Archive
This report contains the results of the Managed Detection and Response (MDR) service (brand name – Kaspersky Managed Protection). The MDR service provides managed threat hunting and initial incident response. Threat hunting is the practice of iteratively searching through data
Speaking at the ATM & Cybersecurity 2019 conference in London, detective superintendent Andrew Gould, National Cybercrime Programme Lead, National Police Chief’s Council, detailed common attackers, attack tactics and the most common ways to prevent them from happening. Saying that the
A new global study from Thales and the Ponemon Institute has exposed a disparity between the rapid growth of data stored in the cloud and organizations’ approaches to cloud security. The firms surveyed more than 3000 IT and IT security
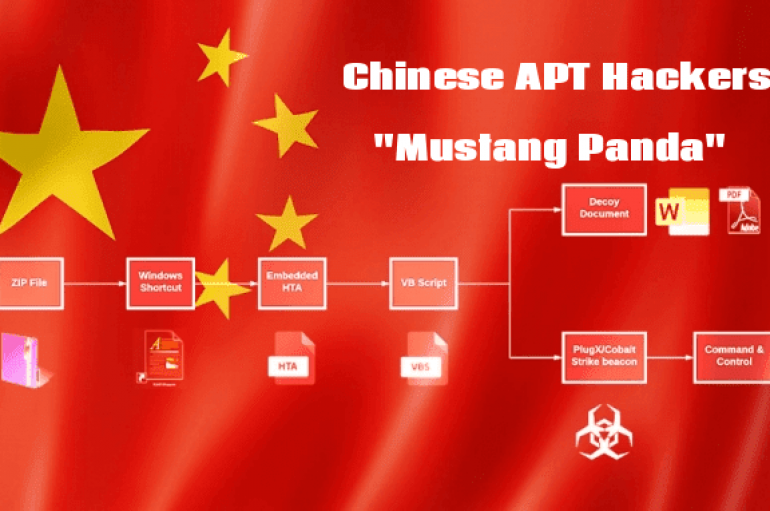
Chinese APT Hackers Mustang Panda Attack Public & Private Sectors Using Weaponized PDF and Word Documents
Researchers discovered an ongoing malware campaign that believed to be operating by a Chinese based threat group called “Mustang Panda” that targets public and private sectors around the world. Mustang Panda threat group activities initially observed in June 2018, since
RCE Vulnerability in D-Link Routers Let Hackers Access the Router Admin Page Without Credentials
Security researchers disclosed a new unauthenticated command injection vulnerability in some of the D-link routers. The vulnerability can be tracked as CVE-2019-16920 and rated as critical. Successful exploitation of the vulnerability results in Remote Code Execution, an attacker can trigger
Microsoft Security Updates – Patches for Multiple RCE Vulnerabilities that Affected Microsoft Office
Microsoft released security updates for Microsoft Office vulnerability, the update covers 14 vulnerability, out of that 9 vulnerabilities are remote code execution vulnerabilities. The update covers the vulnerabilities in Excel 2016, Office 2016, Excel 2013, Office 2013, Excel 2010, Office
Don’t treat cyber-risk any differently to any other risk to your business, as engagement with senior management continues to be a challenge. Speaking at the ATM & Cybersecurity 2019 conference in London, Nina Paine, global head of cyber partnerships and
Essay on Ethical Hacking: Is It Legal?
Sometimes, the toughest part of an essay is its topic. Many students aren’t able to cover definite topics plainly and interesting. Commonly, they struggle with some unknown issues or themes, which are assigned quite rarely. For example, not all people
The personal information of 92 million Brazilian citizens has been discovered for sale to the highest bidder on an underground forum auction. According to BleepingComputer, the auction is present on multiple dark web marketplaces that can only be accessed by
A health organization in New Zealand that was targeted in a global cyber-incident in August has uncovered evidence of earlier attacks dating back three years. Tū Ora Compass Health took its server offline and strengthened its IT security following a
Researchers at Fortinet’s FortiGuard Labs have publicly disclosed a critical remote code execution vulnerability affecting some models of D-Link routers. Security experts at Fortinet’s FortiGuard Labs disclosed a remote code execution vulnerability tracked as CVE-2019-16920. The vulnerability is an unauthenticated
More than three-quarters (77%) of UK workers claim to have never received any form of cyber-skills training from their employer, according to research from Centrify. The company surveyed 2000 fulltime professional services workers in the UK, discovering that along with
APT groups exploiting vulnerabilities in popular enterprise VPN products to retrieve arbitrary files that include login credentials, change configuration settings, or connect to further internal infrastructure. According to the National Cyber Security Centre (NCSC) research, threat actors actively attacking the
Buggy Malware Attack on WordPress Websites by Exploiting Newly Discovered Theme & Plugin Vulnerabilities
Researchers discovered an ongoing buggy malware campaign that attempts to exploit the newly discovered vulnerabilities resides in the WordPress theme and plugin. Cybercriminals are always curious about developing the exploits soon after the new vulnerabilities found in wide particularly sites
US and UK Sign Crime Data Sharing Agreement
UK Home Secretary Priti Patel and US Attorney General William Barr have signed a bilateral agreement paving the way for UK and US law enforcement agencies to obtain data more quickly from electronic service providers operating in each jurisdiction. According
Thales and Verint have announced the release of The Cyberthreat Handbook, a report designed to provide insights into the most significant groups of global cyber-attackers through detailed rating cards. The two companies combined to carry out a year-long investigation into