Posts From CCME
Security experts at Morphisec observed a wave of attacks against point-of-sale (PoS) thin clients using card data scraping malware and the Cobalt Strike beacon. Over the past 8-10 weeks, security experts at Morphisec observed multiple sophisticated attacks targeting PoS thin
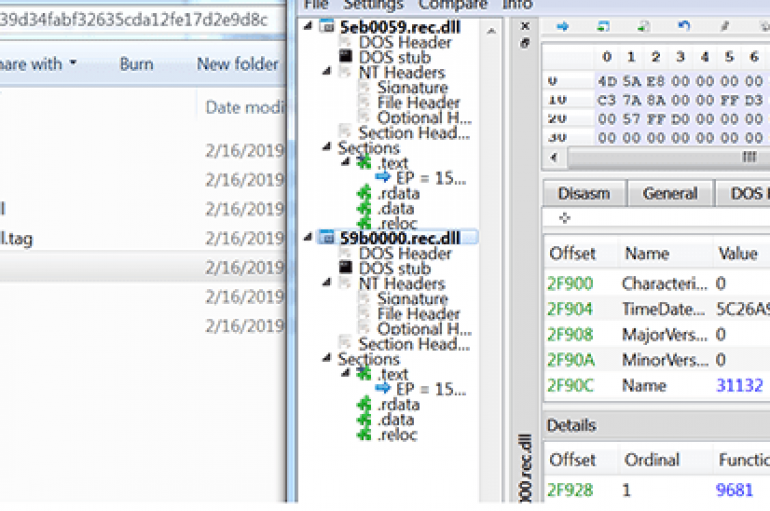
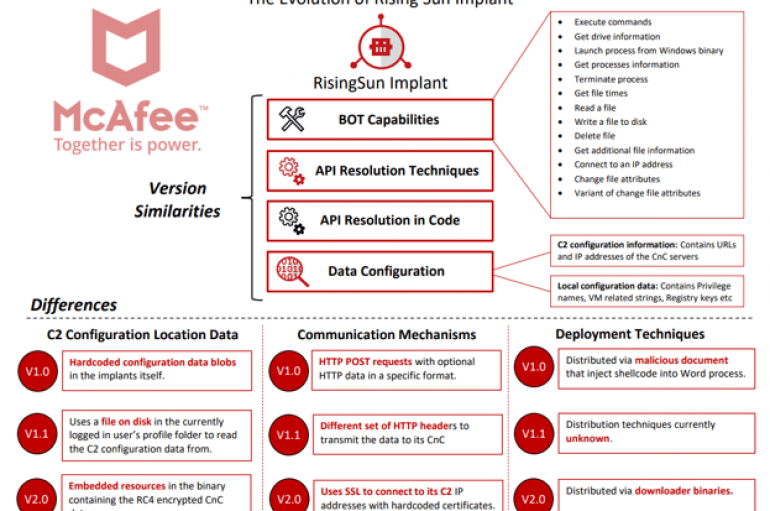
Security experts at McAfee analyzed the code of a C2 server involved in the cyber espionage campaign tracked as Op. Sharpshooter and linked it with the North Korea-linked APT group McAfee worked with a government entity and discovered that the
Security breaches linked to open source software components have risen by 71% over the past five years, as securing applications continues to be a challenge for many organizations, according to Sonatype. The DevOps automation firm has been running its global
A 2016 cyber-attack that resulted in a major data breach for the International Civil Aviation Organization (ICAO), believed to be the work of a hacker associated with Emissary Panda, should have been prevented, according to the CBC. Documents resulting from
Still Room To Improve Data Breach Readiness
While many companies have taken impressive steps in an effort to prepare themselves for the likely inevitability of a data breach, a new study from Experian found that more work needs to be done. To understand what organizations have done,
Ten years of cloud computing have brought about a change in understanding, DevOps, new risk strategies and regulations. Speaking on a panel marking the tenth anniversary of the Cloud Security Alliance, moderator Becky Swain, GRC and cloud security assurance consultant,
Speaking at BSidesSF Stina Ehrensvard, CEO and founder of Yubico, and co-inventor of the YubiKey – a small hardware-based authentication device – outlined how online identities can be protected with simple, secure open standards. Ehrensvard explained that security needs to
Speaking at the CSA Summit, Cloud Security Alliance founder member and ACLU technology fellow Jon Callas tackled the question on whether the future of privacy is “Futile or Pretty Good?” He claimed that it is “really easy to be nihilistic
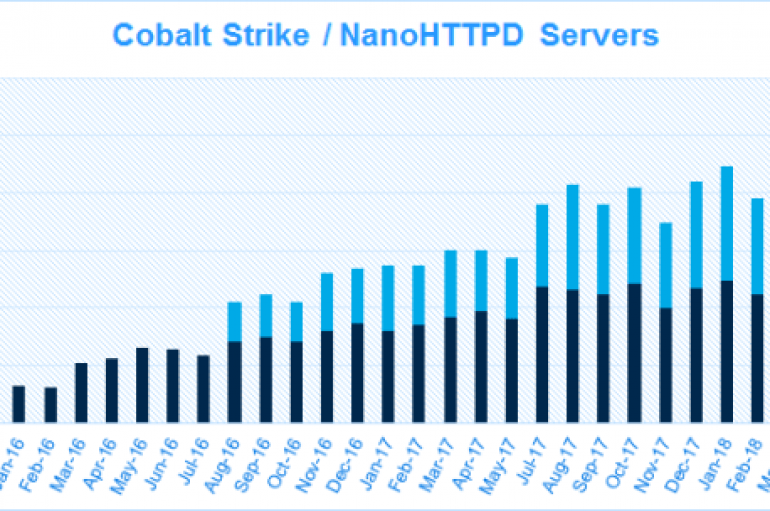
According to security experts at Fox-IT, a recently addressed flaw in the Cobalt Strike penetration testing platform could be exploited to identify attacker servers. Security experts at Fox-IT discovered that a recently addressed vulnerability in the Cobalt Strike penetration testing
SSL-Based Phishing Surges 400% from 2017
Hackers are increasingly using encrypted traffic to hide their attacks from security filters, with phishing emails soaring in popularity, according to new data from Zscaler. The cloud security provider processes more than 60 billion transactions per day and claimed that
Dow Jones Partner Leaks Global Watchlist Data
Dow Jones has landed itself in trouble again after an authorized third party accidentally left a highly sensitive list of criminals, terrorists and dodgy businesses on a publicly accessible cloud server. The list, which contained over 2.4 million records, was
Tik Tok Kids’ App Hit by Record $5.7m FTC Fine
US regulators have handed a Chinese-owned social networking app a record fine after it illegally collected the personal data of children who used it. A Federal Trade Commission notice issued this week revealed that Music.ly, now incorporated into Tik Tok
The Wireshark Foundation released Wireshark 3.0.0, the latest release of the popular open-source packet analyzer. The Wireshark Foundation announced the release of Wireshark 3.0.0, the latest release of the popular open-source packet analyzer. The new version addresses several bugs and
Bug bounty platform HackerOne announced that two of its members have each earned more than $1 million by participating bug bounty programs. Bug bounty programs could be a profitable activity, the popular bug bounty platform HackerOne announced that two of
Sextortion Scammers Target Employees
Corporate employees are more likely to receive a sextortion scam today than an impersonation or Business Email Compromised (BEC) attack, according to new data from Barracuda Networks. The security vendor analyzed malicious emails sent to its customers and found one
Even though misconfigurations in public clouds create risks to enterprise security, a new study found that more than half of IT professionals do not really understand the risks inherent in public cloud misconfigurations as well as they understand risks within