Posts From CCME
Nearly half (45%) of citizens across seven countries – the UK, US, Canada, Australia, Russia, Norway and Sweden – do not trust the integrity of information they find online, according to an analysis by TunnelBear. This includes 48% of respondents
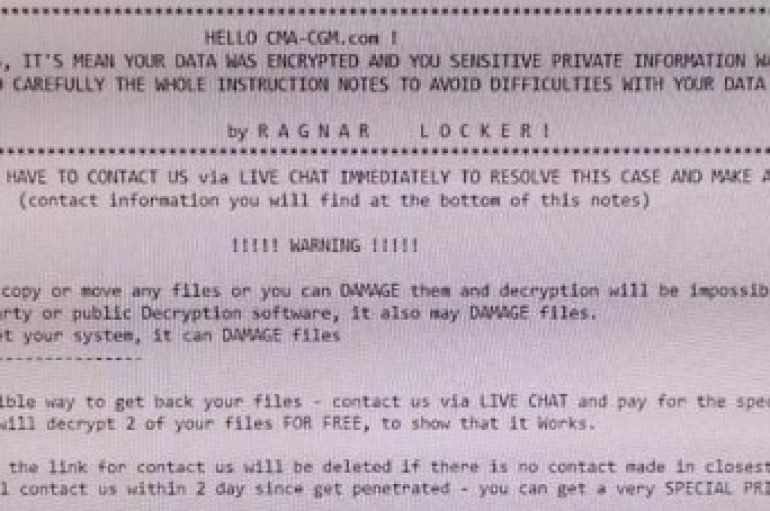
The French maritime transport and logistics giant CMA CGM S.A. revealed it was the victim of a malware attack that affecting some servers on its network. CMA CGM S.A., a French maritime transport and logistics giant, revealed that a malware attack affected
OCR Imposes $6.85M Penalty Over Data Breach
A health insurance company in Washington state has been slapped with the second-largest ever HIPAA violation penalty. The Department of Health and Human Services’ Office for Civil Rights (OCR) has imposed a $6.85m penalty on Premera Blue Cross to resolve
One in five (20%) UK employees have downloaded commercially sensitive or confidential company files on a personal device whilst working from home, a new study from gadget insurance firm Protect Your Bubble has found. What is more, of these respondents,
Ivanti has announced the acquisitions of mobile device management vendor MobileIron and secure access and VPN provider Pulse Secure. Under the terms of the agreement, Ivanti will acquire all outstanding shares of MobileIron for a total value of approximately $872m.
Over a third of government and enterprise users have been given privileged access despite not needing it, potentially exposing their organization to greater cyber-risk, according to Forcepoint. The security vendor polled nearly 1900 privileged users in the UK and US
