Posts From CCME
2 Unpatched Critical RCE Bug Disclosed in Open Source Network Configuration Utility rConfig
Two unpatched remote command execution vulnerabilities have been identified in popular open-source network management system rConfig. Rconfig was written in PHP, a utility used by network engineers to record snapshots of the devices and to monitor device configurations for policy
Android Dropper App Infects 45K Devices
A malicious Android app that displays advertisements and facilitates the download of additional malicious apps has infected over 45,000 devices in six months. Researchers at Symantec observed a surge in detections of the Xhelper app, which has mainly been targeting
Midwest to Get First Cyber Battalion
America’s Midwest is to get its first National Guard cyber battalion. The 127th Cyber Battalion will comprise 100 soldiers, who will be based in Indiana. Before taking up their new command, the soldiers will head to the Muscatatuck Urban Training
Proofpoint has entered into a definitive agreement to acquire ObserveIT for $225m. Extending its data loss prevention (DLP) capabilities with the acquisition of the insider threat management provider, Proofpoint said that the combination of ObserveIT’s lightweight endpoint agent technology and
Global Registrar Web.com Suffers Major Breach
A global internet registrar with millions of customers has admitted suffering a data breach in August which exposed user account information. US-based Web.com, and subsidiaries Network Solutions and Register.com, discovered on October 16 that they were hit by an attack
Nikkei Hit in $29m BEC Scam
Media giant Nikkei has become the latest firm to suffer a humiliating Business Email Compromise (BEC), after it admitted losing $29m to scammers following human error. The Tokyo-headquartered firm, which owns the Financial Times, revealed in a brief statement that
New Gafgyt Botnet Targets Gaming Servers
Palo Alto Networks discovered a new version of Gafgyt botnet composed of Home & Small Office Wireless routers used to attack gaming servers. Palo Alto Networks researchers discovered a new version of Gafgyt botnet targeting home & small office wireless
Experts have spotted the first mass-hacking campaign exploiting the BlueKeep exploit, crooks leverage the exploit to install a cryptocurrency miner. Security researchers have spotted the first mass-hacking campaign exploiting the BlueKeep exploit, the attack aims at installing a cryptocurrency miner
How Hackers Remotely Hack your Car? Cyber Security Guide for Internet-Connected Car’s to Avoid Hacking
As if there aren’t already enough cybersecurity threats looming in our daily lives, there’s one garnering an increasing amount of attention–car hacking. Automotive cybersecurity is a term for the tools and techniques used to protect the electronic systems of a
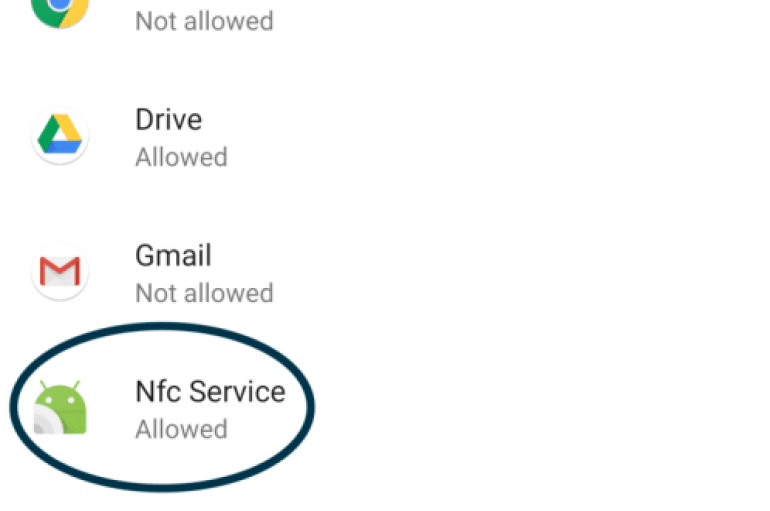
A vulnerability affecting devices running Andoid 8 (Oreo) or later, tracked as CVE-2019-2114, could be exploited by hackers to infect them via NFC beaming. Google has recently released a patch to address a vulnerability affecting devices running Android 8 (Oreo)
This is an emergency notice for all Chrome users!!! Google released an emergency update for Chrome that patches two new use-after-free vulnerabilities which include a zero-day bug that is actively exploiting in wide. New stable channel update to Chrome 78.0.3904.87
Working environments designed to empower only men are putting women off pursuing cybersecurity careers. Cybersecurity professionals speaking at the (ISC)2 Security Congress held in Florida this week revealed that talented women are taking their skills elsewhere because cybersecurity made them
A structured transdisciplinary approach could be the key to successfully engaging children in cybersecurity. Participants in a STEAM education panel held at the ninth annual (ISC)2 Security Congress called for cybersecurity to be taught as an integral part of all
The recruiting methods being used in the cybersecurity industry are so dire that they pose a national security threat. In an exclusive interview with Infosecurity Magazine at the (ISC)2 Security Congress in Orlando, Florida, the founder and CEO of cybersecurity
Twitter has announced a ban on political advertising ahead of crucial elections in the UK and US over the coming year, turning up the heat on Facebook to tackle micro-targeting campaigns on social media. At Infosecurity Europe earlier this year,
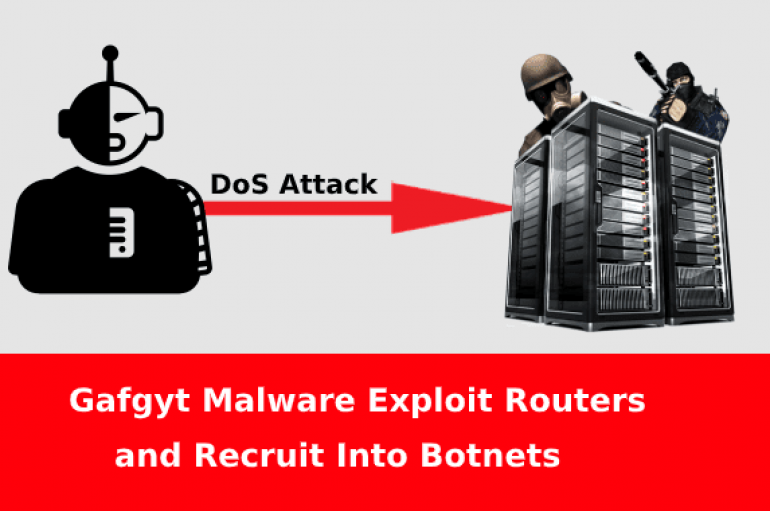
Gafgyt Malware Infect Wireless Routers and Recruit into Botnets to Attack Gaming Servers
Researchers discovered a new malware variant dubbed Gafgyt infect IoT devices specifically routers used in a small office and home network. The malware variant targets commercial routers like Zyxel, Huawei, and Realtek. It exploits remote execution code vulnerability in routers