
What is a CASB? What You Need to Know Before You Buy
CASB definition
Think of cloud access security brokers (CASBs) as central data authentication and encryption hubs for everything your enterprise uses, both cloud and on-premises and accessed by all endpoints, including private smartphones and tablets. Before the CASB era, enterprise security managers had no visibility into how all their data was protected. They have become especially important as more enterprises allow personal phones and other unmanaged devices onto their networks, bringing more risk into their endpoint portfolios.
As cloud computing took off, enterprises needed a way to deliver consistent security across multiple clouds and protecting everyone using their data. CASBs arrived to help give organizations much deeper visibility into cloud and software-as-a-service (SaaS) usage — down to individual file names and data elements.
Most of the main-line security vendors have purchased CASB solutions over the past several years: Oracle (Palerra), Cisco (CloudLock), IBM (Gravitant), Microsoft (Adallom), Forcepoint (Skyfence), Proofpoint (FireLayers), Symantec (Elastica and Perspecsys) and McAfee (Skyhigh Networks). This merger mania has abated in the past year and there are three major CASB independent vendors remaining: CipherCloud, Netskope and Bitglass.
Both Forrester and Gartner in their latest comparison reports have anointed McAfee, Symantec and Netskope as CASB market leaders.
CASBs as important as firewalls
CASBs have matured, although this is a matter of degree since even the longest-running vendors have only been selling products for a few years. They have also evolved to the point where many analysts feel CASB will soon be just as important as firewalls once were back in the day when PCs were being bought by the truckloads. Gartner predicts that by 2022, 60% of large enterprises will use CASBs, up from the 20% that used them at the end of 2018. Forrester predicts that cloud security will become a $112.7B market by 2023.
Several years ago, many enterprises purchased CASBs to stem the tide of what was then called shadow IT and is now considering standard operating procedure in many businesses. IT managers would get a call from their commercial Dropbox sales rep and be told that hundreds of their users were using personal Dropbox accounts, which was often news that they didn’t want to hear. That was the initial sales pitch by the CASB vendors: we can discover where all your cloud data lies and help to protect it. Traditional security tools didn’t provide this visibility, especially when the network traffic never was seen by the corporate data center. “I want to have control over my data, even when it isn’t residing in my own machines,” said Steve Riley of Gartner.
The first attempts at using CASBs were eye-opening for many corporate IT managers. When they were first deployed, IT would find ten times the number of cloud services in use than they thought they had estimated, according to Riley. That turned into a big selling point.
How the modern CASB fits in today’s IT and threat landscape
That was great then, but today’s CASBs are more fully featured and integrated into the alphabet soup of enterprise security. Many vendors offer ways to connect their product to email servers to track and prevent data leakage (either deliberate or unintentional), web application gateway devices, identity management systems, and single sign-on tools.
Enterprise IT managers want deeper control over their cloud data beyond the initial login, and so have come to want more from their authentication tools than a simple binary yes or no to vet user logins, what is called risk-based or adaptive authentication. This means they want to step up authentication challenges to ensure that their most sensitive content doesn’t end up in criminal hands. Several of the CASB vendors integrate these tools into their products now, including Forcepoint.
Another force has been an increase in compliance rules, such as the enactment of the EU’s General Data Protection Regulation (GDPR) and the greater publicity of numerous data breaches. A CASB can show in a single place where a corporation has the most risk and summarizes issues that a security team can quickly focus on for suspicious behavior that other products couldn’t easily do. (As an example, see the Forcepoint risk summary dashboard below.)
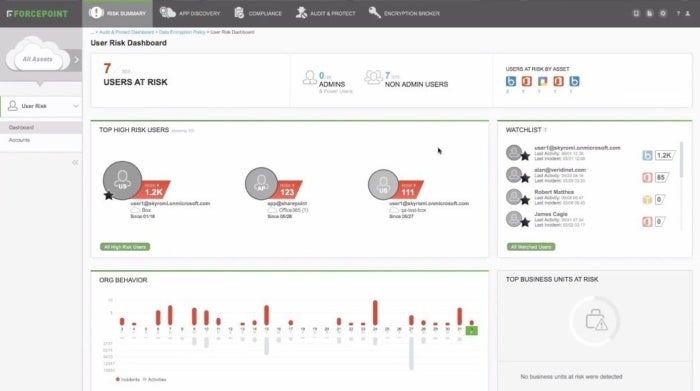 ForcePoint
ForcePointIn addition, the quick adoption of cloud computing has made CASBs more compelling. Jay Barbour talked about the shared security model between cloud and on-premises applications in this blog post. He is the director of security product management at Masergy which sells managed CASB services from several vendors. “As soon as the cloud application count goes above one or two, having employees managing their own identities and passwords quickly become a tangle of security risks and poor user experience,” he wrote.
