Archive
Researchers remotely hack Tesla Model S
Chinese researchers announced Monday that they had discovered security vulnerabilities in the Tesla Model S that allowed them to take over the vehicle’s brakes and more without laying a finger on the car. While other researchers have hacked into Tesla vehicles, this appears
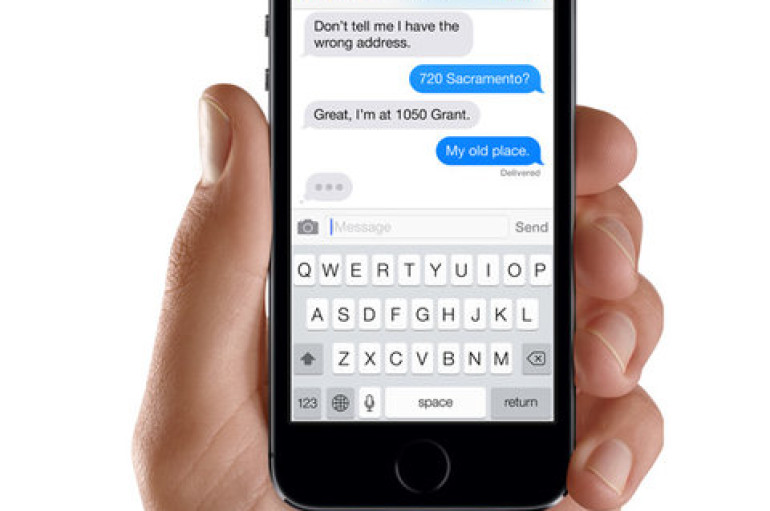
Doing conversations with your friend on iMessage and thinking that they are safe and out of reach from anyone else other than you and your friend? No, it’s not. End-to-end encryption doesn’t mean that your iMessages are secure enough to
OSquery, an open-source framework created by Facebook that allows organizations to look for potential malware or malicious activity on their networks, was available for Mac OS X and Linux environments until today. But now the social network has announced that
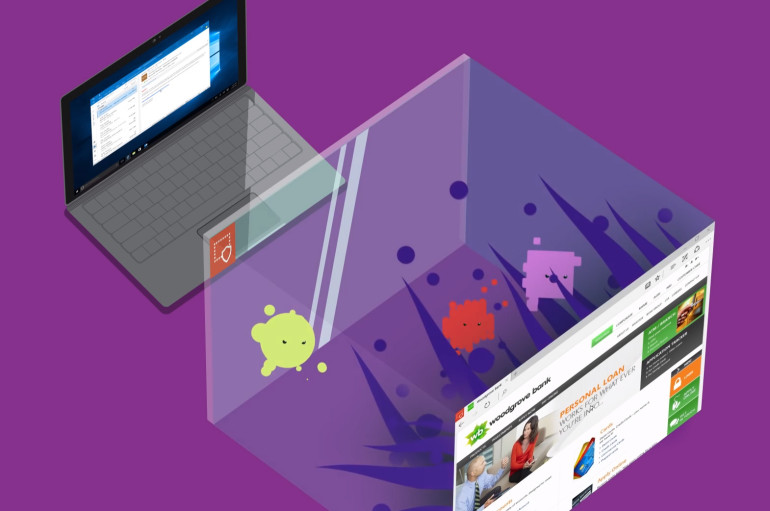
Microsoft is putting Edge in a virtual machine to protect users from malware, viruses, phishing and zero-days. Microsoft has developed a new update for its Windows 10 operating system that will place the Edge web browser inside a virtual machine
A new active ransomware campaign has been detected targeting US government and educational institutions. The ransomware was dubbed MarsJoke after researchers uncovered a “string contained within the code: ‘HelloWorldItsJokeFromMars’”. The ransomware gives victims 96 hours to pay up the ransom,
Cisco Cracks GozNym Trojan DGA, Sinkholes Botnet
An extensive analysis of the hybrid Trojan dubbed GozNym has allowed Cisco researchers to reverse engineer its domain generation algorithm (DGA) and start sinkholing botnets that rely on the malware. The existence of GozNym, which is a combination between the
A Norwegian court on Wednesday dismissed a fresh bid by fugitive whistleblower Edward Snowden to win assurances he would not be extradited to the US should he come to Norway to collect an award. The Oslo appeals court said it
Researchers at Palo Alto Networks have come across an OS X Trojan they believe has been used by a notorious Russia-linked cyber espionage group in attacks aimed at the aerospace industry. The malware, dubbed “Komplex,” appears to have been developed
Land Registry warns on property phishing scam
The Land Registry is warning its users not to fall for a new phishing scam which imitates a request for property ownership information. The latest phishing emails state: “The document attached is an official requisition, reminder or letter from Land
Do you know — Your Smart Devices may have inadvertently participated in a record-breaking largest cyber attack that Internet has just witnessed. If you own a smart device like Internet-connected televisions, cars, refrigerators or thermostats, you might already be part
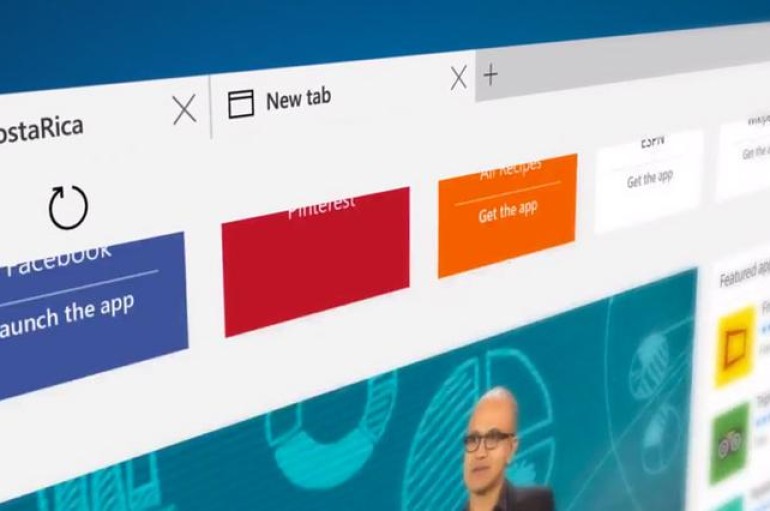
Microsoft Boosts Edge Browser Security
Microsoft is giving its Edge browser a security boost with Windows Defender Application Guard for Windows 10 Enterprise. Other browsers use software-based sandboxes to stay segregated from sensitive areas of the PC, but they “still provide a pathway for malware
If you are a hacker, you might have enjoyed the NSA’s private zero-day exploits, malware and hacking tools that were leaked last month. But the question is: How these hacking tools ended up into the hands of hackers? It has
A mother from Austin, Texas, said she had to take down her baby monitor for good after she discovered that someone had hacked it and taken control over the device more than one time. The mother, who wanted to remain
Hackers can use leaked NSA tools to do their dirty work. Hackers using NSA-related hacking tools could exploit a major cyber security vulnerability impacting hundreds of thousands of Cisco switches, routers, and other networking gear. The vulnerability, disclosed by Cisco
When we talk about protecting your money, debit and credit card fraud have always been one of the primary concerns. But there’s now a new threat to your wallet that’s becoming an increasingly popular way for criminals to get access
500 million accounts — that’s half a Billion users! That’s how many Yahoo accounts were compromised in a massive data breach dating back to 2014 by what was believed to be a “state sponsored” hacking group. Over a month ago,