Archive
A new wave of cyber attacks carried out by a China-linked APT group hit German blue-chip companies BASF, Siemens, Henkel and others. On Wednesday, German blue-chip companies BASF, Siemens, Henkel along with a host of others confirmed they had been
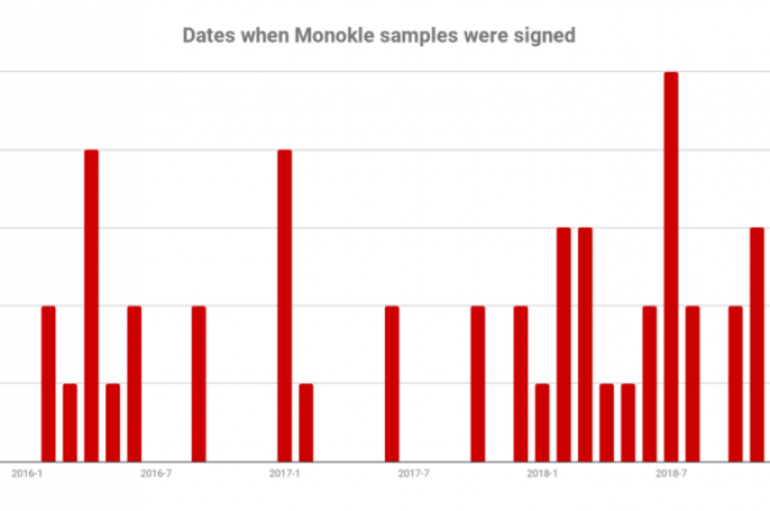
Android Spyware Monokle, Developed by Russian Defense Contractor, Used in Targeted Attacks
Researchers at Lookout discovered a new mobile spyware dubbed Monokle that was developed by a Russian defense contractor. Experts at Lookout discovered a new Android mobile spyware in the wild, dubbed Monokle, that was developed by a Russian defense contractor
In today’s threatscape, antimalware software provides little peace of mind. In fact, antimalware scanners are horrifically inaccurate, especially with exploits less than 24 hours old. Malicious hackers and malware can change their tactics at will. Swap a few bytes around,
APT17 Outed as MSS Operation
A group of anonymous researchers have outed the APT17 cyber-attack group (aka DeputyDog) as a Chinese Ministry of State Security (MSS) operation, potentially paving the way for more US indictments. Intrusion Truth have been right before, when they identified APT3
The Underground hacking Forums are the market place for cybercriminals to advertise various malware variants and other hacking tools. A new report represents the top malware families advertised. By analyzing more than 3.9 million posts, Recorded Future’s, Insikt Group identified
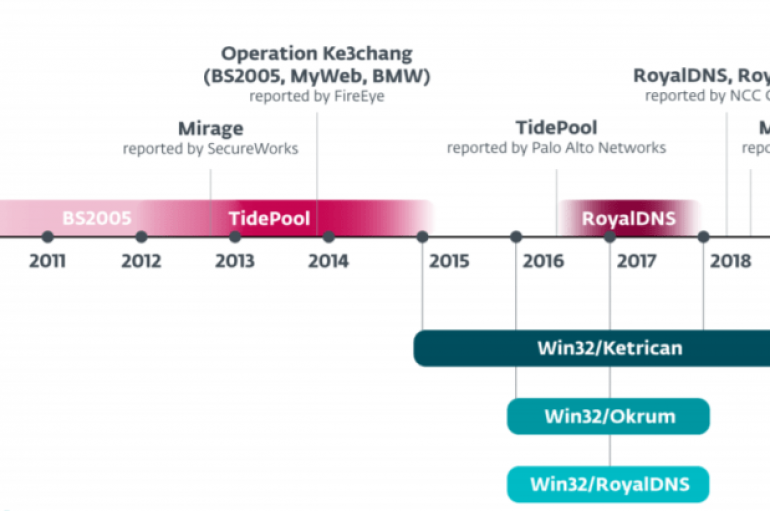
APT15 Hackers Using Steganography Technique to Drop Okrum Backdoor Via PNG File to Evade Detection
Researchers discovered a previously unseen malware called Okrum that distributed from APT15 threat group via a hidden PNG file with steganography technique to evade detection. APT15 threat group also known as Ke3chang has a long history of its malicious activities
VideoLAN’s VLC Media Player Has Serious Flaw
The latest edition of nonprofit VideoLAN’s VLC media player software has what Germany agency CERT-Bund is calling a serious security flaw that allows hackers to install and run software without user knowledge, according to NewsX. “This is just one in
Cybercrime Costs Global Economy $2.9m Per Minute
In just one minute on the internet, $2.9 million is lost to cybercrime, according to the annual Evil Internet Minute report from RiskIQ. After analyzing proprietary research and data derived from the volume of malicious activity on the internet, the