Just a few years ago, you could find a few companies moving to Google or Microsoft cloud-based email, but that was just the beginning of the mass migration. Microsoft offered attractive licensing models to encourage more enterprises toward using Office 365 and away from installing its software. Many corporations accelerated their purchases of cloud resources from multiple providers, so a tool such as CASB was needed to bridge the security gaps between resources spread across AWS and Azure, for example. As companies moved their resources out of their data centers – or eliminated them entirely – CASBs became essential security tools. “There is no way to install security agents to protect files stored on Box or OneDrive,” says Forrester in its report.
Finally, the threat landscape has evolved, even from just a few years ago. Now we have more blended threats using multiple exploits along with numerous obfuscation technologies to make malware harder to find. More subtle phishing attacks are getting harder to recognize, even by experienced IT staff, or that exploit very subtle features of cloud services that can quickly go viral and infect millions of users. CASBs are now being used for shoring up malware protection, according to a new Bitglass survey. Added to this is that the number of data leaks caused by sloppy (or missing) access rights to various cloud-related data repositories such as AWS S3 or ElasticSearch continues to grab headlines. Digital Shadows found that in 2018 there were 1.5 billion files exposed around the world solely due to misconfigurations in cloud services. CASBs can sometimes be the last bulwark to catch these issues.
Four things also helped the CASB cause: First was its quick learning curve by security personnel. These tools are relatively easy to bring online, and the dashboards make their reports more understandable, certainly easier than trying to order firewall rule sets or create appropriate policies on DLP products.
Second was that they became more inclusive in terms of applications support. The early products had a limited portfolio of apps they could protect: That has widened considerably. Forcepoint, for example, claims that it can spin up support for any custom app within a few days’ effort. Bitglass has a feature that can detect changes in underlying apps that might elude traditional reverse proxies. McAfee’s CASB can create custom prevention policies for apps without any coding.
Third was that multimode operation has become more prevalent. CASBs operate in one of three different modes, and more products now support more apps in each mode:
- Forward proxy, usually deployed with endpoint agents or VPN clients
- Reverse proxy, which don’t require agents and can work better for unmanaged devices
- API control, which provides visibility into data already stored in cloud repositories or data that is used within a cloud process that never enters a corporate network.
Some vendors break up this functionality into multiple products: Cisco only supports API access in its CASB and provides proxies via its Umbrella product. Saviynt also has an API-only product. Others, like Microsoft, require a series of prerequisite products before you can fully use its CASB product.
Finally, the need for better GDPR compliance has become more compelling, particularly as EU regulators are now issuing major fines for violations (such as what has happened with Marriott and British Airways recently).
How to buy the right CASB solution
Before you get started in your evaluation, check out one of the CASB vendors’ free service plan to discover your cloud portfolio. Cofense has Cloudseeker, which also performs this service (but doesn’t sell a CASB solution). Most vendors offer the first month with a limited number of apps or services for free. This will give you an idea of the scale and scope of your exposure and how the tool works within your infrastructure. Links to the various products are at the end of this article.
Here’s what to consider before you buy a CASB:
- Pick your most critical apps to pilot a CASB project initially and run a product through its paces with this smaller set before you widen its scope.
- Figure out if you want to integrate with existing identity-as-a-service (IDaaS)/single sign-on (SSO) tools.
- Don’t view cloud access as a simple “yes” or “no” authentication event. Understand when and how you will need more granular and risk-based authentication and whether you want a CASB to deliver this functionality.
- Understand if and how your product supports field-level data encryption.
- Look at the multimode CASBs so you can have flexibility for complete coverage across as many possible use cases, and make sure you understand a product’s limitations in each of the three operating modes.
- Examine if your product integrates with your secure web gateways, application firewalls, data loss prevention tools and email providers. Examine these features offered by the CASB versus what you already have in place.
- Calculate the costs. Gartner puts the range between $15/user/year for simple installations of just a few cloud apps to a more robust coverage for multimode unlimited cloud apps at $85/user/year.
Major CASB vendors
The links below go to free trial pages or video screencast demos where available.
- Bitglass
- CensorNet
- CipherCloud
- Cisco Cloudlock
- Forcepoint CASB
- IBM Managed Cloud Services
- ManagedMethods
- Masergy
- McAfee/Skyhigh Security Cloud
- Microsoft Cloud App Security
- Netskope (video demo)
- Oracle CASB Cloud Service
- Palo Alto Networks Aperture
- Perimeter81
- Proofpoint CASB
- Saviynt
- Symantec/Skycure CloudSOC
This story, “What is a CASB? What you need to know before you buy” was originally published by
Network World.


