Posts From CCME
Famous Email service provider Click2mail suffering from a massive data breach that leaked their customer sensitive personal information, and the attackers used the stolen email addresses to send spam emails. October 4th, 2019, Click2Mail learned that their customer’s data were
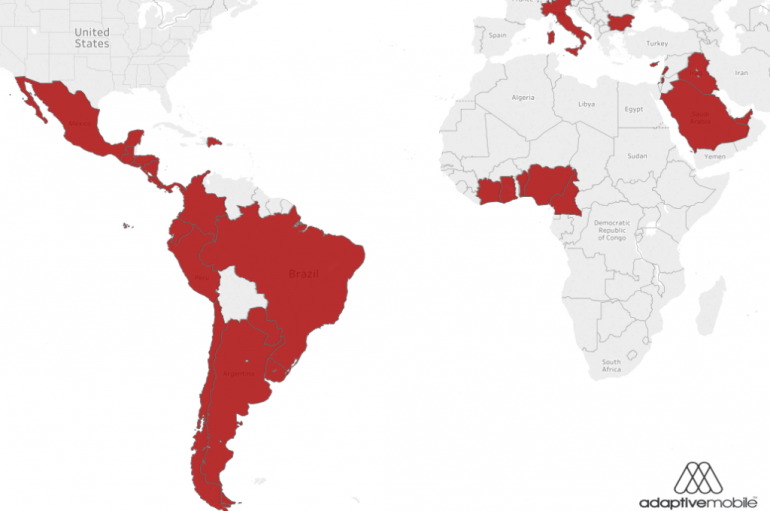
Exactly one month ago, researchers at AdaptiveMobile Security disclosed a critical vulnerability in SIM cards dubbed SimJacker that could be exploited by remote attackers to compromise targeted mobile phones and spy on victims just by sending an SMS. The SimJacker
There is a privacy threat lurking on perhaps hundreds of millions of devices, that could enable potential attackers to track and profile users, by using information leaked via the Tor network, even if the users never intentionally installed Tor in
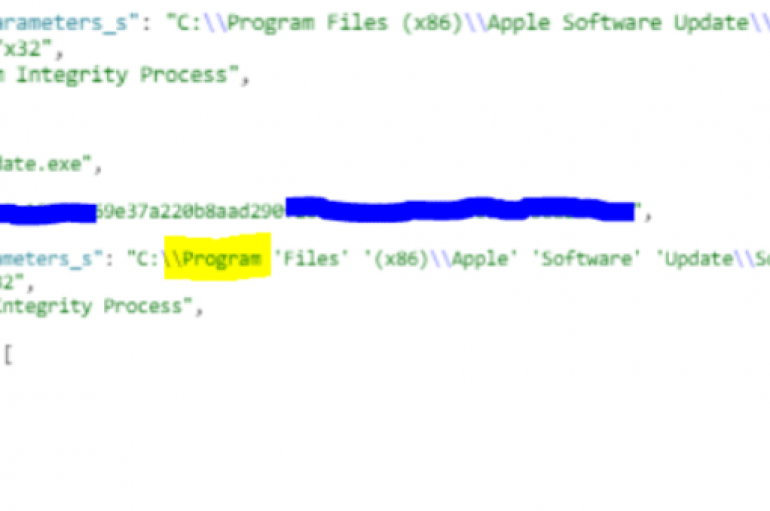
Researchers found a new footprint about the recent BitPaymer ransomware campaign that was exploited the Apple iTunes for Windows Zero-day vulnerability to attacker public and private sectors across the U.S. Threat actors took advantage of a zero-day vulnerability that resides
Sophos addressed a vulnerability in its Cyberoam firewalls that could be exploited by an attacker to gain access to a company’s internal network without providing a password. “A critical shell injection vulnerability in Sophos Cyberoam Firewall appliances running CyberoamOS (CROS)
For modern security systems to succeed, it’s important for organizations to expect that security systems will fail. By expecting failure and planning for it, it’s possible to be more resilient and deliver better security outcomes, according to Solomon Sonya, assistant
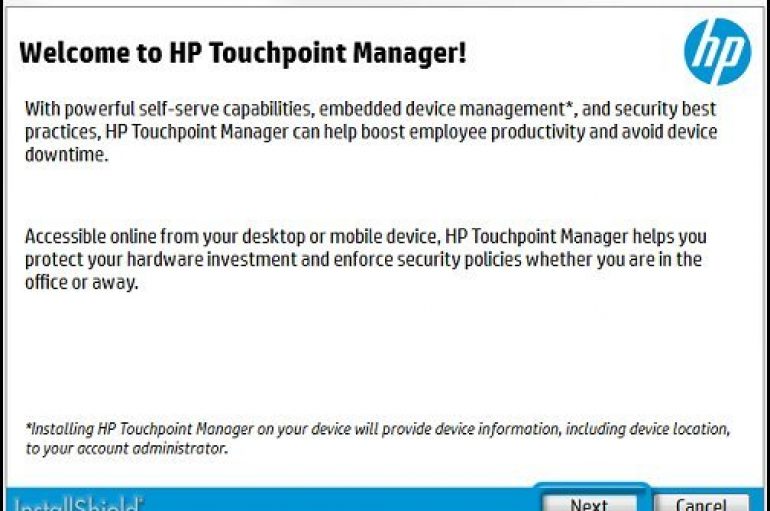
Security researchers at SafeBreach have discovered that the HP Touchpoint Analytics service is affected by a serious flaw tracked as CVE-2019-6333. The vulnerability received a CVSS score of 6.7 (medium severity). The TouchPoint Analytics is a service that allows the
An audit of Mississippi government institutions has revealed an alarming lack of compliance with standard cybersecurity practices and with the state’s own enterprise security program. A survey of 125 state agencies, boards, commissions, and universities conducted by the Office of