NSA Launches New Unit to Tackle Foreign Threat
The NSA has announced a new unit tasked with taking on foreign adversaries like Russia and China in cyberspace. The Cybersecurity Directorate, which will be operational from October, is to be led by Anne Neuberger. She previously led an NSA
Researchers discovered five critical vulnerabilities in Comodo Antivirus / Advanced version. Out of five vulnerabilities four present in version 12.0.0.6810 and one with 11.0.0.6582. The vulnerabilities discovered at Tenable by David Wells, these vulnerabilities could be exploited by the attacker
Multiple zero-day vulnerabilities could allow malicious actors to attack Comodo antivirus software and install malware to escalate to the highest privileges, according to Tenable Research. Though antivirus software is used to protect PCs and other devices from unknown malware and
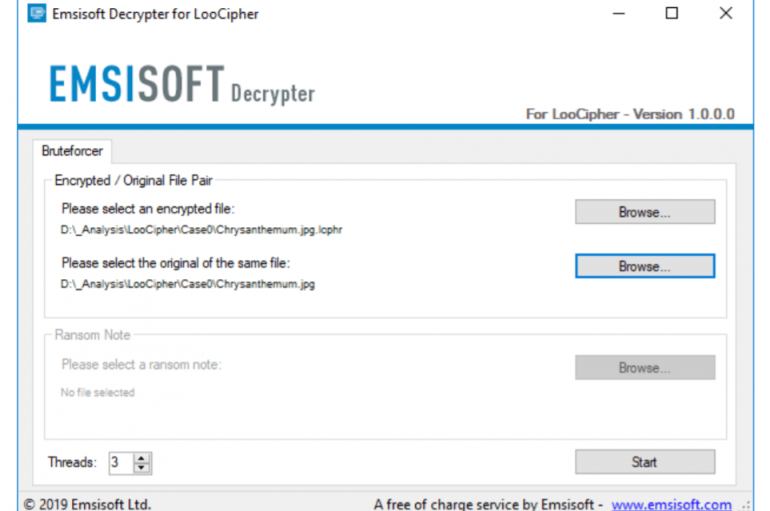
Security experts at Emsisoft released the third decryptor in a few days, this time announced a free one for the LooCipher ransomware. A few days ago, the experts at Emsisoft released two free decryptors for the ZeroFucks ransomware and Ims00rry
Experts at Defiant have uncovered a campaign that exploited recently disclosed plugin vulnerabilities to inject malware into websites. Experts at Defiant, the company that developed the Wordfence security plugin for WordPress, uncovered a malvertising campaign that leverages recently disclosed plugin
ESET researchers reported that China-linked cyberespionage group APT15 has been using a previously undocumented backdoor for more than two years. Security researchers at ESET reported that China-linked threat actor APT15 (aka Ke3chang, Mirage, Vixen Panda, Royal APT and Playful Dragon)
Xerosploit – Pentesting Toolkit to Perform MITM, Spoofing, DOS, Images Sniffing/Replacement, WD Attacks
Xerosploit is a penetration testing toolbox whose objective is to perform the man in the middle attacks. It brings different modules that permit to acknowledge proficient assault and furthermore permits to do DOS attacks and port filtering. We can use
FIN8 Reappears with BADHATCH Malware
The financially motivated threat group known as FIN8 has recently reemerged after being somewhat dormant, according to new research from Gigamon’s applied threat research (ATR) team. Researchers have published findings that show FIN8 continues to evolve and adapt its tools.