Mac password-stealing malware haunts Transmission app… again
To have the official distribution of your Mac software hacked to include malware once may be regarded as a misfortune; to have it happen twice looks like carelessness.
(With apologies to Oscar Wilde.)
The first time it happened to popular BitTorrent client Transmission was back in March 2016.
For a short while, the Mac version of Transmission 2.90 on the official download site was a not-so-official version that had some secret sauce of its own: OS X ransomware called OSX/KeRanger-A.
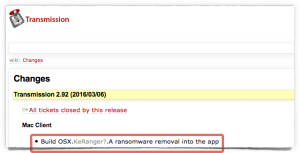
This time, for less than 24 hours on 28 August 2016 and 29 August 2016, a bogus version of Transmission 2.92 was uploaded that contained malware known as OSX/PWSSync-B.
Ironically, the main feature added when 2.92 was released, and the main reason you might have updated, was to a malware removal utility for KeRanger, in case you had a leftover infection from the hacked 2.90 version:
PWS, by the way, is short for password stealer, so you can guess the primary function of the malware; it is also known as “Keydnap”, a name that explains itself (say it out loud quickly).
The hack that was applied to the Transmission app this time is very similar to the previous attack.
The hacked Transmission program itself contains only a tiny change: a small snippet of code added at the start that loads a file called License.rtf that is packaged into the application bundle. (Last time, the sneaky extra file was General.rtf.)
Source | nakedsecurity