Police Scotland is to establish a “center of excellence” for cybercrime with specialist staff deployed to help combat online offences including child sexual abuse, fraud and the sharing of indecent images. As reported by the BBC, the center will have
A European fashion retailer has become the latest big-name brand to expose personal data on millions of its customers after misconfiguring a cloud database. Researchers at vpnMentor discovered the unencrypted Elasticsearch server on June 28 and parent company BrandBQ finally
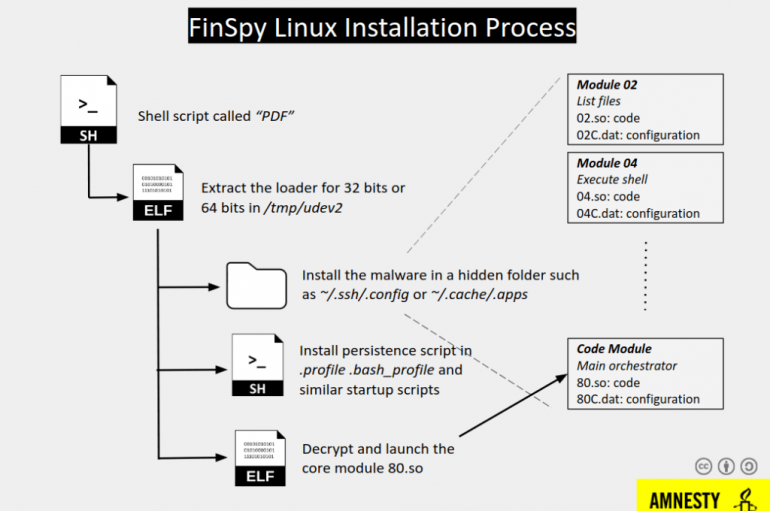
Experts from Amnesty International uncovered a surveillance campaign that targeted Egyptian civil society organizations with a new version of FinSpy spyware. Amnesty International uncovered a new surveillance campaign that targeted Egyptian civil society organizations with previously undisclosed versions of the
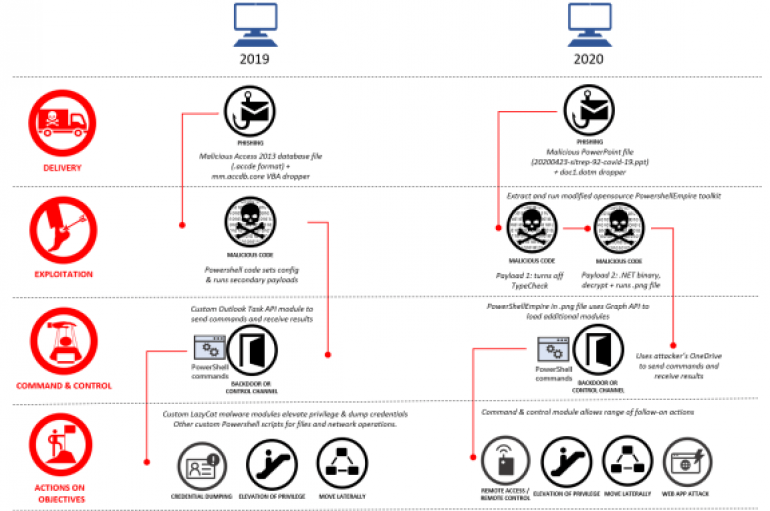
Microsoft removed 18 Azure Active Directory applications from its Azure portal that were created by a Chinese-linked APT group Gadolinium. Microsoft announced this week to have removed 18 Azure Active Directory applications from its Azure portal that were created by
Texas Software Provider Reports Cyber-attack
A cyber-attack has struck a Texas company that provides software services to schools and state and local governments across the United States. Tyler Technologies notified customers on September 23 that its phone and computer systems had been compromised by a
