Archive
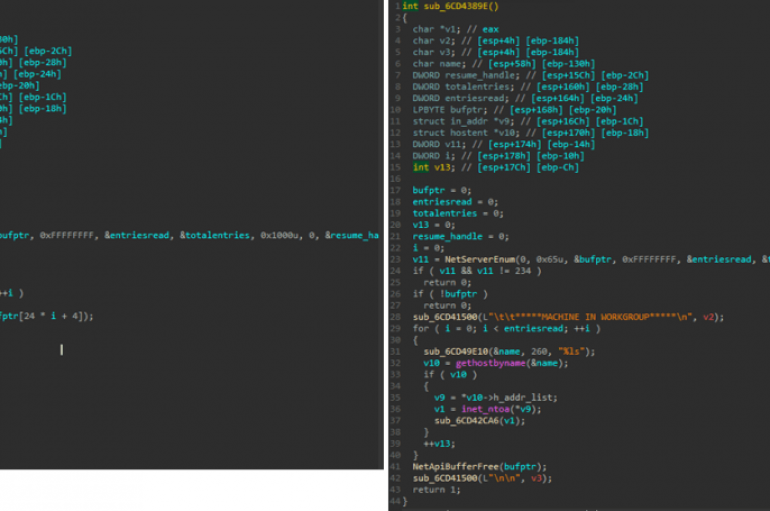
Kaspersky experts recently discovered a backdoor dubbed Plurox that can spread itself over a local network and can allow installing additional malware. Kaspersky experts discovered the Plurox backdoor in February, it can spread itself over a local network and could
OnePlus Phone Critical Security Vulnerability in Default Wallpapers App Leaks Users Email Address
A critical security flaw with OnePlus device wallpaper app Shot on OnePlus leaks hundreds of user’s email address. The flaw resides in the API that used to host the photos. The Shot on OnePlus is an application used to access
Accenture Acquires Deja vu Security
Deja vu Security has become a part of Accenture’s cyber-defense offerings through an acquisition announced on June 17. The Seattle-based Deja vu Security was founded in 2011 and has been providing a range of business application security solutions with a
Mozilla released a security update for Critical Zero-day vulnerability that fixed in a new version of Firefox 67.0.3 and Firefox ESR 60.7. Critical vulnerabilities can be used to run attacker code and install software, requiring no user interaction beyond normal
DNS Attacks Grow More Frequent and Costly
Domain name server (DNS) attacks have grown in frequency and cost, according to multiple research reports published this week. The Domain Fraud Threats Report from Proofpoint found that Chengdu West Dimension Digital, NameSilo, Public Domain Registry and GoDaddy are the
Researchers discovered a critical zero-day flaw in TP-Link Wi-Fi extender that allows a remote attacker to get complete control over the device and to execute commands in user privileges. This vulnerability can be tracked as CVE-2019-7406, and it affects the
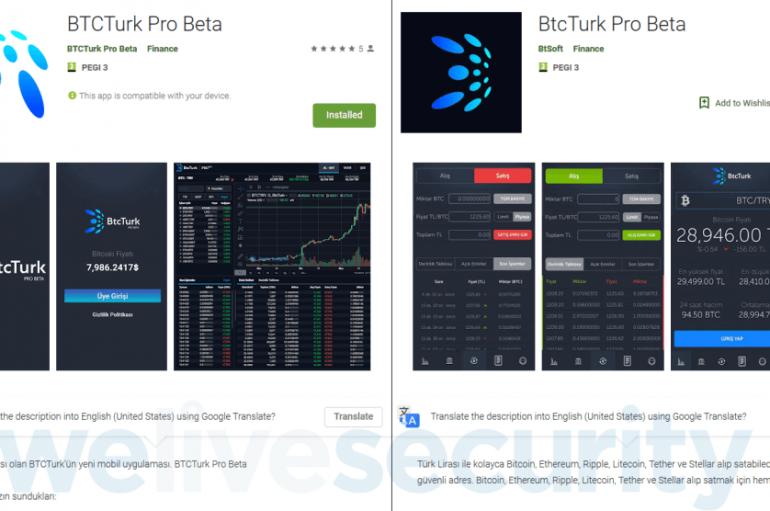
Expert discovered a new technique bypassing SMS-based two-factor authentication while circumventing Google’s recent SMS permissions restrictions The popular security expert Lukas Stefanko from ESET discovered some apps (namedBTCTurk Pro Beta and BtcTurk Pro Beta) impersonating the Turkish cryptocurrency exchange, BtcTurk,
Biometrics are seen as a positive step forward in authentication, but employees maintain privacy concerns. According to a survey of 4013 workers across the UK, France and the Netherlands, the Okta Passwordless Future Report found that 78% of respondents use
