Recently Cloud Atlas Used a New Piece of Polymorphic Malware
Cloud Atlas threat actors used a new piece of polymorphic malware in recent attacks against government organizations.
The Cloud Atlas cyberespionage group, aka Inception, continues to carry out attacks against government organizations and was observed using a new piece of polymorphic malware dubbed VBShower.
The Cloud Atlas was first observed by researchers at Kaspersky Lab back in 2014, at the time the group was targeting government, diplomatic and research organizations. The campaign was dubbed by Kaspersky the return of Red October because the attackers targeted the same organizations of the previous campaign.
“From the beginning of 2019 until July, we have been able to identify different spear-phishing campaigns related to this threat actor mostly focused on Russia, Central Asia and regions of Ukraine with ongoing military conflicts.” reads the report published by Kaspersky Lab.
“Cloud Atlas hasn’t changed its TTPs (Tactic Tools and Procedures) since 2018 and is still relying on its effective existing tactics and malware in order to compromise high value targets.”
Most of the victims of the group were located in Russia, followed by Kazakhstan, Belarus, India and the Czech Republic. Over the year the group also targeted entitied in Ukraine, Moldova, Belgium, Iran, France, the United States, Turkey, Georgia, and Bulgaria.
Now the group continues to be mainly focused on Russia, but other victims were reported by Kaspersky in Kyrgyzstan, Turkmenistan, Ukraine, Turkey, Romania and Portugal. Most of the victims belong to government organizations, but researchers observed that attacks against Russian entities hit religious organizations, the aerospace industry and an international organization.
The Cloud Atlas attacks still leverage spear-phishing messages to target high profile victims. These emails are crafted with Office documents that use malicious remote templates that were hosted on remote servers.
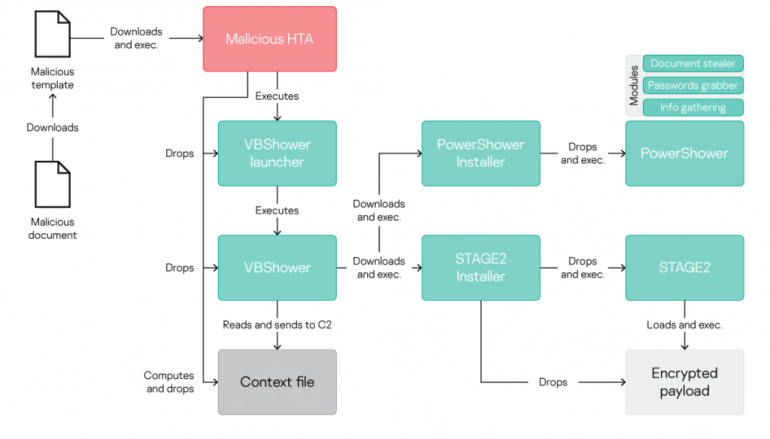
In past attacks, Cloud Atlas was delivering a “validator” implant tracked as “PowerShower” by chaining the CVE-2017-11882 and the CVE-2018-0802 issues. Recently Kaspersky has observed the threat actor adopting a new infection chain, involving a polymorphic HTA, a new and polymorphic VBS implant used to deliver the PowerShower, and a second stage modular backdoor that we first detected five years ago.
The threat actors were using the PowerShower malware since October 2018. The malicious code allows fetching PowerShell and VBS modules that can be executed on a compromised machine to gather intelligence and exfiltrate data.
Since April 2019, Kaspersky researchers have observed the Cloud Atlas group using a new piece of malware tracked as VBShower in a new “polymorphic” infection chain. Cloud Atlas attackers were using a polymorphic HTA hosted on a remote server, which is used to drop the following different files on the local system:
- A backdoor tracked as VBShower which is polymorphic and replaces PowerShower as a validator;
- A tiny launcher for VBShower ;
- A file computed by the HTA which contains contextual data such as the current user, domain, computer name and a list of active processes.
The “polymorphic” infection chain allows evading detection based on IoCs. Experts pointed out that each code is unique by victim.


“The VBShower backdoor has the same philosophy of the validator version of PowerShower. Its aim is to complicate forensic analysis by trying to delete all the files contained in “%APPDATA%..LocalTemporary Internet FilesContent.Word” and “%APPDATA%..Local SettingsTemporary Internet FilesContent.Word”. ” continues the analysis.
Kaspersky confirmed that Cloud Atlas attackers appeared to be Russian-speaking, but the security firm did not link it with any government.
“Cloud Atlas remains very prolific in Eastern Europe and Central Asia. The actor’s massive spear-phishing campaigns continue to use its simple but effective methods in order to compromise its targets.” concluded Kaspersky.
“Unlike many other intrusion sets, Cloud Atlas hasn’t chosen to use open source implants during its recent campaigns, in order to be less discriminating. More interestingly, this intrusion set hasn’t changed its modular backdoor, even five years after its discovery.”
This post Recently Cloud Atlas Used a New Piece of Polymorphic Malware originally appeared on Security Affairs.