New research has found that only a quarter of Americans know that surfing the internet in private browsing mode only prevents other users of the same computer from seeing what you’ve been up to online. A survey conducted in June
FIN6 Hacker Group Inject Skimmers into Thousand of E-commerce Sites to Steal Credit Card Data
FIN6 hacking group active since 2015, PoS systems are their primary targets. The hacking group is financially motivated and employs several attack vectors to steal payment card data. Researchers observed a new FIN6 hacking group campaign attacking the E-commerce websites
Charming Kitten APT Hackers Group Abusing Google Services to Attack U.S Presidential Campaign Members
The Iranian based hacker group Charming Kitten, also known as APT35 or Ajax or Phosphorus is active since 2014. The hacker group primarily targets researchers from the US, Middle East, and France, focusing on Iranian academic researchers, Iranian dissidents in
The cybercriminals behind BitPaymer and iEncrypt ransomware attacks have been found exploiting a Windows zero-day vulnerability for Apple iTunes and iCloud in attacks in the wild. The zero-day vulnerability resides in the Bonjour updater that comes packaged with Apple’s iTunes
ESET researchers discovered an advanced malware piece of malware named Attor, that was used in cyberespionage operations on diplomats and high-profile Russian-speaking users in Eastern Europe. The researchers believe that the threat actor behind Attor a state-sponsored group involved in
In a paper released today, the Information Security Forum is urging organizations to capitalize on the opportunities offered by artificial intelligence while taking sensible steps to reduce the risks posed by this still immature technology. Demystifying Artificial Intelligence in Information
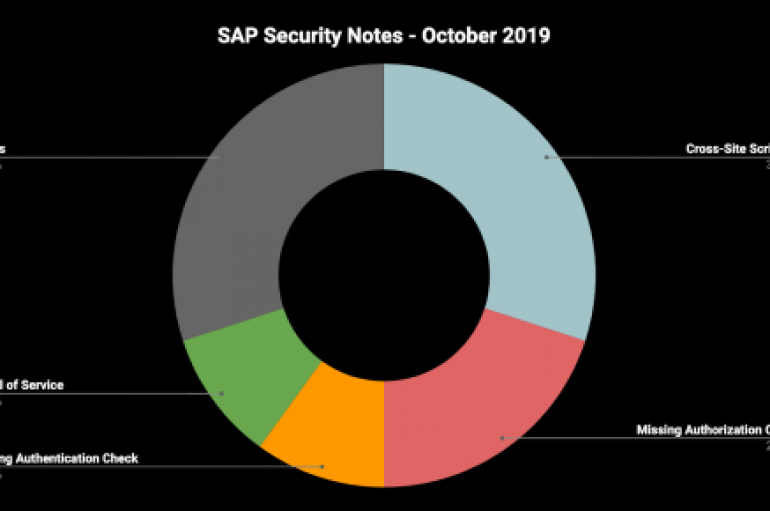
SAP has released its October 2019 Security Patch Day updates that also address two critical vulnerabilities (Hot News) with CVSS scores of 9.3 and 9.1. The October 2019 Security Patch Day also includes a High Priority Note addressing Binary Planting
Multiple Vulnerabilities Found in Satellite Internet Access Terminal Let Hackers Intercept the GPS Traffic
Researchers from CERT/CC discovered multiple vulnerabilities in Satcom terminal Cobham EXPLORER 710 that affects both firmware and device. The vulnerabilities allow hackers to perform several attacks such as intercept the traffic, remotely execute the command, implant and hide a backdoor,