Trust remains the most important factor in enabling security and identity management. Speaking at the Okta Forum in London, Okta CEO Todd McKinnon said that every company is a technology company now, and if you are not a technology company
Researcher Leaked a Dataset of over 7,000,000 Transactions Scraped from the Venmo Public API
Researcher leaked online a dataset containing over 7,000,000 transactions scraped from the Venmo public API Venmo is a digital wallet app owned by PayPal that lets you make and share payments with friends. In August 2016, security expert Martin Vigo
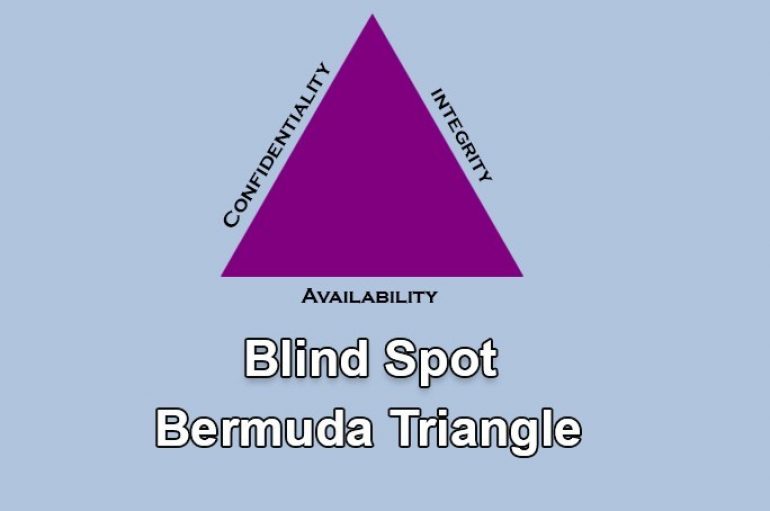
Inspection in detail is available for Packet’s behaviour, but unfortunately, there is no possibility or means to inspect a person’s Intention. ( CIA triangle ) The reason I selected this title “Blind spot in the Bermuda(CIA) triangle” is that we
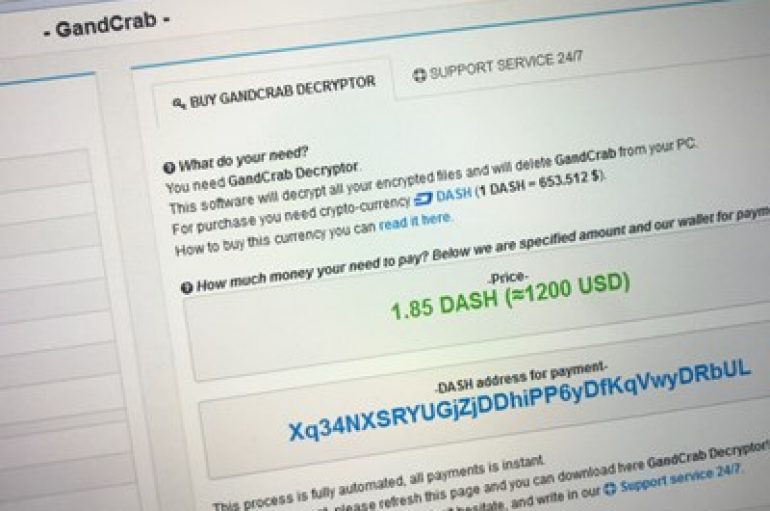
Infamous ransomware GandCrab could finally be on the way out, after white hats released yet another updated decryptor tool designed to help victims to get their data back. In partnership with various law enforcement agencies including Europol, the Metropolitan Police,
Oregon State Uni Attack Exposes Data on Hundreds
Another US university has been hit by a successful cyber-attack, this time potentially compromising personal information (PII) on hundreds of students and family members. Oregon State University (OSU) issued a public notice on Friday after one of its employee’s email
End of GandCrab – New Free Decryptor Tool that let Victims to Unlock All versions of Ransomware Infection
Decryptor tool released for the notorious GandCrab ransomware let’s victim’s to unlock the files infected with any version of GandCrab. The tools are available to download form Bitdefender and No More Ransom Project. Bitdefender, along with law enforcement agencies managed
Multiple Vulnerabilities with NETGEAR Wireless Routers Allows Attackers to Access Sensitive Information
Researchers discovered multiple vulnerabilities with some NETGEAR wireless routers that allow an attacker to access sensitive information. The vulnerability exists in the KCodes’ NetUSB kernel module. Only specific models of NETGEAR wireless routers use the kernel module from KCodes; the
Single Sign-on is a method of authentication process that helps to log in multiple application using single login credentials. Security is enhanced through Single Sign-on (SSO) in light of the fact that users are diminished of the various secret password