#SecTorCa: Finding a New Route to Solve Tomorrow’s Cyber-Attacks
For modern security systems to succeed, it’s important for organizations to expect that security systems will fail. By expecting failure and planning for it, it’s possible to be more resilient and deliver better security outcomes, according to Solomon Sonya, assistant professor of computer science at the United States Air Force Academy.
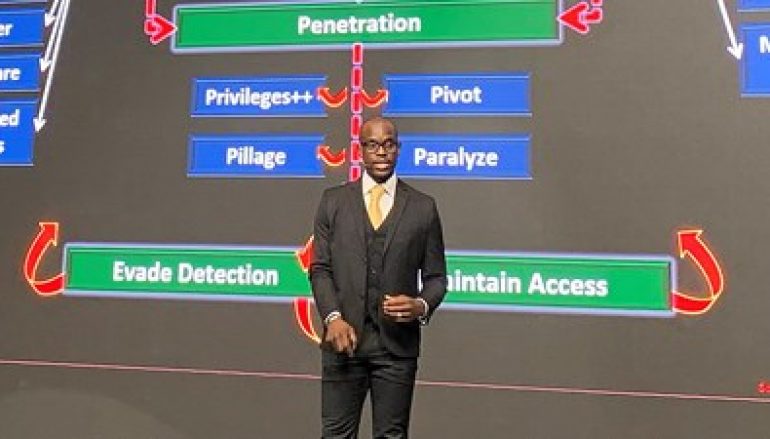
Sonya delivered his message during a keynote at the SecTor security conference in Toronto, Canada on October 10, where he emphasized the need for employing what is known as a Byzantine Failure approach, rather than relying on a detection-only approach for IT security attacks. The Byzantine Failure approach in computer science is all about understanding that failure is something that will happen and as such, a strategy needs to be put in place for the eventuality.
“Tomorrow’s attacks will be worse than today’s,” Sonya said. “Malware continues to increase in sophistication, prevalence and proliferation across the enterprise.”
Malware has changed over the past two decades, but the basic approach employed by many organizations has not, in Sonya’s opinion. He noted that a key challenge is the fact that many of today’s security paradigms are predicated on a false belief that detection is key to success. Sonya detailed how malware has changed from the early days of SQL Slammer in 2003 to the modern threats of ransomware and fileless attacks. A key part of malware’s evolution is how it has become increasingly sophisticated and difficult to always detect or immediately block.
“Some people will argue that attacks won’t happen tomorrow because AI will better protect us,” Sonya said. “AI is good, but it’s not sufficient.”
Rather, Sonya emphasized that what is needed is for organizations to identify the weakness in systems and networks. With the weak links identified, Sonya said it’s important to understand what should be done to actually secure the assets and data that are critical to the organization.
“So if you look at the attack surface from a Byzantine perspective, you start by taking the system that you want to protect, you draw a circle around it and you say which failures can lead to compromise,” Sonya explained.
What ‘Right’ Looks Like
Rather than relying on existing approaches and expecting to be able to detect incursions, Sonya suggested that organizations should “take the road less travelled” and instead of just buying a product, invest the time to understand and discover what can fail and lead to exploitation.
For Sonya, the ‘right’ approach also involves making use of Software Defined Network (SDN) technology, to segment networks and reduce the potential impact of a failure. While detecting threats alone isn’t a winning strategy, he emphasized that having actionable threat intelligence is a valuable component.
“Many vendors will say they have threat intelligence, but what they actually provide is just data,” he argued. “Intelligence is useful only in order to help us get some kind of action and actually make a decision based on the intelligence.”
Looking beyond just basic passwords, Sonya suggested that organizations consider new forms of secure access protection systems that can validate users based on activity as well as other attributes. Additionally, there is a need for organizations to rethink how Digital Loss Prevention (DLP) technologies are used and deployed. In his view, DLP needs to be deployed in a stack for data at rest and in motion, such that if data is lost or stolen, it can’t be used by an attacker.
To conclude, Sonya noted that security professionals need to constantly question the security paradigm, be curious and explore the possibilities that an unconventional attack might introduce into an organization.
“In our scheme of protecting machines, our initial response should not rely on detection, because if we wait until we detect, it could be too late,” Sonya said.
This post #SecTorCa: Finding a New Route to Solve Tomorrow’s Cyber-Attacks originally appeared on InfoSecurity Magazine.





