Posts From CCME
Most Important Security Consideration to Strengthen Enterprise IT Security Against Cyber Attack
Cyberattacks are always evolving and hackers are always one step ahead of enterprises. Ransomware, DDoS, Man-in-the-middle, Phishing and more, their hacking methodologies always seems to evolve, especially the recent cryptojacking takedowns. Enterprises are always requested to keep their security procedures
India’s Leading outsourcing giant Wipro Ltd confirmed that some of its employee accounts have been hacked in an advanced phishing campaign. The company detected an abnormal activity in a few of his employee accounts on its network. Kerbs On Security
NCSC Launches 2019 Cybersecurity Accelerator
The UK’s National Cyber Security Centre (NCSC) has launched its latest annual search for the hottest cybersecurity start-ups in the country. The NCSC Cyber Accelerator is a government-funded initiative that claims to have doled out GBP20m in investment since its
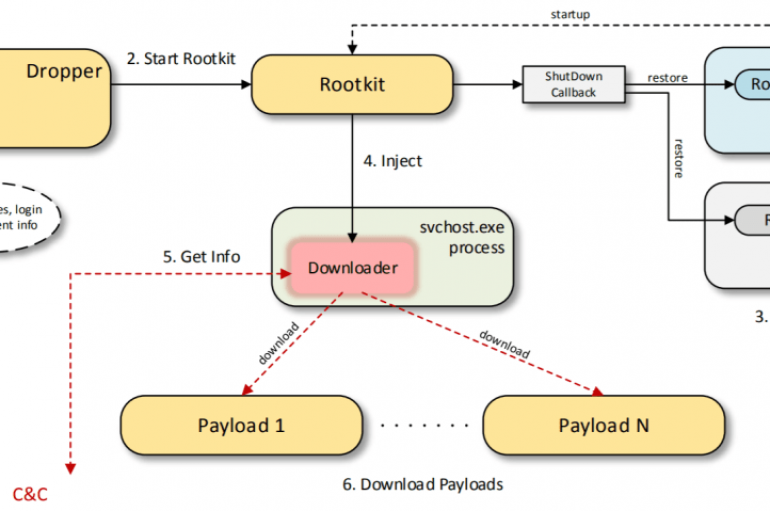
Scranos is a powerful cross-platform rootkit-enabled spyware discovered while investigating malware posing as legitimate software like video players, drivers and even anti-virus products. The Scranos rootkit malware was first discovered late last year when experts at Bitdefender were analyzing a
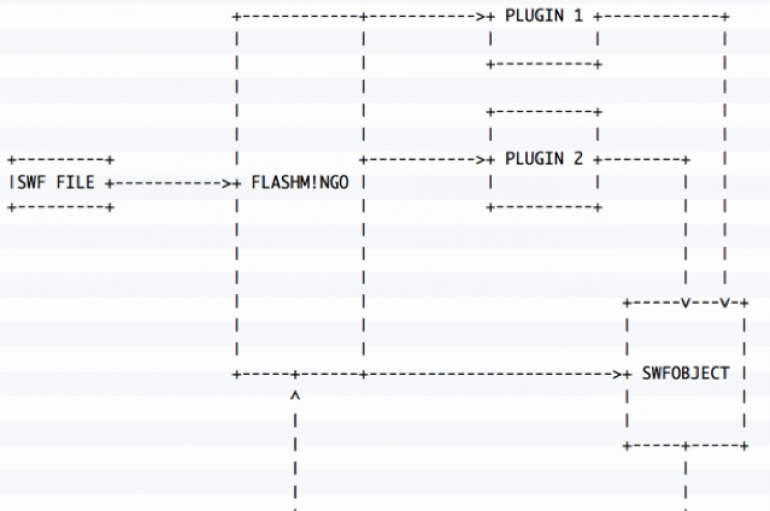
Cyber security firm FireEye announced the release of FLASHMINGO, a new open source tool designed to automate the analysis of Adobe Flash files. FireEye released FLASHMINGO, a new open source tool designed to automate the analysis of Adobe Flash files.
