Posts From CCME
StealthWorker Brute-force Malware Attack on Windows & Linux Platform Via Hacked E-commerce Websites
Researchers discovered a new brute-force malware called StealthWorker that attack Windows & Linux platform via compromised E-commerce websites to steals personal information and payment data. This Stealthy malware written in Golang language which is very rarely used by malware authors
Organizations are still failing to put in place the appropriate internal auditing and incident response measures necessary to comply with General Data Protection Regulation (GDPR) rules, according to a new report from the Information Commissioner’s Office (ICO). The UK’s data
The average cost of cybercrime rose by over $1m last year to reach $13m per firm, with the impact of malicious insiders particularly noticeable, according to a new Accenture report. The consulting giant’s annual Cost of Cybercrime report is compiled
Phishing Attacks Spiked by 250% in 2018
A new report from Microsoft found that phishing attacks increased 250% over the course of 2018. According to Microsoft’s Security Intelligence Report (SIR) volume 24, attackers have shifted tactics and are now targeting multiple points of attacks within one campaign.
Strong passwords are to protect your devices, online banking accounts and other data sources from unauthorized access. In this article, we highlight the Best Free Password Manager available. If you have a weak password then it is a cake walk
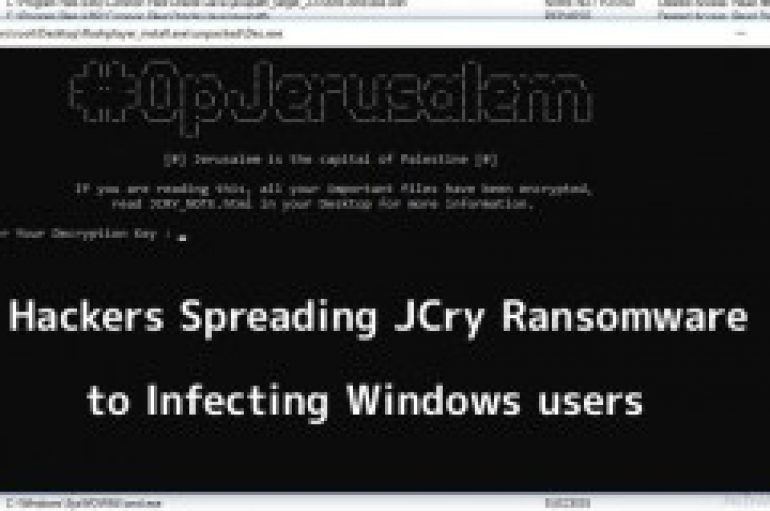
Cyber criminals spreading new ransomware called Jcry which is written in Go language via #OpJerusalem2019 campaign that attack Windows users to encrypt the file and demand the ransom. #OpJerusalem2019 is recently launched a cyber attack against the Israeli Government and
Researchers have uncovered a thriving underground market in TLS certificates sold on their own and packaged with crimeware to help launch a range of attacks. Sponsored by Venafi, the SSL/TLS Certificates and Their Prevalence on the Dark Web report was
Businesses Go Passwordless into Cloud Security
Security and risk management leaders are looking to better understand the link between risk and business goals, according to Gartner. In its newly released list of the top seven security and risk management trends for 2019, Gartner identified the ongoing
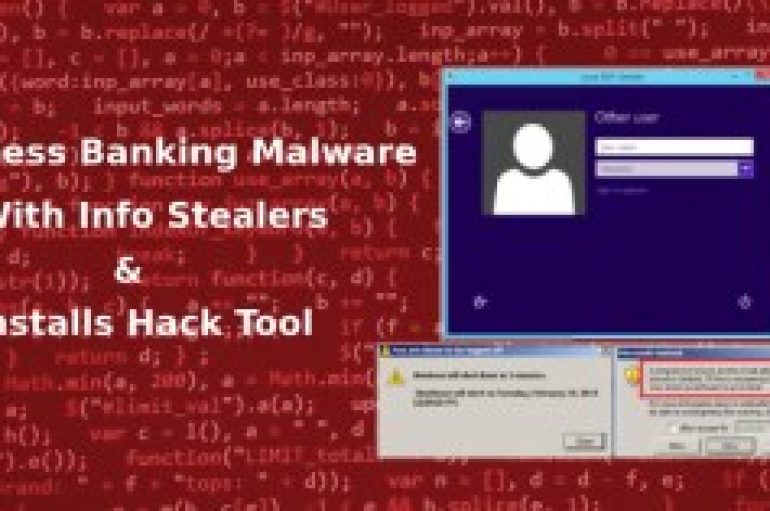
Fileless Banking Malware Steals User Credentials, Outlook Contacts, and Installs Hacking Tool
A new malware campaign focuses on stealing online banking credentials, to gather business email address and to gains remote access to the victim machine. According to TrendMicro analysis, the fileless banking malware with multiple .BAT attachments is capable of establishing
BEC, cryptojacking, phishing and fileless malware attacks all surged in 2018 as cyber-criminals increasingly moved away from one-size-fits-all approaches, according to Trend Micro. The security vendor’s 2018 roundup report, Caught in the Net: Unraveling the Tangle of Old and New
Privileged Credential Abuse a Top Attack Vector
Attackers are increasingly finding success using compromised privileged credentials to breach organizations, according to a new survey from Centrify. In a survey of 1,000 IT decision-makers in the US and the UK, 74% of those organizations that have experienced a
When returns on ransomware and cryptojacking started to decline, cyber-criminals had to get creative with alternative methods of making money, according to Symantec‘s newly released Internet Security Threat Report. The report found that, on average, 4,800 websites were compromised with
Ultrasounds Lack Ultra Security, Research Shows
Ultrasound technology using an outdated operating system is vulnerable to attack, according to new research from Check Point. In a video demonstration, researchers revealed that connected ultrasound machines running Windows 2000 are able to be exploited. Because the Windows 2000
Emergency !! Hackers Exploited Active Google Chrome Zero-day in Wide – Update Chrome Now
Google announced an emergency warning about active Google Chrome zero-day vulnerability that exploited in wide and urged users to update the chrome immediately. Currently, the exploit is rapidly used by hackers and they continue to compromise Google Chrome users to
#RSAC: Rethinking Third-Party Risk Management
Todd Inskeep, principal, cyber security strategy with Booz Allen Hamilton, began his RSA Conference 2019 talk with a picture of a three-legged race because it represented the relationship necessary to win. It worked as a perfect metaphor for third-party risk
Despite a proliferation of security tools, breaches continue to happen. Best of breed isn’t working, so organizations need to rethink their approach to deploying cybersecurity products, said Matthew Chiodi, chief security officer, public cloud and Sandra Wenzel, sr systems engineer,