Posts From CCME
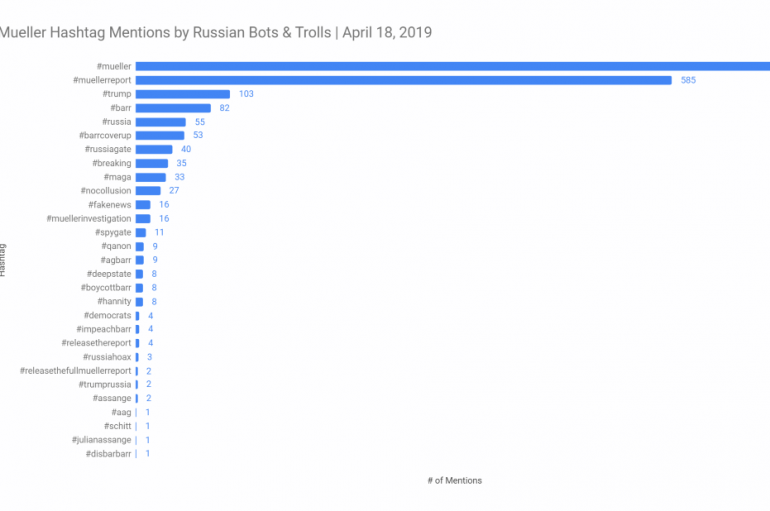
Experts at security firm SafeGuard reported that Russian Twitter bot activity raised up by 286 percent in the wake of the release of the Mueller Report. Social media platforms like Twitter are key components of misinformation campaigns carried out by
jQuery JavaScript Library Flaw Opens the Doors for Attacks on Hundreds of Millions of Websites
The popular jQuery JavaScript library is affected by a rare prototype pollution vulnerability that could allow attackers to modify a JavaScript object’s prototype. The impact of the issue could be severe considering that the jQuery JavaScript library is currently used
Researcher discovered a high-severity flaw in Shopify e-commerce platform that could have been abused to expose the traffic and revenue data for the stores. Bug bounty hunter Ayoub Fathi. discovered a vulnerability in a Shopify API endpoint that could be
Everybody knows by now that Cloud technology has changed our lives. So much so that it isn’t even news anymore: The Cloud is just there. It puts our lives at ease, of course, to know that our data and information
Hackers Launching Malware via Weaponized Excel File to Gain the Remote Access to the Target Computers
Cyber criminals launching a new malware campaign that make use of legitimate script engine AutoHotkey with a malicious script to evade detection and also gain the remote access to the targeted system. AutoHotkey is an open source Microsoft Windows tool
Password plays a vital role in securing your account, a common password is easy to remember, but it will be easier for an attacker to guess the password. An analysis of most Hacked Passwords showing still people is using weak
Hackers Launching DNS Hijacking Attack to Gain Persistent access to Sensitive Networks and Systems
Researchers discovered a new malicious campaign called “Sea Turtle,” attack public and private entities in various countries using DNS hijacking as a mechanism. State sponsored threat actors compromise at least 40 different organizations across 13 different countries during this malicious
Security researcher discovered a database belonging to a ride-hailing company operating in Iran that was left exposed online containing over 6.7M records. Security researcher Bob Diachenko discovered a database belonging to a ride-hailing company operating in Iran that was left
Researcher discovered eight unsecured databases exposed online that contained approximately 60 million records of LinkedIn user data. Researcher Sanyam Jain at GDI foundation discovered eight unsecured databases exposed online that contained approximately 60 million records of LinkedIn user data. Most
Antivirus solutions from different vendors are having malfunctions after the installation of Windows security patches released on April 9, including McAfee, Avast and Sophos. Antivirus solutions from different vendors are showing malfunctions after the installation of Windows security patches released
USBStealer – Password Hacking Tool For Windows Applications to Perform Windows Penetration Testing
USBStealer is a Windows Based Password Hacker Tool that helps to Extract the password from Windows-Based Applications such as Chrome Password, FireFox Password, NetPassword, Admin passwords of the Windows Computer. The vast majority of the general population realize that windows
Google this week announced that it is going to block login attempts from embedded browser frameworks to prevent man-in-the-middle (MiTM) phishing attacks. Phishing attacks carried out by injecting malicious content in legitimate traffic are difficult to detect when attackers use
Maltego is an intelligence gathering tool, its available for windows, mac, and Linux. We will be using Kali Linux where it’s available by default. Remember to register on their website and I have it configured. There are a lot of
Hacker Broke into Super Secure French Government’s Messaging App Tchap Hours After Release
A white hat hacker discovered how to break Tchap, a new secure messaging app launched by the French government for officials and politicians. The popular French white hat hacker Robert Baptiste (aka @fs0c131y) discovered how to break into Tchap, a
The weather channel hit with a ransomware attack on its own network stop’s the live Broadcasting and down the website about 90 minutes On Thursday morning, from 6AM to 7:39AM. The Weather Channel (TWC) is an American pay television channel
Free Email Security Penetration Testing Tool to Check Organization’s Security against Advanced Threats
BitDam launches a free Email Security Penetration Testing tool to determine the organization’s security posture against advanced threats. The Email accounts are the tempting targets for hackers, they find every possible way to infiltrate your email accounts as they are