Posts From Seid Yassin
SynAck targeted ransomware was seen in the wild using the Doppelgänging technique which was first presented as a proof of concept in December 2017. SynAck targeted ransomware was seen in the wild using the Doppelgänging technique which was first presented
The ISO has brought together a team of privacy experts to develop the first set of preventative international guidelines to ensure consumer privacy is embedded into the design of a product or service. Cyber-security professionals have long been lamenting the
Pentagon Bans Huawei and ZTE Devices from Bases
The US has turned up the pressure on Chinese technology firms after the Department of Defense ordered all military bases to stop selling Huawei and ZTE devices out of security concerns. The Pentagon is also said to be considering whether
Warren Buffett: Cybersecurity risk ‘is uncharted territory. It’s going to get worse, not better’
Warren Buffett believes cybersecurity incidents will rise, and with it the potential to significantly harm the insurance industry. “Cyber is uncharted territory. It’s going to get worse, not better,” he said at the Berkshire Hathaway 2018 Annual Shareholders Meeting Saturday.
Not long after the Russian government ordered the immediate blocking of the Telegram messaging app from the Apple App Store and Google Play Store, an imitation of the popular app made its rounds on Google Play. Confusion surrounding the prompt
Whether serendipitous or ironic, Global Password Day found Twitter advising users to change their passwords after a bug in its password storage system “unmasked” the passwords in an internal log. “We have fixed the bug, and our investigation shows no
What is Blockchain Technology?
Tips for Entering the Penetration Testing Field
OWASP TOP 10 VULNERABILITIES
The 13 Most Helpful Pentesting Resources
Cybersecurity Fundamentals Glossary
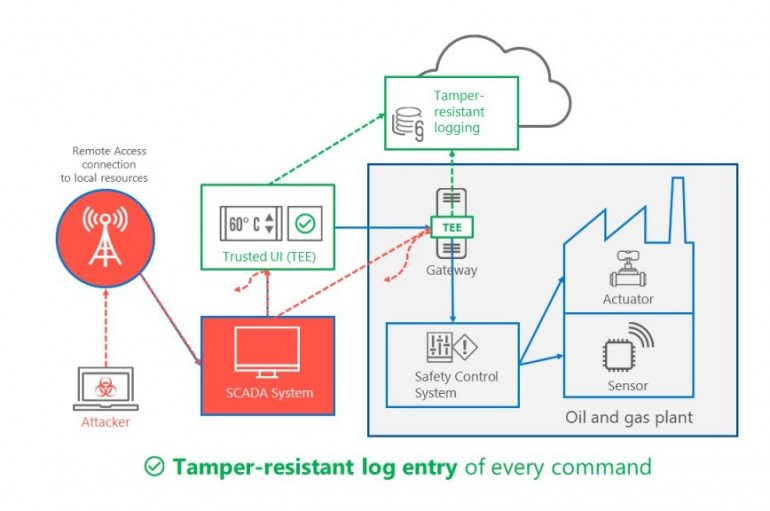
Microsoft last week unveiled Trusted Cyber Physical Systems (TCPS), a new solution designed to help protect critical infrastructure against modern cyber threats. Microsoft provided the recent Triton and NotPetya attacks as examples of significant threats hitting critical infrastructure. Triton was
The world’s largest online marketplace for selling and lauching distributed denial-of-service (DDoS) attacks was shut down this week as part of Operation Power Off, an international investigation into the so-called Webstresser.org site. The effort was led by the UK National
GravityRAT, a remote access trojan targeting organisations across India, boats an unusual trick for evading analysis: taking a reading of the target computer’s temperature. The trojan only detonates its payload if the thermal reading is below a certain level, because
If you receive a link for a video, even if it looks exciting, sent by someone (or your friend) on Facebook messenger—just don’t click on it without taking a second thought. Cybersecurity researchers from Trend Micro are warning users of
Alexa Turned Spy, Able to Snoop on Users
Amazon put a quick stop to an issue in Alexa’s skill set after Chexmarx researchers reported that her skill set could be expanded to listen in on users not just some of the time but all of the time. According to a Checkmarx research