Russia-Linked Turla APT Group Hijacked C2 of the Iranian OilRig
Russia-Linked cyberespionage group Turla uses a new toolset and hijacked command and control infrastructure operated by Iran-Linked OilRig APT.
Russia-linked Turla cyberspiesused a new set of tools in new attacks and hijacked command and control infrastructure operated by Iran-Linked OilRig APT.
Recent campaigns demonstrate that Turla continues to evolve its arsenal and adopt news techniques to remain under the radar.
Turla (aka Snake, Uroburos, Waterbug, Venomous Bear and KRYPTON), has been active since at least 2007 targeting government organizations and private businesses.
The list of previously known victims is long and includes also the Swiss defense firm RUAG, US Department of State, and the US Central Command.
In June, ESET researchers observed the Russia-linked cyberespionage group using weaponizing PowerShell scripts in attacks against EU diplomats.
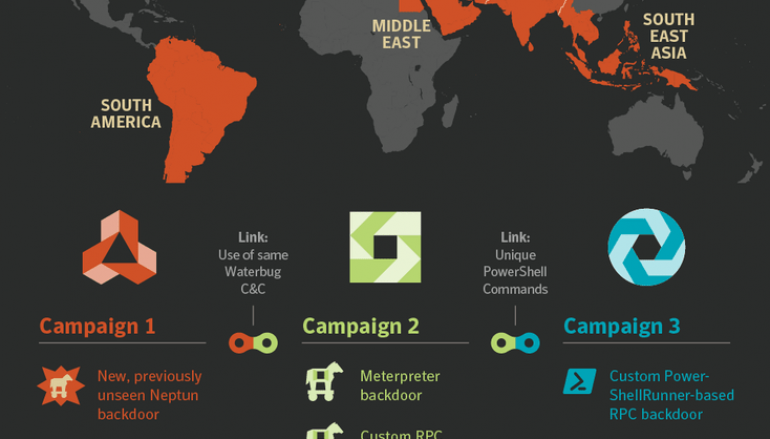
Experts at Symantec observed in the last eighteen months at least three distinct campaigns, each using a different set of hacking tools. In one campaign the attackers used a previously unseen backdoor tracker as Neptun (Backdoor.Whisperer), the malicious code is deployed on Microsoft Exchange servers and passively listen for commands from the attackers.
Experts noticed that in one attack, Turla hackers used the infrastructure belonging to another espionage group tracked as Crambus (aka OilRig, APT34).
In a second campaign, the group used three different backdoors, it involved a modified version of Meterprete, a publicly available backdoor, two custom loaders, a custom backdoor called photobased.dll, and a custom Remote Procedure Call (RPC) backdoor.
The third wave of attacks was characterized by the usage of another custom RPC backdoor, that borrowed the code derived from the PowerShellRunner tool to execute PowerShell scripts and bypass detection.
“Recent Waterbug activity can be divided into three distinct campaigns, characterized by differing toolsets.” reads the analysis published by Symantec. “One attack during this campaign involved the use of infrastructure belonging to another espionage group known as Crambus (aka OilRig, APT34).”

Turla attackers used many other tools and malware in the latest campaigns, such as a custom dropper to deliver the Neptun backdoor, a USB data collecting tool, a hacking tool that combines four NSA tools (EternalBlue, EternalRomance, DoublePulsar, SMBTouch)
Attackers also used a set of Visual Basic and PowerShell scripts for reconnaissance, and publicly available tools such as IntelliAdmin, SScan, NBTScan, PsExec, Mimikatz, and Certutil.exe.
The three recent Turla campaigns targeted governments and international organizations worldwide. Since early 2018, the cyberspies hit at least 13 organizations across 10 different countries:
- The Ministry of Foreign Affairs of a Latin American country
- The Ministry of Foreign Affairs of a Middle Eastern country
- The Ministry of Foreign Affairs of a European country
- The Ministry of the Interior of a South Asian country
- Two unidentified government organizations in a Middle Eastern country
- One unidentified government organization in a Southeast Asian country
- A government office of a South Asian country based in another country
- An information and communications technology organization in a Middle Eastern country
- Two information and communications technology organizations in two European countries
- An information and communications technology organization in a South Asian country
- A multinational organization in a Middle Eastern country
- An educational institution in a South Asian country
“This is the first time Symantec has observed one targeted attack group seemingly hijack and use the infrastructure of another group. However, it is still difficult to ascertain the motive behind the attack. Whether Waterbug simply seized the opportunity to create confusion about the attack or whether there was more strategic thinking involved remains unknown.” Symantec concludes.
“Waterbug’s ever-changing toolset demonstrates a high degree of adaptability by a group determined to avoid detection by staying one step ahead of its targets.”
This post Russia-Linked Turla APT Group Hijacked C2 of the Iranian OilRig originally appeared on Security Affairs.