Posts From CCME
Facebook Fixed, but Did Outage Hurt Trust?
Amid widespread speculation that a cyber-attack caused the outage of Facebook‘s services earlier this week, the social media platform contends that the issue was the result of a server configuration change. Despite the array of questions about when it made
The data breach at Wolverine Solutions Group (WSG) continues to plague the healthcare industry, with more organizations, including Spectrum Healthcare, sending security notices to customers. As was the case for many organizations who have already issued security notices, Spectrum said
In the wake of the New Zealand mosque shooting, the CISA recommends users to remain vigilant on possible scams and malware attacks. Yesterday the horrible mass mosque shooting in New Zealand made the headlines, fifty people were killed. A gunman
E-Com Site Gearbest Exposed Millions of Records
Researchers at vpnMentor have discovered a security vulnerability in Gearbest, a Chinese e-commerce business that reportedly processes hundreds of thousands of sales a day. According to a blog post from vpnMentor’s research team, hackers were able to access different parts
What is an Indicator of Attack (IOA) IoAs is some events that could reveal an active attack before indicators of compromise become visible. Use of IoAs provides a way to shift from reactive cleanup/recovery to a proactive mode, where attackers
SimBad, a massive adware campaign discovered in Google playstore from more than 200 malicious apps that have been downloaded by nearly 150 million times. Most of the Infected Malicious apps are belongs to simulator games category and these apps creating
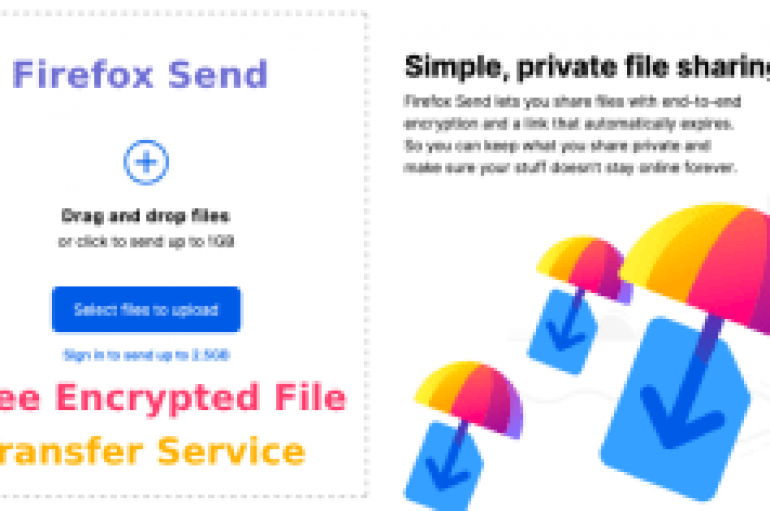
Firefox Send – Free Encrypted File Transfer Service to Share Your Personal Information Securely
Mozilla launched it’s free encrypted file transfer service Firefox Send that allows users to share the files simply and securely from any browsers. You can send files up to 2.5GB by having a Firefox account, else you upload files up
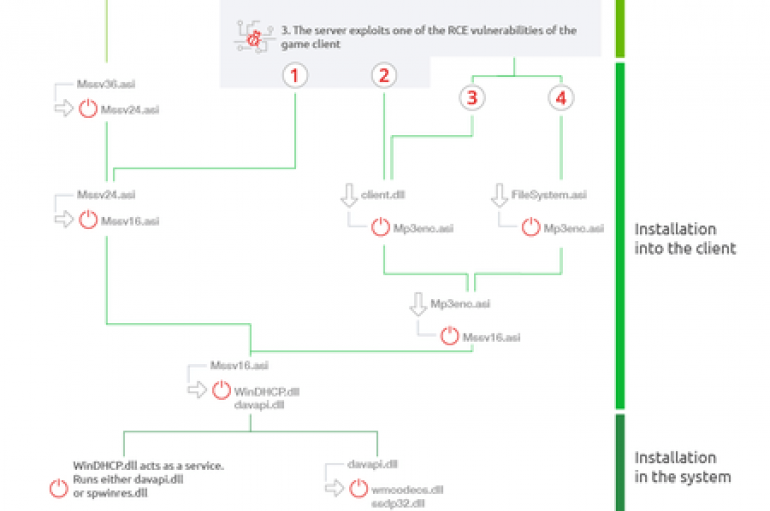
Experts at security firm Dr. Web revealed that 39% of all existing Counter-Strike 1.6 game servers online are malicious, an attacker is exploiting zero-day flaws in game clients. Bad news for gamers of the popular game Counter-Strike, according to the
Researchers have discovered a new crypto-mining campaign targeting Elasticsearch instances which contains sinkholing capabilities to squash any competing miners. The aptly named “CryptoSink” malware campaign exploits an Elasticsearch vulnerability from 2014 (CVE-2014-3120) to mine cryptocurrency in Windows and Linux environments,
Orgs Say Yes to AI Use But Ask ‘What Is It?’
