Posts From CCME
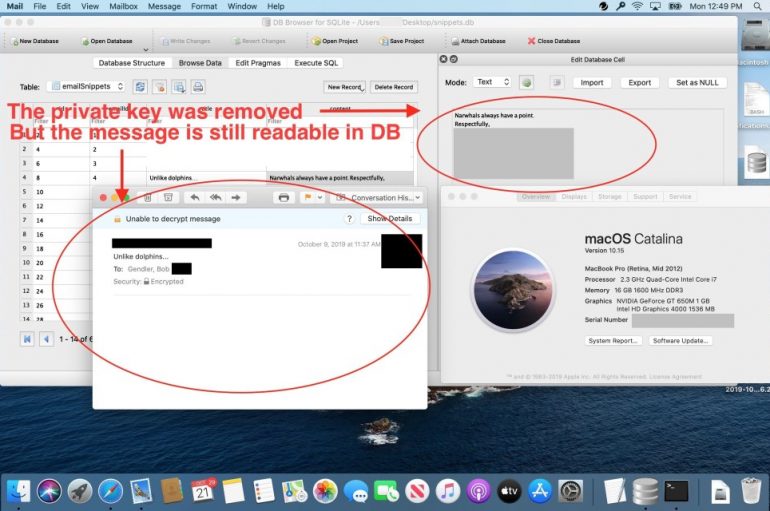
The Apple Mail app available on macOS stores leaves a portion of users encrypted emails in plaintext in a database called snippets.db. The Apple expert Bob Gendler discovered that the Apple Mail app available on macOS stores leaves a portion
This is really an embarrassing incident, ZoneAlarm forum site has suffered a data breach exposing data of its discussion forum users. ZonaAlarm, the popular security software firm owned by Check Point Technologies, has suffered a data breach. According to the
A black hat selling vulnerabilities can make as much money as a white hat researcher using bug bounty programs, or a grey hat working for a nation state doing reverse engineering. Speaking at a Tenable conference in London last week,
Researchers discovered a mass malware distribution campaign that utilizing the well-known political figures in the U.S. including President Donald Trump, former presidential candidate Hillary Clinton with a series of ransomware, screen lockers, RATs and other malicious applications. A variety of
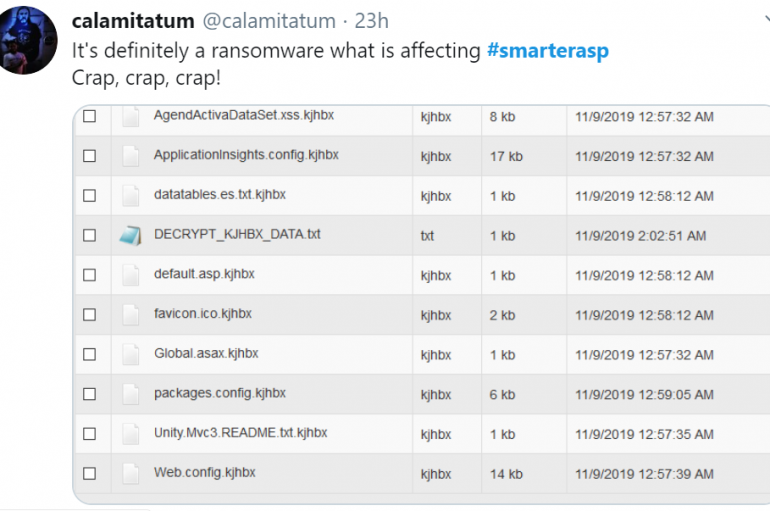
Another day, another victim of a ransomware attack, this time major ASP.NET hosting provider SmarterASP announced it was infected by ransomware. SmarterASP.NET is one of the most popular ASP.NET hosting providers, the company has more than 440,000 customers. SmarterASP announced
A new wave of malware attack strikes again from the Titanium APT group that infects windows with hidden backdoor by mimicking common legitimate software and fileless technique. Titanium APT is one of the technologically advanced hacking group, they are using
Free Antivirus apps on Google play asks users to explicitly agree for dangerous permissions that they are not required to operate. Even if you are installing an antivirus app, you should be careful with permission. While installing any app from
Researchers discovered seven malicious apps from Google play store that drops malware and adware on Android users and opens backdoor access to the attackers. These apps installed over 11,000 Android users from Google Play. These apps perform various malicious activities
