Too Much UPnP-enabled Connected Devices Still Vulnerable to Cyber Attacks
UPnP-enabled devices running outdated software are exposed to a wide range of attacks exploiting known flaws in UPnP libraries.
A broad range of UPnP-enabled devices running outdated software are exposed to attacks exploiting known flaws in UPnP libraries,
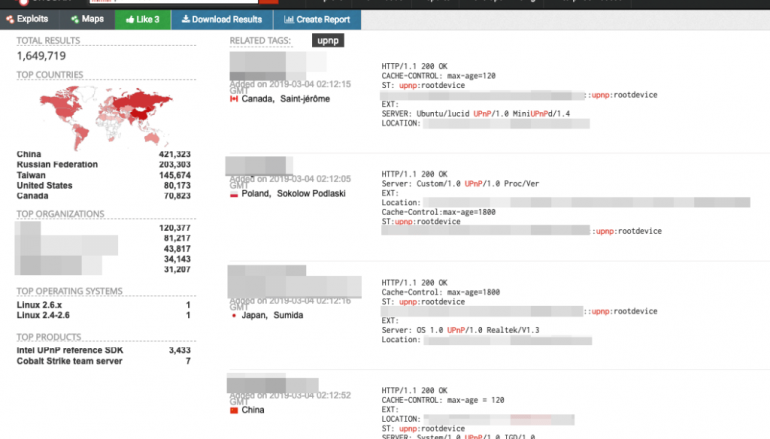
Tony Yang, Home Network Researcher, has found 1,648,769 devices using the Shodan search engine, 35% were using the MiniUPnPd UPnP daemon for NAT routers, 20% the Broadcom’s UPnP libraMost of them are UPnP-enabled devices that can be accessed online, consider for example, the large number of Chromecast adapters used by Smart TVs and Google Home which used them to play a video advertising for the PewDiePie’s channel.
“The hackers behind it reportedly took advantage of poorly configured routers that had the Universal Plug and Play (UPnP) service enabled, which caused the routers to forward public ports to the private devices and be open to the public internet,” reads the analysis published by Yang.
“Many devices such as cameras, printers, and routers use UPnP to make it easy for them to automatically discover and vet other devices on a local network and communicate with each other for data sharing or media streaming. UPnP works with network protocols to configure communications in the network.”

In April 2018, Akamai reported that threat actors compromised 65,000 home routers by exploiting vulnerabilities in Universal Plug’N’Play (UPnP), experts tracked the botnet as UPnProxy. In December 2018 the company provided an update to its initial analysis revealing a disconcerting scenario, UPnProxy is still up and running.
The UPnP communication protocol is widely adopted even if it is known to be vulnerable. In early 2013, researchers at Rapid7 published an interesting whitepaper entitled “Security Flaws in Universal Plug and Play” that evaluated the global exposure of UPnP-enabled network devices.
The report highlighted that over 23 million IPs related to Portable UPnP SDK were vulnerable to remote code execution just through a single UDP packet, over 6,900 product versions from over 1,500 vendors were vulnerable through UPnP due to the exposure of UPnP SOAP service to the internet.
Abusing the protocol attackers can control the traffic in and out the networks, UPnP allows the automated negotiation and configuration of port opening/forwarding within a NATed networking environment.
The malicious botnet uncovered by Akamai was composed of vulnerable devices including malicious NAT injections, it turns routers into proxies, for this reason, the experts called the injected devices UPnProxy.
According to Akamai, many UPnP vulnerabilities were still unpatched, the experts found that out of a pool of 3.5 million potentially vulnerable routers, 277,000 were still open to UPnProxy, and 45,000 have been compromised.
The campaign observed by Akamai in December tracked as EternalSilence, was targeting millions of machines living behind the vulnerable routers by leveraging the EternalBlue and EternalRed (CVE-2017-7494) exploits.
Experts observed millions of successful injections attempting to compromise millions of systems running SMB services, Akamai researchers speculate attackers are leveraging the Eternal family of exploits belonging to the NSA arsenal.
Hackers hijacked some 45,113 routers that expose a total of 1.7 million unique machines to the attackers.
Yang explained that cameras, printers, NAS devices, Smart TVs, and routers which use UPnP for streaming, sharing, and service discovery are exposed to attacks, threat actors could use them to potentially bypass firewalls and attack local network.
Most of the devices discovered by the expert still use old versions of UPnP libraries that are affected by years old flaws.
Data collected by the expert showed that 16 percent of those devices with UPnP enabled utilize the MiniUPnPd library, and only 0.39% is running the latest release 2.1.
Yang pointed out that initial and outdated version is running on 24.47% devices and another 29.98% is running MiniUPnPd 1.6.
This means that most of them are vulnerable, the expert also added that at least one of the following issues affect almost any device:
o CVE-2013-0230, a stack-based buffer overflow in MiniUPnPd 1.0 allows attackers to execute arbitrary code.
o CVE-2013-0229, a vulnerability found MiniUPnPd before 1.4, allows attackers to cause a denial of service (DoS)
o CVE-2017-1000494, an uninitialized stack variable flaw in MiniUPnPd
The expert also discovered 18% of the UPnP-enabled devices exposed online that was using Windows UPnP Server and roughly 5% of them use a libupnp library installation.
“We also found that 18 percent of the devices utilize Windows-based UPnP. These devices, Microsoft Windows XP machines (Windows NT 5.1) in particular, should check if the MS07-019patch has been applied.” continues the expert. “(It is also important to note that Windows XP reached end of life in April 2014, meaning it’s no longer supported by Microsoft and security problems will be left unpatched.) Windows XP comes with UPnP functionality that is enabled automatically out of the box. The patch addresses the UPnP memory corruption vulnerability (CVE-2007-1204) that enables a remote attacker to run arbitrary code in the context of a local service account.”
Experts suggest disabling the UPnP feature if possible to prevent abuses and are uring users of running firmware up to date.
This post Too Much UPnP-enabled Connected Devices Still Vulnerable to Cyber Attacks originally appeared on Security Affairs.





