Posts From CCME
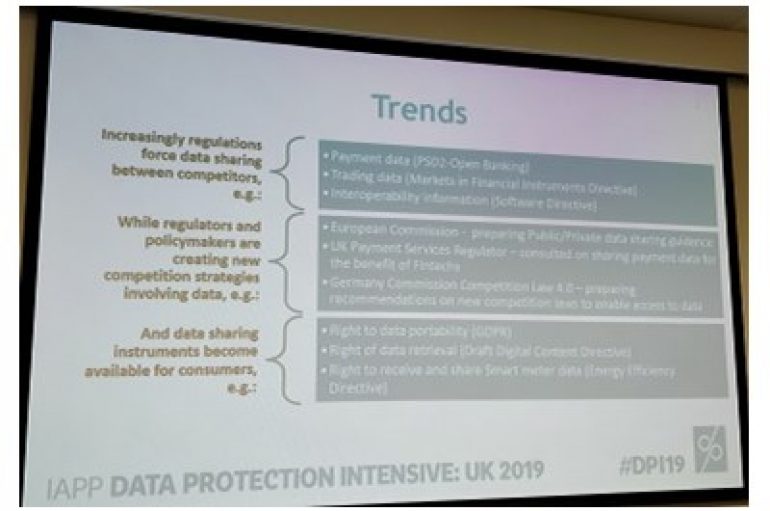
Speaking at the IAPP Data Protection Intensive 2019 conference in London on ‘How Privacy & Data Protection are Impacted by Competition Considerations,’ Helena Koning, senior managing counsel and data protection officer at Mastercard, said that new rules on open banking
Speaking at the IAPP Data Protection Intensive 2019 conference in London, panel moderator Kabir Barday, CEO of OneTrust, asked “How the UK’s Data Protection Act 2018 Impacts Your GDPR Programme.” Julie Varcoe-Cocks, head of ethics, regulatory and compliance and data
Over one million digital certificates have been mis-issued by Google, Apple and GoDaddy after an operational snafu left them non-compliant with industry standards. Researcher Adam Caudill revealed the issue late last week, claiming that the companies had misconfigured the EJBCA
Adobe Releases Security Updates that Fixes Critical Vulnerabilities with Photoshop CC and Digital Editions
Adobe released security updates for the month of March 2019, that covers critical vulnerabilities with Adobe Photoshop CC and Adobe Digital Editions. Successful exploitation of these vulnerabilities allows an attacker to run the arbitary code with the context of the
Advanced ATM Penetration Testing Methods
ATM Penetration testing, Hackers have found different approaches to hack into the ATM machines. Programmers are not restricting themselves to physical assaults, for example, money/card catching, skimming, and so forth they are investigating better approaches to hack ATM programming. An
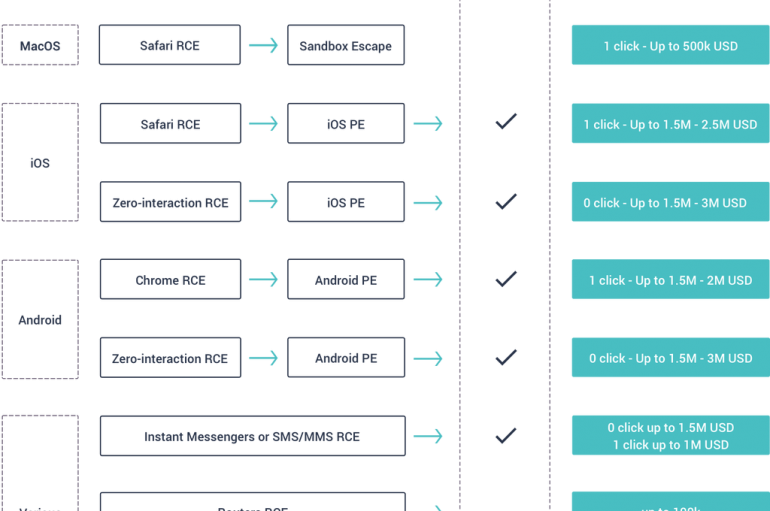
Vulnerability Research Hub Crowdfense is willing to pay $3 Million for iOS, Android Zero-Day Exploits
World-leading vulnerability research hub Crowdfense is offering up to $3 million for full-chain, zero-day exploits for iOS and Android. Vulnerability research firm Crowdfense is offering up to $3 million for working exploits for iOS and Android zero-day. In 2018, Crowdfence
Chinese Hackers Backdoor Gaming Titles
Chinese hackers have launched supply chain attacks against three gaming companies in order to spread malware far and wide across Asian endpoints, according to ESET. The security vendor’s malware researcher, Marc-Etienne M.Leveille, wrote in a blog post on Monday that
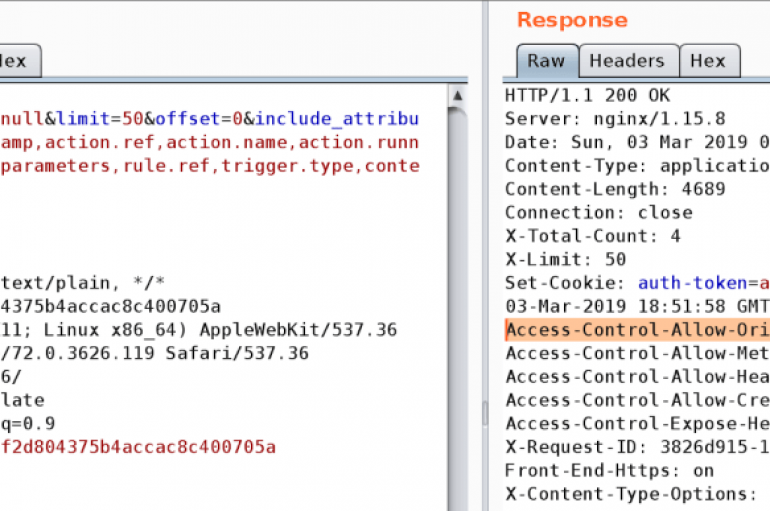
