Microsoft Unveils New Solution for Securing Critical Infrastructure
Microsoft last week unveiled Trusted Cyber Physical Systems (TCPS), a new solution designed to help protect critical infrastructure against modern cyber threats.
Microsoft provided the recent Triton and NotPetya attacks as examples of significant threats hitting critical infrastructure. Triton was used in a highly targeted campaign aimed at an organization in the Middle East, while NotPetya disrupted the operations of several major companies, with many reporting losses of hundreds of millions of dollars.
Microsoft’s TCPS project aims to address these types of threats by providing end-to-end security through hardware, software and trust mechanisms that should help organizations ensure they don’t lose control over critical systems.
Cyber-physical systems (CPS) are referred to as Internet-of-Things (IoT) in an industrial context. TCPS is based on four main principles: separating critical from non-critical operations through hardware isolation; ensuring that the code responsible for critical operations can be audited; the ability of each component to process data only from trustworthy sources and each component being able to attest its trustworthiness to other components; and reducing the attack surface by reducing the number of trusted entities.
One crucial component in providing end-to-end security involves trusted execution environments (TEE), Microsoft said. TEE includes Secure Elements (e.g. chip on a credit card), Intel’s Software Guard Extensions (SGX), ARM TrustZone, and Trusted Platform Modules (TPMs) and DICE-capable microcontrollers from the Trusted Computing Group.
TEE offers several advantages from a security viewpoint, including the fact that code running in a TEE is small and thus has a minimal attack surface, the code is considered trusted, all the data is encrypted, and the TEE hardware ensures that software running outside the trusted environment cannot break in.
Microsoft has pointed out that organizations can acquire low-cost devices with TEE and deploy them without making major changes to existing systems.
The tech giant’s TCPS solution leverages TEE to protect a wide range of components, including cloud services, human interaction devices, and edge computing devices. For instance, in the case of public and private clouds, a TEE that is protected from hosting providers and OS vendors can be used for various critical operations, including key and certificate management, provisioning, patch management, and logging.
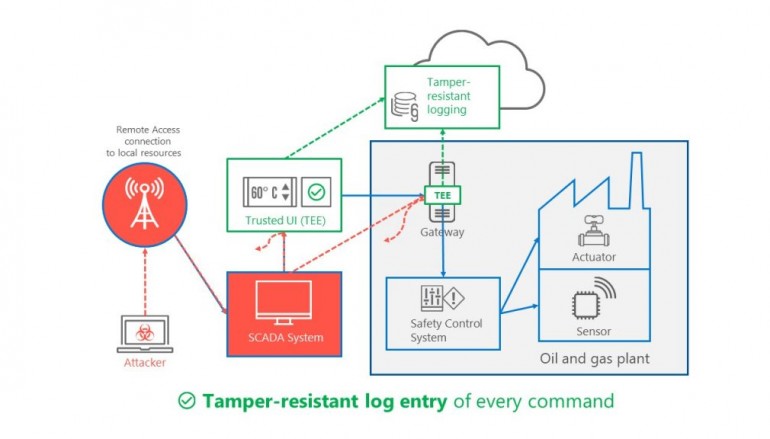
In the case of physical security controls – for example, preventing unauthorized users or malware from tampering with electronically-controlled actuators or sensors – Microsoft says the connection to the system needs to be accessible only from the TEE. In order to avoid replacing existing and potentially expensive equipment, a TEE gateway can be deployed in front of the device.
As for human interfaces, the company points out that there is the risk of a compromised user device or SCADA system sending legitimate-looking arbitrary commands. Microsoft says this can be addressed by using a secure confirmation terminal, a device that displays a message and asks for confirmation if an unusual operation is detected. The TEE can help in this case by ensuring that the display and the input system on the secure confirmation terminal are only accessible from the trusted environment and out of malware’s reach.
Source | securityweek




