Posts From CCME
Hackers compromised a network of ‘camgirl’ sites and exposed data belonging to millions of users and sex workers. Hackers compromised several ‘camgirl’ sites and have exposed millions of sex workers and users. All the sites were run by the Spanish
There is a sense of failure among security practitioners, believing that they cannot keep up with attacks, and this has created a sense of irrational fear. Speaking at the Tenable Edge conference in London, Tenable CEO Amit Yoran said that
Sumo Logic Acquires JASK
Californian security-event management company Sumo Logic has acquired JASK Labs, Inc. JASK makes security information and event management (SIEM) software and is best known for its flagship product, JASK Autonomous Security Operations Center (ASOC), which collects and analyzes data from
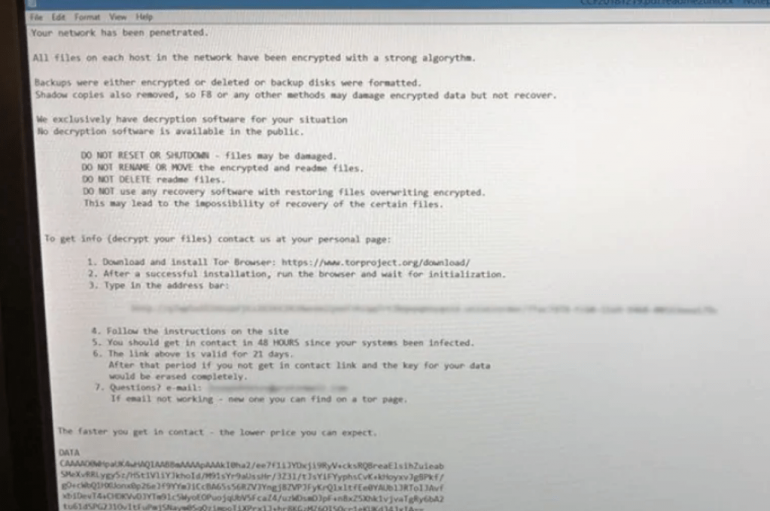
A ransomware attack disrupted IT operations in the territory of Nunavut (Canada), all government services requiring access to electronic data were impacted. A ransomware attack disrupted IT operations in the remote Canadian territory of Nunavut, all government services requiring access
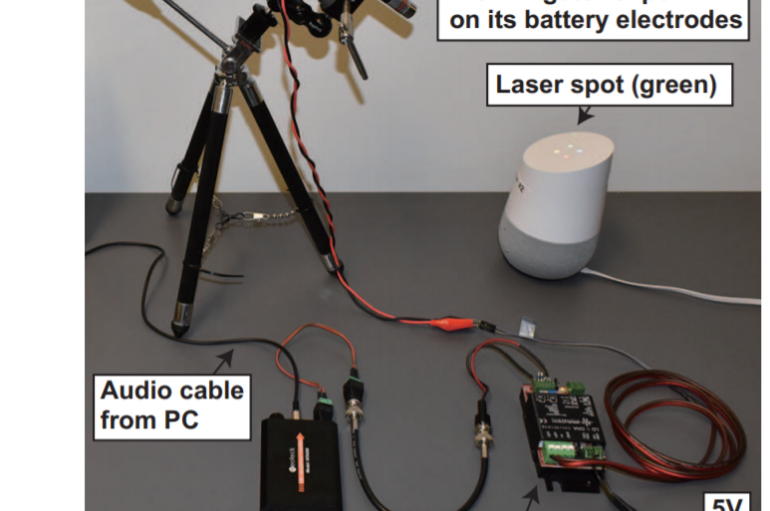
Experts demonstrated that is possible to hack smart voice assistants like Siri and Alexa using a lasers beam to send them inaudible commands. Researchers with the University of Michigan and the University of Electro-Communications (Tokyo) have devised a new technique,
Attack on Indian Ed Tech Firm Exposes 687K Users