Organizations across the US and Japan have plans to increase their use of artificial intelligence (AI) and machine learning (ML) this year, yet many don’t really understand the technology, according to a new report from Webroot. A survey of 400
Fraudsters Band Together, Shift to Bot Attacks
Fraudsters are joining together to create fraud rings, sharing knowledge with each other and leveraging automation to attack at scale, according to a new report from Forter. Forter’s latest Fraud Attack Index found that attackers have been increasingly targeting e-commerce
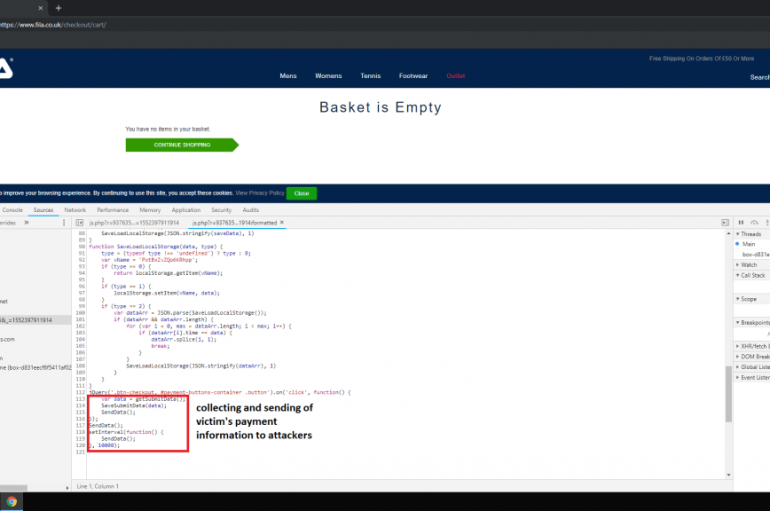
Payment Data of Thousands of Customers of UK and US Online Stores could have been Compromised
Group-IB, an international company that specializes in preventing cyberattacks, has uncovered a malicious code designed to steal customers’ payment data on seven online stores in the UK and the US. The injected code has been identified as a new JavaScript
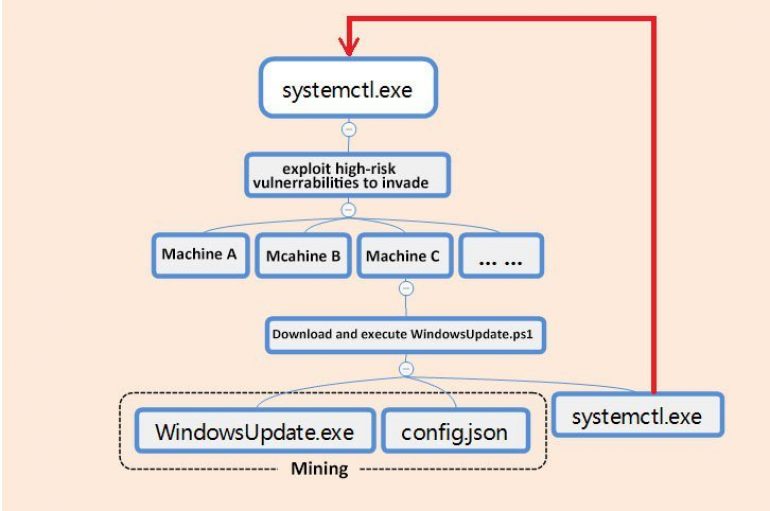
Security experts at 360 Total Security have discovered a new modular cryptocurrency malware that implements worm capabilities to spread. Security experts at 360 Total Security have discovered a new modular cryptocurrency malware that implements worm capabilities by leveraging known vulnerabilities
A new malspam campaign pushes Emotet banking malware along with Qakbot as the follow-up malware. The Emotet is a banking trojan that has the capabilities to steal personal information such as the username and the passwords. Security researcher Brad Duncan
March Patch Tuesday Fixes Two Zero Days
Microsoft has patched over 60 vulnerabilities this month, two of which are being exploited in the wild and four of which were previously disclosed. The two Windows flaws being used to attack targets are elevation of privilege bugs CVE-2019-0797 and
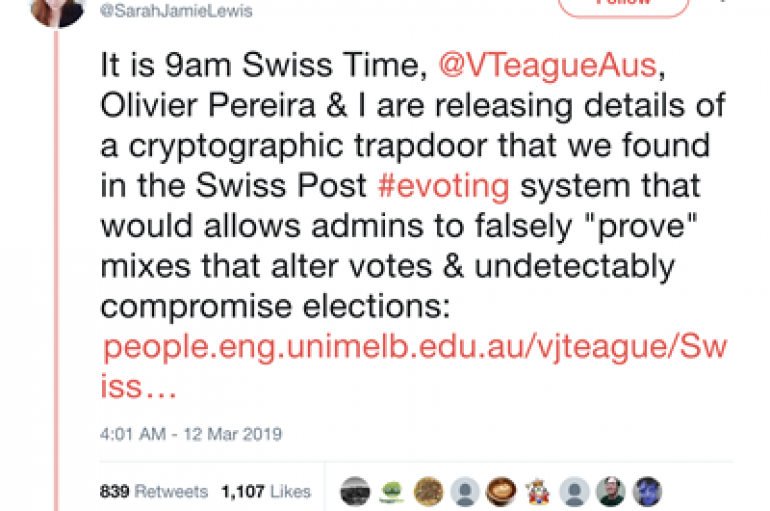
Source Code Error in Swiss Post E-Voting System
A group of international researchers at the University of Melbourne discovered a flaw in the Swiss Post e-voting system that had also been independently discovered by Thomas Haines of NTNU and by Rolf Haenni of Bern University of Applied Sciences.