Is Emotet Gang Targeting Companies with External SOC?
Introduction
The group behind Emotet malware is getting smarter and smarter in the way they deliver such a Malware. While the infection schema looks alike from years; the way the group tries to infect victims improves from day to day.
Today I’d like to share a quick analysis resulted by a very interesting email which claimed to deliver a SOC “weekly report” on the victim email. First of all the attacker knew the target organization was protected by a SOC (Security Operation Center) so she sent a well crafted email claiming to deliver a Microsoft document wrapping out the weekly SOC report as a normal activity in order to induce the victim to open-it.
SOC report 10 12 2019.doc (
6125489453c1824da3e28a54708e7c77875e500dd82a59c96c1d1e5ee88dcad7
) is the delivered file sent on Oct 11, 2019, 11:06:09 PM from
grecia@ambientehomedecor.com
. I believe that
ambientehomedecor.com
is not a malicious domain but mostly a new compromised one.
Technical Analysis
Hash 6125489453c1824da3e28a54708e7c77875e500dd82a59c96c1d1e5ee88dcad7
Threat Word document Dropper (Emotet)
Brief Description First stage of Emotet campaign targeting organization with Security Operation Centers
Ssdeep 6144:tkPNPASKUzSRnLx3Q4td9pB8LGme764XNNHBly:tkPNPAfUGRt3b3B8LGL6CNJ
Following the original eMail headers from
grecia@ambientehomedecor.com
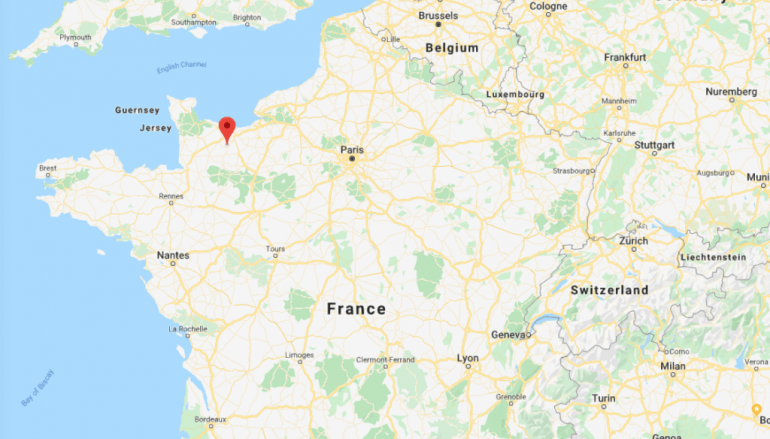
to victim’s email box it is possible to figure-out the attacker used a SMPT client who left trace about the original sender IP address which happens to be:
81.48.36.59
. According to IPLocation that address is related to a very nice town in northern France: Thury-Harcourt, France.
The attached document is a well obfuscated Microsoft Word document which asks to enable macros in order to view its content. The
autoopen
function begins a complex obfuscated chain which tries to deter analyst by introducing junk code, junk variable assignments and fake apparent real comments. The following image proves the adopted obfuscation technique. The function
c878cxx90590
is the “Real Code” by meaning is not part of junk code but actually is the function who really performs malicious actions. As you might see being in the middle of hundreds similar lines of code it gets hard to spot.
The obfuscated macro creates on-memory objects and runs them without passing through temporary files. The following image shows the auto-run created object before the Drop’n Execute. The analysed variable in the following image is the
c0639047895c6
which, in that specific run, holds the Win32_ProcessStartup created Object for fulfill persistence on the victim machine.
Once the dropper assured the persistence and to run during the start-up, it carves from itself the following powershell script. The script runs an encoded string hiding the dropping ULRs. The base64 decoded string shows a romantic
foreach
statement looping through a list of compromised websites hosting the real payload :
de6a8b8612b5236a18eea1a6a8f53e117d046cf2ad95e079a6715af68f8d2216
(VT 6/69). It finally saves the dropped file in a userprofile location as placed in the variable
xc0x57b38b2x7
, before running it. The following image shows the powershell script before and after the encoding by giving a quick description on it.
According to VT, the final run looks like Emotet, a banking trojan who steals credentials, cookies and eCoin wallets. Emotet is also able to access to saved credentials of the major browser like Chromium, Firefox, Opera, Vivaldi to exfiltrate cookies, and to send back to command and control found victim information. But let’s try to quickly check it.
Analysis of dropped and executed file (emotet)
Hash de6a8b8612b5236a18eea1a6a8f53e117d046cf2ad95e079a6715af68f8d2216
Threat Emotet. Data Exfiltration
Brief Description Dropped and Executed by previous stage
Ssdeep 3072:2xUIvfl2nnKJFddS2TZGjRurmOEfRtaG/70Jfm4JuLYwO9/+Tl:2lvfUnKJFddhAjYrmOEpzcflQu1+
The dropped file (VT 12/69), grabbed from the dropping URLs inside the previous powershell script, is an executable packed by internal functions which uses several techniques to avoid static and dynamic analysis. For example it deletes the original file once executed, it resolves an unusual very high number of APIs and it dynamically resolves functions avoiding static analysis.
During the running phase the analyzed sample records many information on the hosting machine, it asks for local public IP address by querying an external resource: http[://185[.42[.221[.78:443/whoami.php and finally it pushes out those information to external Command and Control (please refer to IoC section for the complete C2 list).
The sample starts a local service called
khmerdefine
and assures its persistence by adding that file in
c:\Windows\SysWOW64
and setting up a system service in autorun. AV and plenty static traffic signatures confirm we are facing a new encrypted version of Emotet trojan.
Conclusion
Emotet gang is getting smarter and smarter in delivery artifacts. That time they addressed companies having an external Security Operation Center (SOC) pretending to simulate an external SOC operator who sends periodic reports to the company. The delivery content was a Microsoft word document within heavily obfuscated Macros who eventually drops and executes Emotet Malware. The following image represent the compiled MITRE ATT&CK matrix in order to qualify stages and to describe the overall behavior.
This post Is Emotet Gang Targeting Companies with External SOC? originally appeared on Security Affairs.