An Indian ed tech provider suffered a serious data breach months ago impacting hundreds of thousands of customers, but is only now informing them of the incident. Vedantu offers a real-time online learning environment for teachers and students from its
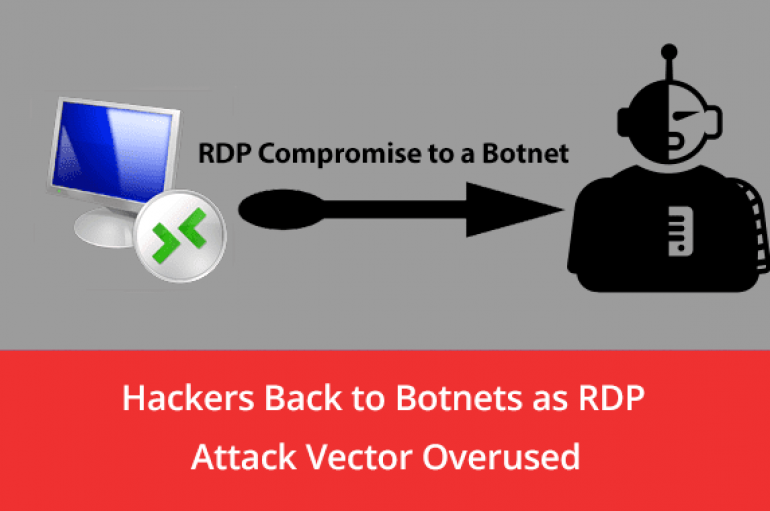
Hackers Changing the Main Attack Vector from RDP Compromise to Botnets For Network Breach
The ransomware evolution re-shaping the cyber domain, starting from 2019 the ransomware attacks against high-profile public and corporate networks by making criminal alliances. In 2018, threat actors behind GandCrab ransomware launched their Ransomware-as-a-Service which shifts the paradigm and turns the
UK Launches Cyberhood Watch
Community safety organization Neighbourhood Watch has established a cyber-safety initiative to help Brits protect themselves and their families from online crime. The UK’s largest voluntary movement teamed up with antivirus brand Avast to create the UK Cyberhood Watch. Formed in
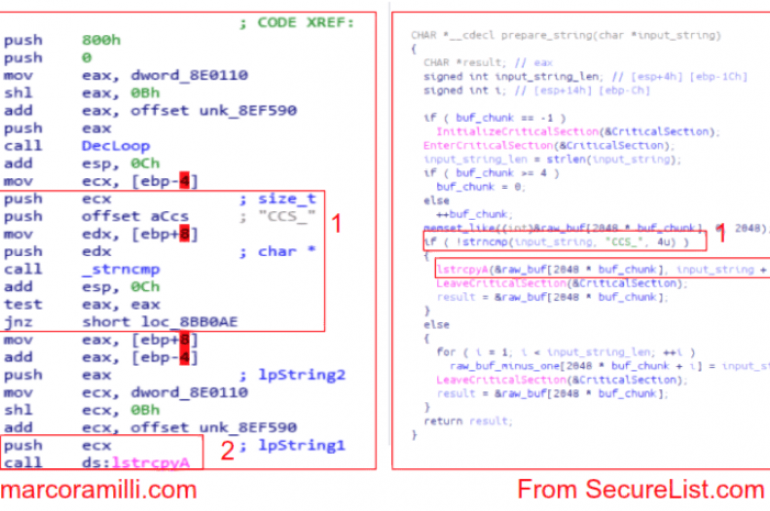
DarkUniverse – The Mysterious APT Framework #27
In April 2017, ShadowBrokers published their well-known ‘Lost in Translation’ leak, which, among other things, contained an interesting script that checked for traces of other APTs in the compromised system. In 2018, we found an APT described as the 27th
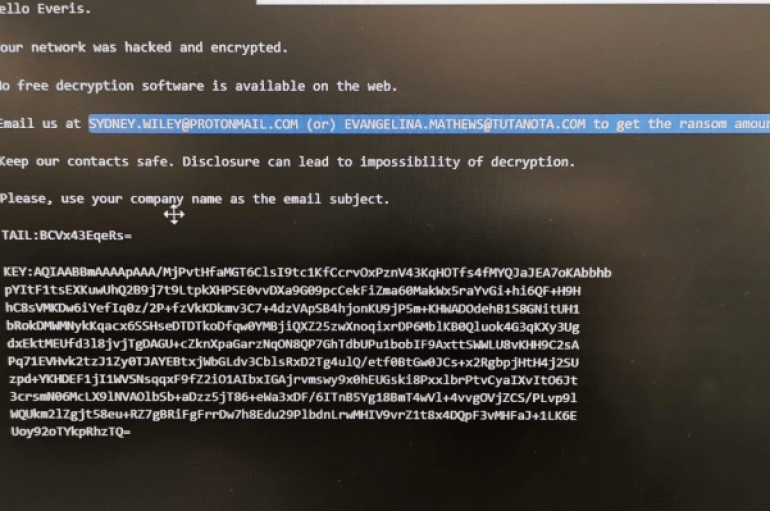
NTT DATA-owned firm Everis is one of Spain’s largest managed service providers (MSP), it has suffered a ransomware attack, and it was not the only case. Systems at Spain’s largest managed service providers (MSP) Everis have been infected by a
