Archive
Cisco released security updates for Data Center Network Manager that allows an unauthenticated, remote attacker to upload arbitrary files on an affected device. CVE-2019-1620 – File Upload & Remote Code Execution The vulnerability resides in the web-based management interface of
Multiple flaws in the BlueStacks Android emulator were addressed, including a vulnerability that allowed attackers to remotely control code execution. Other issues included information disclosure and a flaw that allowed attackers to steal backups of the VM and its data.
New ViceLeaker Malware Attack on Android Devices With Backdoor Capabilities to Hijack Camera, Record Audio
Researchers discovered a new malware campaign called ViceLeaker that specifically targeting the Android users with sophisticated backdoor capabilities to Hijack camera, delete files, record audio and more. Some of the Malware samples discovered by Kaspersky researchers are modified versions of
Account Take over Vulnerability in EA Origin Game Client Let Hackers Hijack the 300 Million Gamers Account
Researcher uncovered a critical chain of vulnerabilities in Popular EA’s Origin gaming client allows attackers to take over the players account and committing the identity theft against 300 Million EA Gamers. EA (Electronic Arts) is a second largest American based
Another Florida city has decided to pay a ransom to the hackers who took control over its municipal computer systems. On June 25, the mayor of Lake City said the northern Florida city would pay hackers $460,000 to regain control
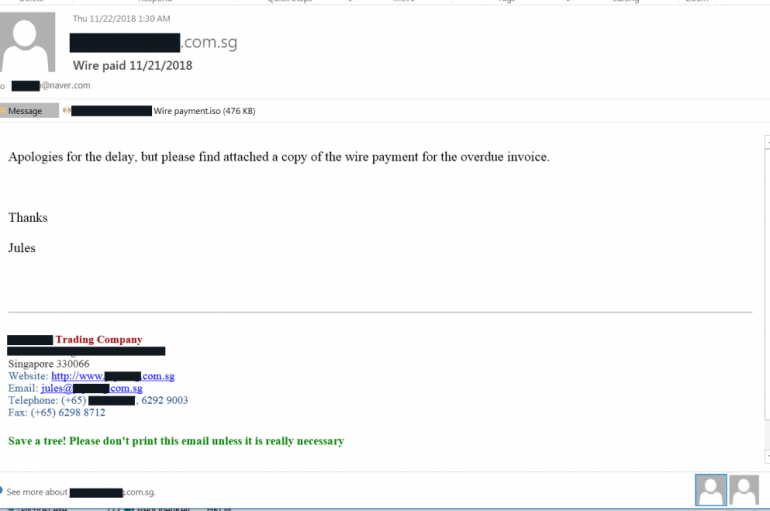
Experts from security firm Netskope observed variants of LokiBot and NanoCore malware distributed in ISO Image through malspam campaign. Security firm Netskope observed a new malspam campaign delivering variants of LokiBot and NanoCore malware in ISO image file attachments. “Netskope
Security researchers are warning of a “dramatic” increase in the exploitation of legitimate file sharing services to deliver malware in email-based attacks, especially OneDrive. FireEye claimed in its latest Email Threat Report for Q1 2019 that services including WeTransfer, Dropbox,
Tech support gangs have been spotted using paid search to reel in unsuspecting victims looking for food-related content online, according to Malwarebytes. The security vendor spotted scammers buying ads for Google and Bing which it said are designed to lure
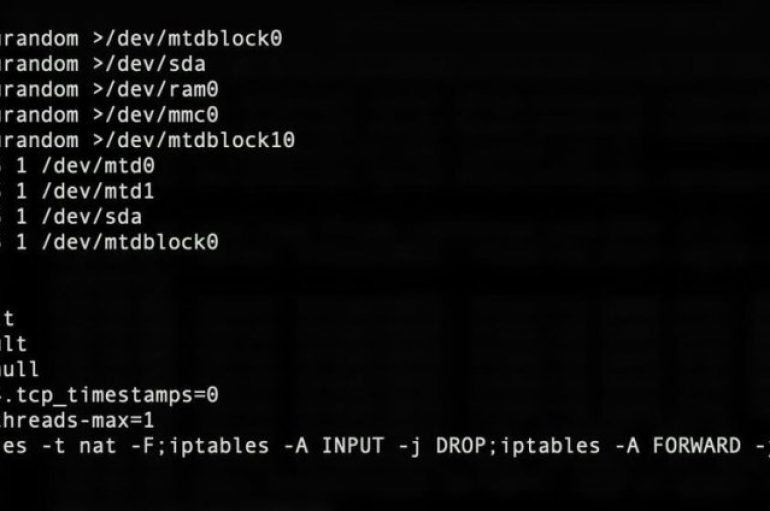
Security experts warn of a new piece of the Silex malware that is bricking thousands of IoT devices, and the situation could rapidly go worse. Akamai researcher Larry Cashdollar discovered a new piece of the Silex malware that is bricking
Infamous Chinese APT 10 hackers compromised over 10 Telecom networks around the world under the campaign called Operation Soft Cell and stealing various sensitive data including call records, PII, and attempting to steal all data stored in the active directory.