Blue Cross of Idaho announced to have suffered a data breach, hackers accessed to the personal information of about 5,600 customers. Blue Cross of Idaho announced suffered a data breach that might have exposed the personal information of about 5,600
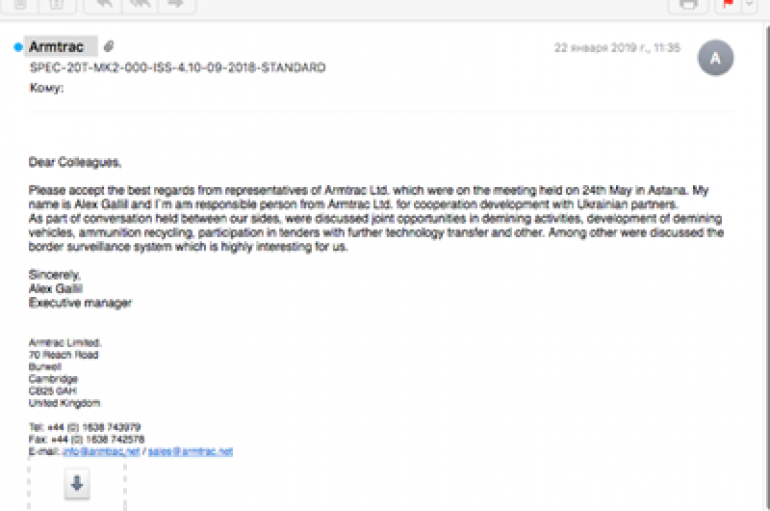
A spear-phishing email campaign targeting government entities in Ukraine could have been active as early as 2014, according to FireEye. In a blog post published on April 16, 2019, FireEye Threat Intelligence found the latest spear-phishing email in early 2019,
Expert discovered an exploit that could allow ad blocking filter list maintainers for the Adblock Plus, AdBlock, and uBlocker browser extensions to craft filters to inject remote scripts into web sites. ad blocking extensions receive in input a list of
Instagram users are being warned not to fall for a new phishing scam doing the rounds which aims to harvest log-ins and spread worm-like across the social network. According to Twitter users who have posted screenshots of the scam, users
Miner Malware Uses Multiple Propagation Methods to Infect Windows Machines and to Drop Monero Miner
A miner malware that uses a number of techniques that includes EternalBlue, Powershell abuse, pass-the-hash technique, Windows admin tools, and brute force to infect windows machine and to drop a Monero miner. According to Trend Micro telemetry, the threat actors
SIM Swap Attack Let Hackers Port a Telephone Number to a New SIM to Hack WhatsApp & Bypass 2FA
Cybercriminals are activity performing SIM swap Attack in various countries to bypass 2 Factor Authentication and to compromise the various social media apps including WhatsApp by porting a victims telephone number to a new SIM card. This widespread attack causing
Today, Kaspersky Labs announced that it had detected a “previously unknown vulnerability” in Microsoft Windows, which was exploited by an unidentified criminal group. The company theorizes that it was an attempt to gain full control over a targeted device. The
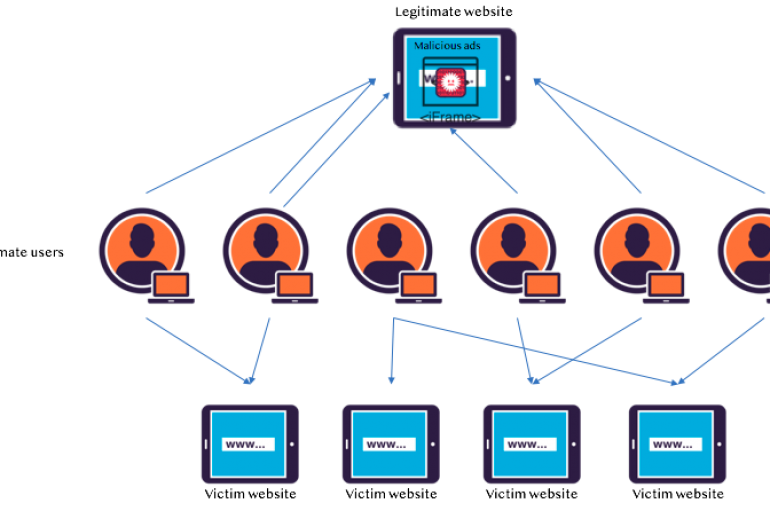
Experts at Imperva discovered a new type of large-scale DDoS attack that abuses the HTML5 Ping-based hyperlink auditing feature. Experts at Imperva Vitaly Simonovich and Dima Bekerman observed a large-scale DDoS attack abusing the HTML5 Ping-based hyperlink auditing feature. The
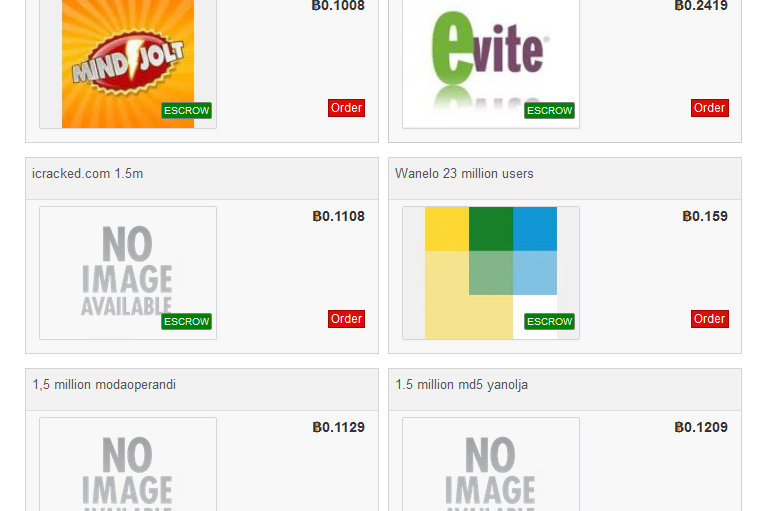
Gnosticplayers Round 5 – 65 Million+ Fresh Accounts from 6 Security Breaches Available for Sale
The popular hacker Gnosticplayers made the headlines again, he is offering for sale on the dark web the fifth round of hacked accounts. The popular hacker Gnosticplayers is offering for sale on the dark web the fifth round of hacked
Secure Email Accounts is one of the most important concerns in the digital world since the email account is one of the most targetted sources for cyber attacks . The Email accounts are the tempting targets for hackers, they find
Web server pen testing performing under 3 major category which is identity, Analyse, Report Vulnerabilities such as authentication weakness, configuration errors, protocol Relation vulnerabilities. 1. “Conduct a serial of methodical and Repeatable tests “ is the best way to test