The popular rConfig network configuration management utility is affected by two critical remote code execution flaws that have yet to be patched. rConfig is a completely open-source, network configuration management utility used to validate and manage network devices, including switches,
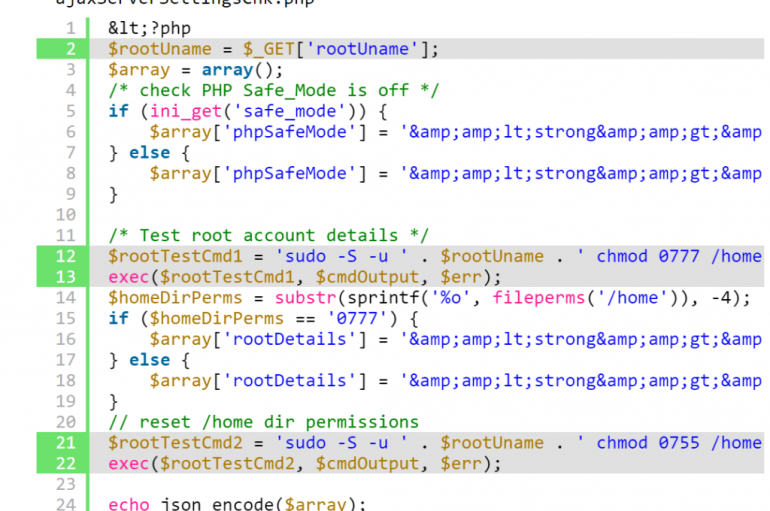
Expert Marco Ramilli and his team analyzed the sample that infected systems at the Kudankulam Nuclear Power Plant, it is a targeted attack. During the past few days a cyber attack hit Kudankulam Nuclear Power Plant: the largest nuclear power
Malware delivery trends change every day. For the last few years, we have observed various hacker groups like ( APT12 to Turla ) uses various techniques to deliver malware on the system or network. One of the best technique hackers
Security researchers spotted the first mass cyberattack campaign exploiting BlueKeep RDP Flaw to install a cryptocurrency miner on the vulnerable installations. Bluekeep(CVE-2019-0708) is a wormable critical RCE vulnerability in Remote desktop services that let hackers access the vulnerable machine without
A Pentagon advisory board has published a set of guidelines on the ethical use of artificial intelligence (AI) during warfare. In “AI Principles: Recommendations on the Ethical Use of Artificial Intelligence by the Department of Defense,” the Defense Innovation Board
WP Hardening – A Free WordPress Security Plugin to Perform Real-time Security Audit On Your WordPress Site
An average WordPress owner does not know what to do to ensure their WordPress’s security. Those who do know still does not imply. We tried to find the reason behind this erratic behavior. And the results, while not completely unexpected