Archive
NASA Office of Inspector General revealed that the Agency’s network was hacked in April 2018, intruders exfiltrated roughly 500 MB of data related to Mars missions. According to a report published by the NASA Office of Inspector General, hackers breached
Nmap – A Detailed of Explanation Penetration Testing Tool to Perform Information Gathering
Nmap is an open source network monitoring and port scanning tool to find the hosts and services in the computer by sending the packets to the target host for network discovery and security auditing. Numerous frameworks and system admins additionally
Security researcherfrom F5 Networks that released more details and proof-of-concept for the recently addressed flaw in Outlook for Android. Microsoft has recently addressed an important vulnerability, tracked as CVE-2019-1105, in Outlook for Android, that potentially affected over 100 million users.
U.S Launched Cyber Attack on Iranian Military Computers After U.S Military Drone Shot Down by Iran
United States Military launched a cyber attack on the Iranian Military computers that used to control the Iran missiles after the $240 million Worth U.S drone shootdown by Iran. The attack was mainly targeting the Iran military computer systems with
Cloud Computing Penetration Testing is a method of actively checking and examining the Cloud system by simulating the attack from the malicious code. Cloud computing is the shared responsibility of Cloud provider and client who earn the service from the
Security researchers discovered a double free vulnerability in macOS caused by memory corruption flaw in the AMD component. Successful exploitation of the vulnerability allows an attacker to escalate privilege and to run malicious code as a root user. The vulnerability
Its time for hackers to hack your PC using malformed video file, yes, critical vulnerabilities in VLC media Player let attackers load specially crafted video files in the vulnerable system to execute the arbitrary code. VideoLAN released a security update
Security experts at Malwarebytes have discovered a new macOS crypto miner, tracked as Bird Miner, that works by emulating Linux. Researchers at MalwareBytes have spotted a new cryptominer, tracked as Bird Miner, that targets macOS and emulates Linux. The malware
North American homes have the highest density of internet of things (IoT) devices of any region in the world, according to researchers at Stanford University and Avast. Together, Stanford University and Avast have published findings of their research in a
Dell Advises PC Users to Update SupportAssist
Dell has released a security alert letting customers know that they should update SupportAssist for both business and home PCs. The vulnerability was discovered by SafeBreach security researcher Peleg Hadar, who wrote that the OEM software vulnerability puts multiple laptops
Desjardins Insider Accessed Data of 2.9m Members
Canada’s largest credit union and one of the world’s largest banks, Desjardins, published a security advisory after a former employee gained unauthorized access to the data of 2.9 million members. The former employee was fired as a result of the
Russia-Linked cyberespionage group Turla uses a new toolset and hijacked command and control infrastructure operated by Iran-Linked OilRig APT. Russia-linked Turla cyberspiesused a new set of tools in new attacks and hijacked command and control infrastructure operated by Iran-Linked OilRig
While the debate on the 5G rollout has focused on Huawei, the work has been much wider and had to consider attacks and technical precision, according to the NCSC. Presenting at Chatham House in London, NCSC CEO Ciaran Martin said
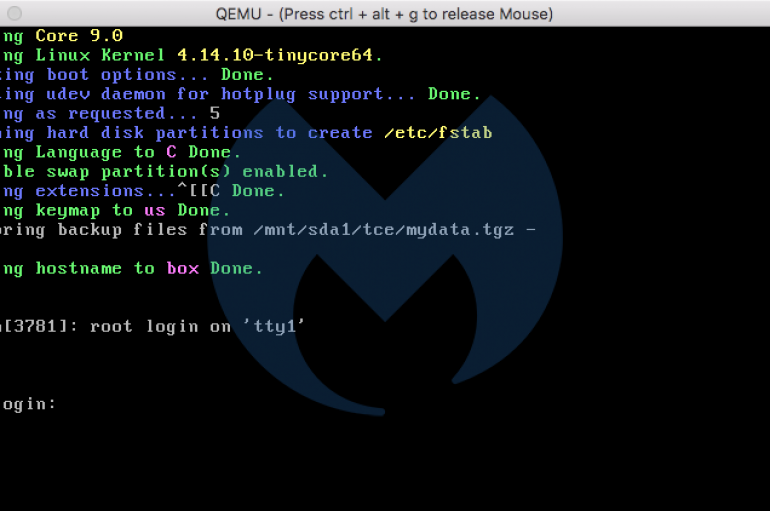
Warning Made on Cross-Platform Cryptominer
ESET has warned of cross-platform software which is used to mine cryptocurrency. Named LoudMiner, the malware uses virtualization software – QEMU on macOS and VirtualBox on Windows – to mine cryptocurrency on a Tiny Core Linux virtual machine. LoudMiner is
First time Kali Linux unveils a roadmap that highlights the changes and the new features coming to Kali Linux in the following year. The Kali Linux team is “trying to balance our efforts between changes that are user facing and
Spoofing Vulnerability in Outlook for Android Let Hackers Perform Cross-site Scripting Attacks – Update Now
Microsoft released a new security update with the fixes of Spoofing vulnerability affected an Outlook for Android that allows attackers to perform Cross-site Scripting attacks in vulnerable android device. A spoofing attack is a method of fraudulent or malicious practice