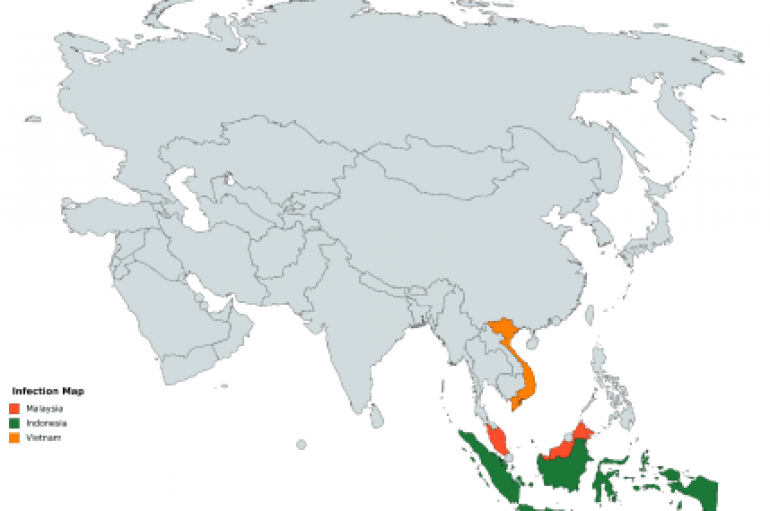
Kaspersky researchers have found a new advanced backdoor used by the Platinum advanced persistent threat (APT) group in attacks in the wild. Security experts at Kaspersky Lab have spotted a new backdoor, tracked as Titanium, that was used by the
In this first day, Ethical hackers earned $195,000 by exploiting the vulnerabilities that reside in the different products, In the second and final day of Pwn2Own Tokyo 2019, researchers made 6 attempts in various categories and earned $315,000 in total
Accenture Opens Cyber Ranges
Accenture has opened a trio of practice ranges in which companies can have a crack at responding to cyber-attacks. The new “cyber ranges” are specifically aimed at assisting industrial companies in the oil and gas, chemicals, utilities, and manufacturing industries
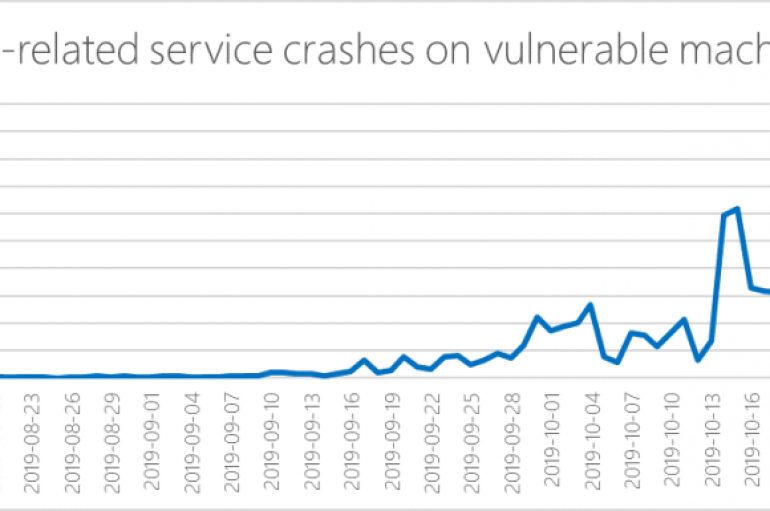
Microsoft is warning once again of more BlueKeep attacks that could deliver disruptive payloads and urges organizations to patch their systems. Recently, researchers warned of the first mass-hacking campaign exploiting the BlueKeep exploit, the attack aimed at installing a cryptocurrency
A recently discovered exploit kit dubbed Capesand is being involved in live attacks despite the fact that it’s still under development. In October 2019, researchers at TrendMicro discovered a new exploit kit dubbed Capesand that is being involved in live
The UK government is set to spend GBP1.8m developing anti-drone capabilities, as threats from the skies increase. The Ministry of Defence’s Defence and Security Accelerator (DASA) this week announced funding for 18 projects, which will each receive around GBP100,000. Successful
Microsoft Urges users to patch for BlueKeep RDP vulnerability as it could result in more effective attacks. The Bluekeep exploit can be used to deliver to more notorious malware. On November 2, 2019, security researcher Kevin Beaumont spotted the RDP
A vulnerability detected in Amazon doorbell cameras made it possible for hackers to gain access to the owner’s household computer network. The weakness in the Ring Video Doorbell Pro IoT device was discovered by researchers at Bitdefender in June of