018, the largest healthcare group in Singapore, SingHealth, has suffered a massive data breach that exposed personal information of 1.5 million