Archive
Burp is one of the most famous tools used by pentesters, which incorporates a full static code investigation engine to discover vulnerabilities. PortSwigger Security Burp Suite 2.1.02 with WebSockets in Burp Repeater. The Burp scanner is one of the widely
w3af is an open-source web application security scanner (OWASP Top 10) which enables developers and penetration testers to distinguish and exploit vulnerabilities in their web applications especially OWASP Top 10 Vulnerabilities. This tool also provides GUI framework but sadly most
Cybercriminals using fake Google domain to infect the Credit card skimmer in Magneto websites using Internationalized domain name (IDN) EX: google-analytics[.]com or xn--google-analytcs-xpb[.]com ASCII. Researchers found a Magento website blacklisted by McAfee SiteAdvisor. Later, they digging deeper and found that
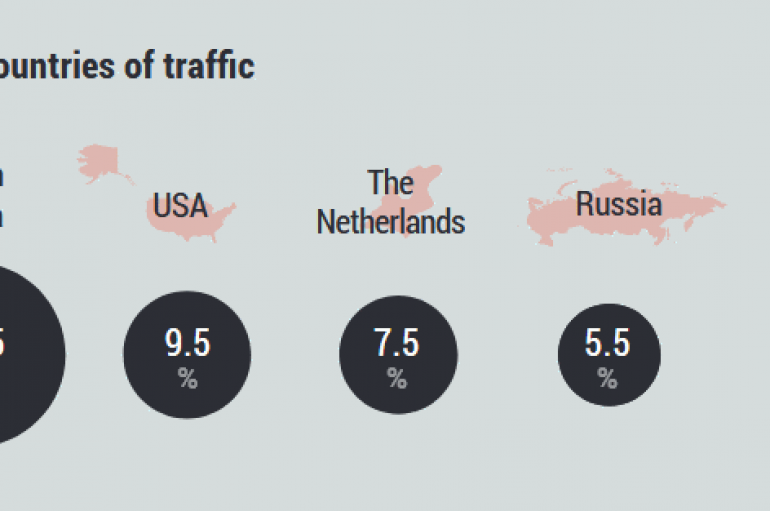
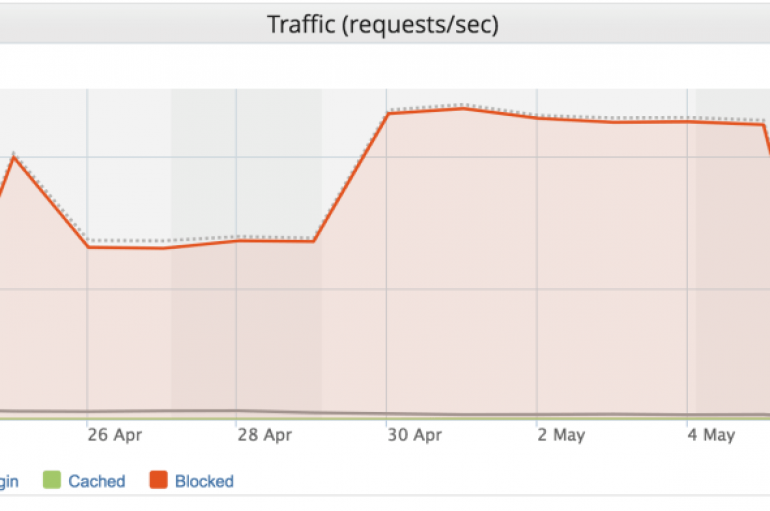
An unrevealed streaming site hit with massive DDoS attack from 402,000 different IoT(Internet of Things) Botnet IPs, which directed a peak flow of 292,000 RPS (Requests Per Second). DDoS Attack is one of most dangerous threat for any organization and
According to a report published by cybersecurity firm Sixgill data for over 23 million payment card were on offer in underground forums in the first half of 2019. A report published by cybersecurity firm Sixgill revealed that data for over
Over the past three years, the website of No More Ransom was visited by 3 million users and allowed to save $108 million in ransom to the victims of 109 ransomware. After three years, No More Ransom confirms the success
Unpatched RCE Vulnerability in LibreOffice Let Hackers Take Complete Control Of Your Computer
The researcher discovered a code execution vulnerability in LibreOffice let an attacker hack your computer by just sending a weaponized document with macro and promote a user to Open it via LibreOffice. LibreOffice is an open-source office suite alternative of
Uptick in Ransomware, Mobile Banking Malware
Ransomware dominated the first half of 2019, while mobile banking malware threats grew by more than 50% from 2018 to 2019, according to Check Point’s Mid-Year Trends Report. “This year collaborations between threat actors allowed even more destructive attacks that
Monokle – Mobile Surveillance Malware Developed by Russian Defense Contractor Spy Android Users in Wide
Security researchers observed a highly targeted Android mobile surveillanceware malware dubbed Monokle that compromises users privacy by stealing user data and exfiltrate the data to remote servers. Lookout researchers able to link the malware associated with Russian defense contactor STC,
Researchers have found over 23 million stolen credit and debit cards up for sale on the dark web, with US consumers by far the biggest hit. Nearly two out of every three stolen cards on the sites trawled by Sixgill
Hackers attack Electric utility City Power on Johannesburg, South Africa using powerful ransomware and take down the entire network, applications, and database. Recent days threat actors mainly targeting the government network, cities, municipalities around the world to demand the huge
An undisclosed streaming service was hit by a 13-day DDoS massive attack powered by a Mirai botnet composed of 402,000 IoT devices. Imperva confirmed that its systems were able to repel the attack and the service remained up and running
Noam Rotem and Ran Locar with their research team found a database leak in YouHodler. YouHodler, A Crypto lending site offered an easy way for its users to apply for crypto-loans or turn their crypto-holdings into fiat currencies. The breach
Experts at Intezer researchers have spotted a strain of the Linux mining that also scans the Internet for Windows RDP servers vulnerable to the Bluekeep. Researchers at Intezer have discovered a new variant of WatchBog, a Linux-based cryptocurrency mining botnet,
93% of Organizations Cite Phishing as Top Threat
Email remains the vector of choice for cyber threat actors with the majority of organizations citing phishing as their top perceived threat, according to a new survey from Dimensional Research and Barracuda Networks. With the rise of more complex, advanced
Campaign Targets Government IT in Eastern Asia
A cyberattack campaign using malicious RTF documents has been targeting government IT agencies in Eastern Asia, according to research published today by Proofpoint. Dubbed Operation LagTime IT, the malicious documents delivers custom Cotx RAT malware to tech agencies responsible for