US Federal Agency Compromised by Cyber-Actor
A warning has been issued by America’s Cybersecurity and Infrastructure Security Agency (CISA) after a malicious cyber-actor compromised a United States federal agency. The attacker used valid log-in credentials for multiple users’ Microsoft Office 365 accounts and domain administrator accounts
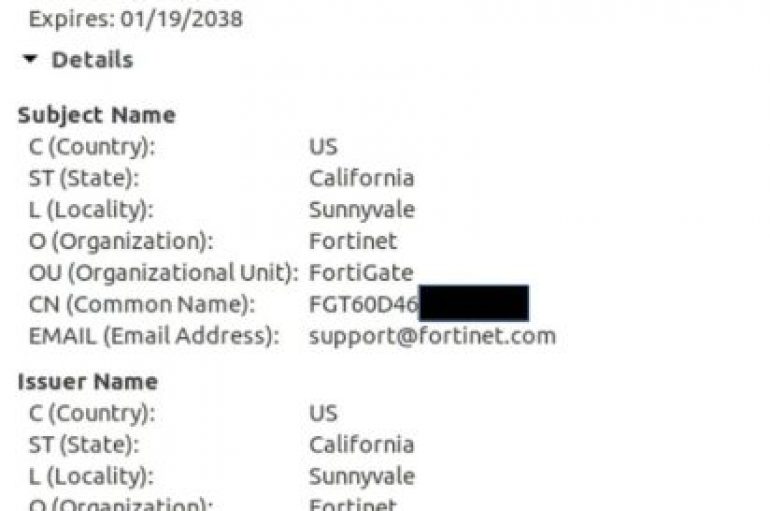
According to SAM Seamless Network, over 200,000 businesses are using Fortigate VPN with default settings, exposing them to the risk of a hack. In response to the spreading of Coronavirus across the world, many organizations deployed VPN solutions, including Fortigate
Cyber-criminals stole more than GBP4m from elderly people in the UK in the financial year 2018-19, data received by the charity Age UK has revealed. A freedom of information (FOI) request submitted by the charity to the UK’s national fraud
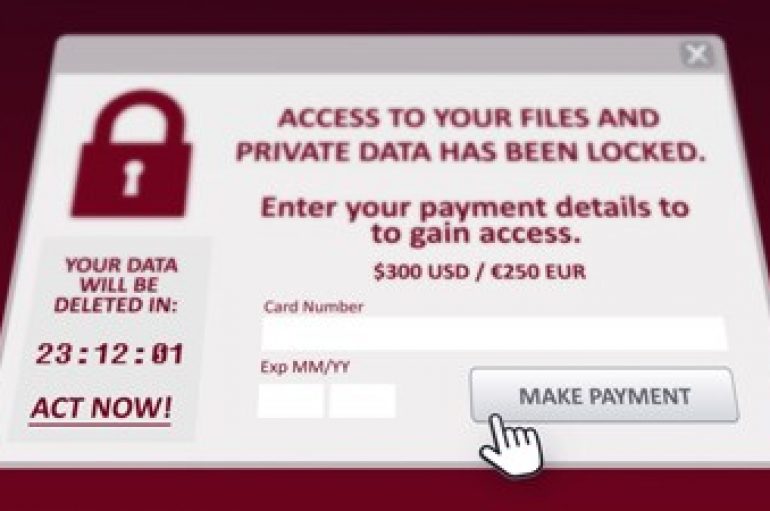
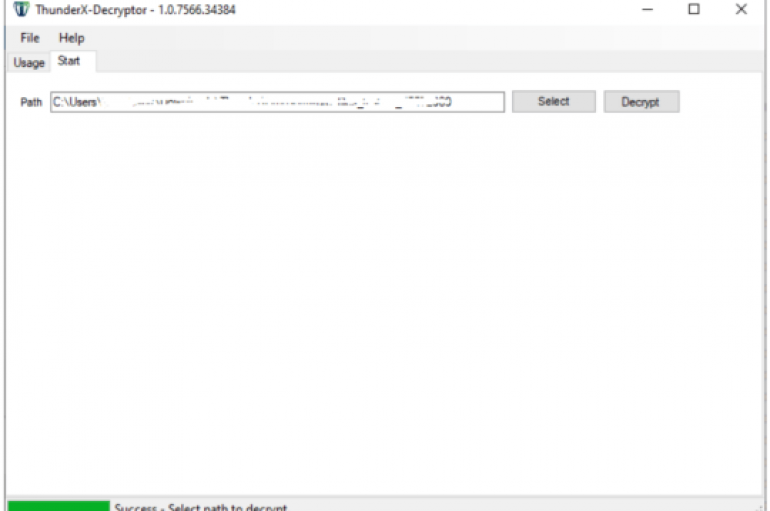
Good news for the victims of the ThunderX ransomware, cybersecurity firm Tesorion has released a decryptor to recover their files for free. Cybersecurity firm Tesorion has released a free decryptor for the ThunderX ransomware that allows victims to recover their
Facebook has been forced to remove over 150 fake accounts tied to Beijing’s efforts to influence public opinion in south-east Asia. The social media giant describes influence operations like this as “coordinated inauthentic behavior” (CIB), as those behind them use