Posts From CCME
Analyst Urges UK CISOs to Act on Brexit
A leading analyst firm has warned British CISOs to focus on three key areas to mitigate the potential fallout from the UK’s departure from the European Union. Whether the UK strikes a withdrawal agreement with the EU or not, security
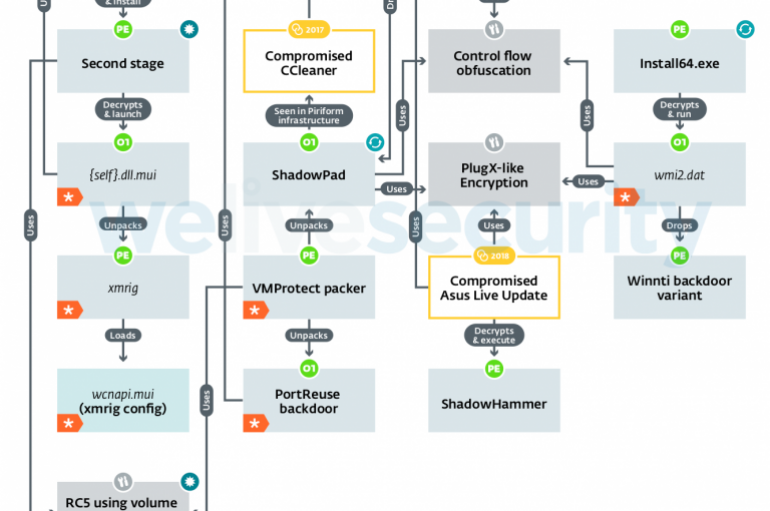
Security experts at ESET revealed that Winnti Group continues to update its arsenal, they observed that the China-linked APT group using a new modular Windows backdoor that they used to infect the servers of a high-profile Asian mobile hardware and
Microsoft and NIST Team Up on Patching Guide
Microsoft has teamed up with the US National Institute of Standards and Technology (NIST) to develop a new guide designed to make enterprise patch management easier. Microsoft lead cybersecurity architect, Mark Simon, explained that the firm had first worked closely
A Florida clinic providing specialized medical care for women has alerted all current and former patients that their personal information and medical records may have been exposed following a data breach. North Florida OB-GYN, which joined Women’s Care Florida on
A new vulnerability has been discovered in the Linux Sudo program let unprivileged users can run the command as root by specifying the user ID -1 or 4294967295. Sudo (Superuser Do) program in Linux is responsible to allocate the security
Ransomware attack is quite common nowadays since Malicious software spreading everywhere through various mediums. The cybercriminals that use it are looking to do one thing, extort your money. Not unlike the movies, it usually starts with an ominous ransom note
Tactics of Supply-Chain Attack Group Exposed
Researchers have exposed the underhanded methods of a threat group responsible for unleashing a string of supply-chain attacks. Winnti Group has been targeting the gaming industry for nearly a decade. Their preferred mode of attack is to compromise game developers,
New problems for Apple, most of its users likely ignore that the company is sharing iOS web browsing data on some of them to Chinese giant Tencent. Most Apple users likely don’t know that the tech giant is sending iOS
Stolen Cloud API Key to Blame for Imperva Breach
A security breach which led to the compromise of customer data at Imperva was caused by a stolen API key for one of its Amazon Web Services (AWS) accounts, the firm has revealed. The firm was notified of the incident,
The world of today continues its progress toward higher digitalization and mobility. From developments in the Internet of Things (IoT) through augmented reality to Industry 4.0, whichrely on stronger automation and use of robots, all of these bring more efficiency
Introduction The group behind Emotet malware is getting smarter and smarter in the way they deliver such a Malware. While the infection schema looks alike from years; the way the group tries to infect victims improves from day to day.
New research shows how easy to hide a $200 tiny spy Chip inside an IT equipment and to gain backdoor access to the device. Security researcher Monta Elkins, to demonstrate how he created a proof-of-concept version in the CS3sthlm security
Researchers discovered 2 new hacking tools called BOOSTWRITE and RDFSNIFFER that were added in FIN7 groups malware arsenal with sophisticated capabilities and techniques. FireEye Mandiant investigators uncovered that these new hacking tools were added for hijacking the DLL load order
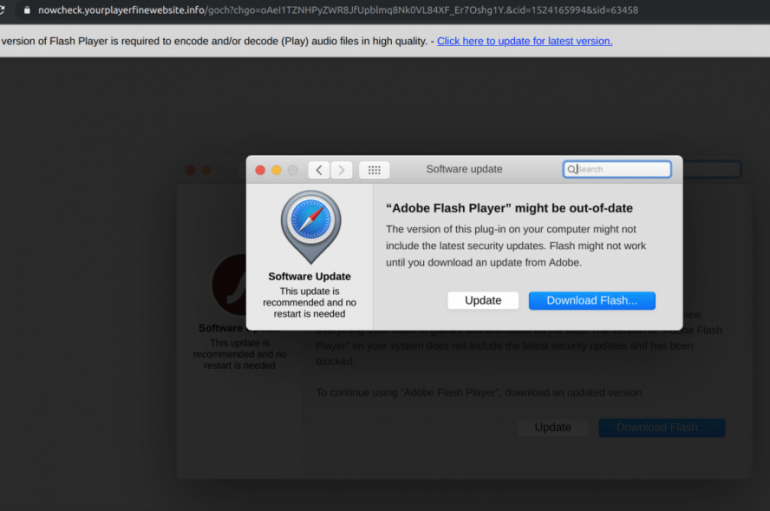
Confiant researchers have discovered a new Mac malware dubbed Tarmac distributed via malvertising campaigns in the US, Italy, and Japan. Security experts at Confiant have discovered a new Mac malware dubbed Tarmac that is distributed via malvertising campaigns in the
A website and online presence are more important for your company now than ever before. Unfortunately, the increased reliance and use of technology by businesses have led to a major increase in data breaches and hacks. There are many different
Leafly, the world’s leading cannabis resource, informed its customers via email that has suffered a data leak. On September 30, the company discovered that customer The company discovered on September 30 that a secondary database was exposing customer information from