The security researcher Barak Tawilyhas discovered a severe vulnerability, tracked as CVE-2019-9580, in the popular, open source event-driven platform StackStorm. According to the expert, the flaw could be exploited by a remote attacker to trick developers into executing arbitrary commands
Security experts have discovered many vulnerabilities, including a critical issue, in Moxa EDS and IKS industrial switches. Industrial control systems used in many industries, including the energy sector, critical manufacturing, and transportation, continues to be an element of concern for
Pre-GDPR UK Breach Reporting Was a Mess
Many UK firms struggled to identify breach incidents, delayed reporting to the regulator and left out key details in the year prior to the GDPR, and could still be non-compliant today, according to new data obtained by Redscan. The managed
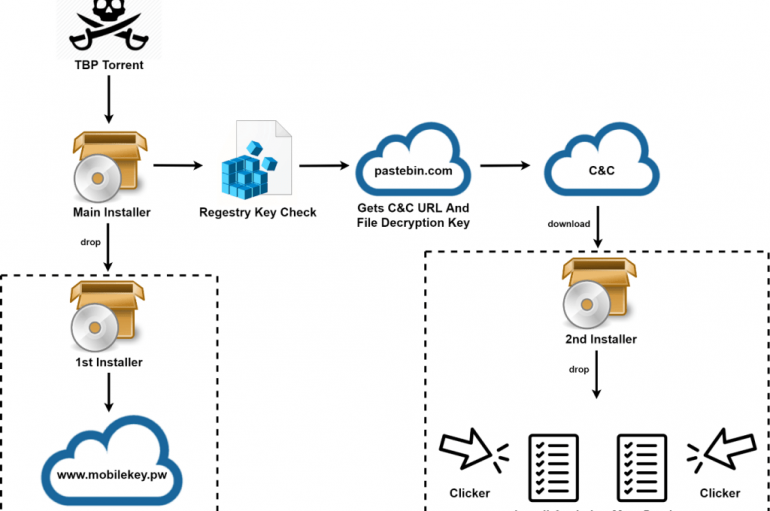
Crooks are abusing the torrent website The Pirate Bay to distribute the PirateMatryoshka malware that fuels the victim’s PC with unwanted software. Crooks abusing torrent services to distribute malware is not a novelty, Torrent users are often exposed to serious
Citrix hacked, Yes, Citrix suffered a massive data breach and the company believes that the attackers may have stolen atleast 6 TB to 10 TB of data by compromise the Citrix internal systems. Citrix Systems, Inc.a well-known software company that
An RSA Conference 2019 a panel representing the SANS Institute – featuring Heather Mahalik, director of forensics engineering at ManTech and mobile forensics course director, and Ed Skoudis, instructor, and Johannes Ullrich, dean of research – addressed the most dangerous
The Android caller ID app Dalil exposed online data belonging over 5 million users, security experts discovered a MongoDB database left accessible on the web without a password. The MongoDB behind the Android caller ID app Dalil was left exposed
Experts observed the STOP ransomware installing the Azorult password-stealing Trojan to steal account credentials, cryptocurrency wallets, and more. The STOP ransomware made the headlines because it is installing password-stealing Trojans on the victims’ machines. Experts observed the ransomware also installing
#RSAC: Fixing the Mess of IoT Security
Ken Munro, partner at Pen Test Partners, opened his talk at RSA Conference 2019 by explaining how easy it was for him to hack a Wi-Fi-enabled tea kettle. In the online manual, he discovered the default password. To find out