A new Mac malware dubbed OSX/Linker leverages the recently disclosed macOS’ Gatekeeper vulnerability to get executed on victim’s machine without user permission or warnings. The MacOS X GateKeeper zero-day vulnerability was publically disclosed by Filippo Cavallarin on May 24, as
China Blamed for APT Attacks on Global Telcos
Security researchers have uncovered a major new two-year state-sponsored attack against global telcos, most likely linked to China’s Ministry of State Security (MSS). Boston-based vendor Cybereason claimed that the group used tools and techniques associated with APT10 to obtain Call
There’s been a 71% increase in open source-related breaches over the past five years, with UK firms downloading on average 21,000 software components known to be vulnerable over the past 12 months, according to Sonatype. The DevOps automation firm’s annual
Social Engineering Forum Suffers Major Breach
An online forum focused on discussion of all things social engineering has been breached, with the details of tens of thousands of account holders compromised. Social Engineered administrator “Snow101” explained to users in a post late last week that the
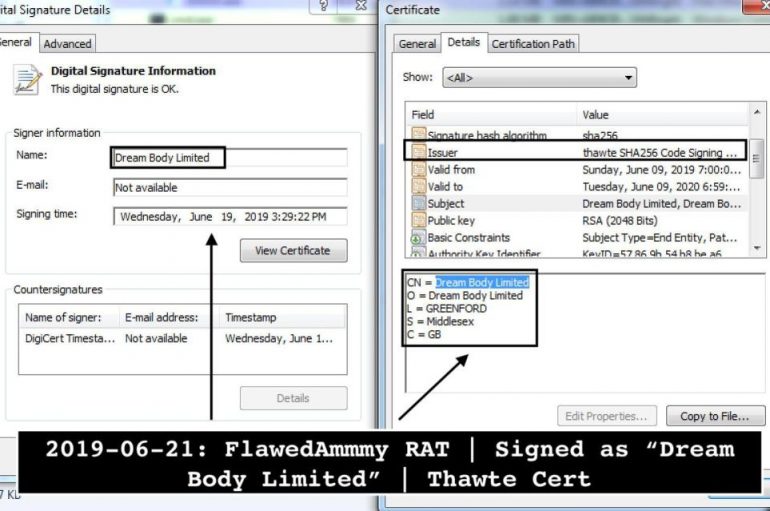
Researchers at Microsoft uncovered a malicious campaign that delivers the infamous FlawedAmmyy RAT directly in memory. Experts at Microsoft uncovered a malicious campaign that delivers the FlawedAmmyy RAT directly in memory. The FlawedAMMYY backdoor borrows the code of the Ammyy
Hacking software is not only used by hackers for criminal activities but it’s equally used by white hat hackers and security professionals to identify a vulnerability in a network or an endpoint. There is several hacking software available on the