Archive
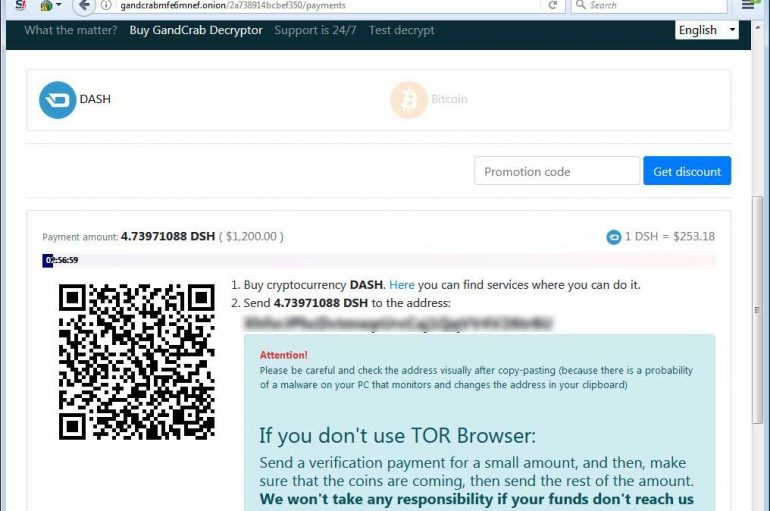
Good news for the victims of the latest variants of the GandCrab ransomware, NoMoreRansomware released a free decryption tool. Victims of the latest variants of the GandCrab ransomware can now decrypt their files for free using a free decryptor tool
The cyber attack occurs on a daily basis, and these can range from attacks on tech giants to individuals falling foul to the many scams which are present online. Thankfully, there are ways in which people and groups at both
Venmo users are being advised to set their accounts to private after a computer science student scraped seven million Venmo transactions, proving that users’ public activity can be easily accessed, according to The Next Web (TNW). Over a six-month period,
Eliminate Outdated Identity Proofing, Says GAO
The remote identity proofing used by four large government agencies has been deemed outdated by a new report released by the U.S. Government Accountability Office (GAO). According to the report, the Postal Service, Department of Veteran Affairs, Social Security Administration
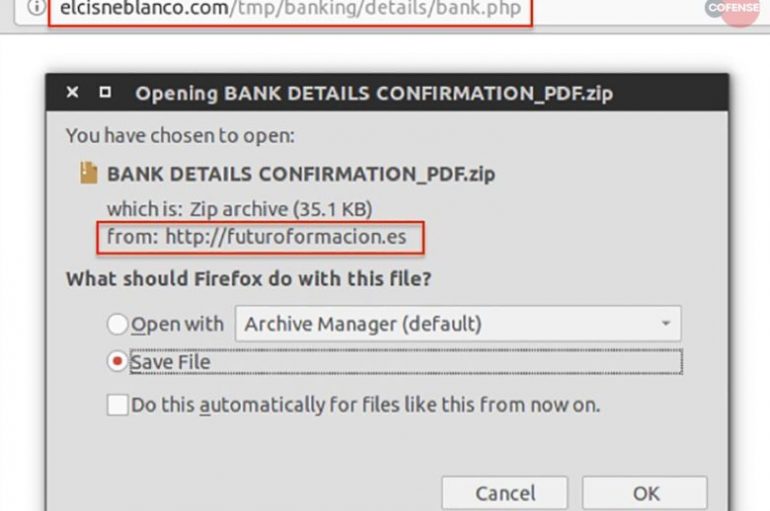
Security researchers at Cofense have spotted a phishing campaign aimed at commercial banking customers distributing a new remote access trojan (RAT) tracked as WSH RAT. Security experts at Cofense Phishing Defence Center have spotted a phishing campaign aimed at commercial
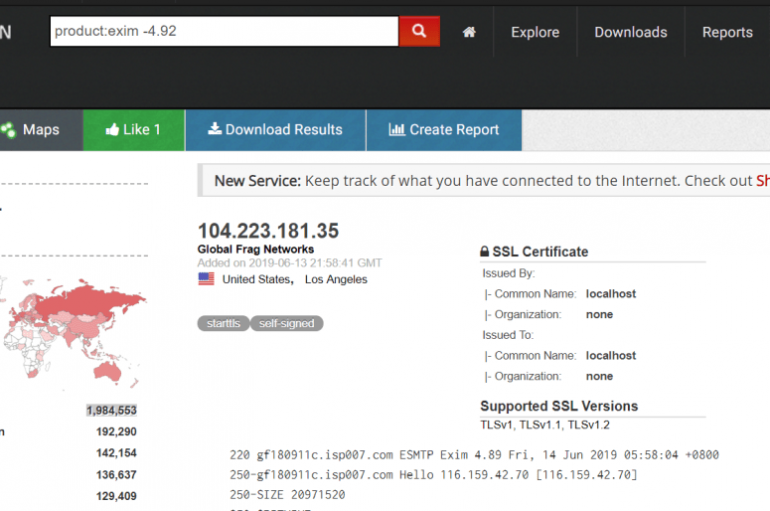
Microsoft has urged Azure users to update their systems following the discovery of a major new attack campaign targeting popular email server software. The worm, which Infosecurity reported on last week, targets mail transfer agent product Exim running on Linux-based
Twitter Shuts Down 5000 State-Sponsored Accounts
Twitter has taken down nearly 5000 fake accounts, most of them apparently backed by the Iranian state, in a bid to clean the platform of government-sponsored attempts to spread propaganda. The social network claimed in a post last week that
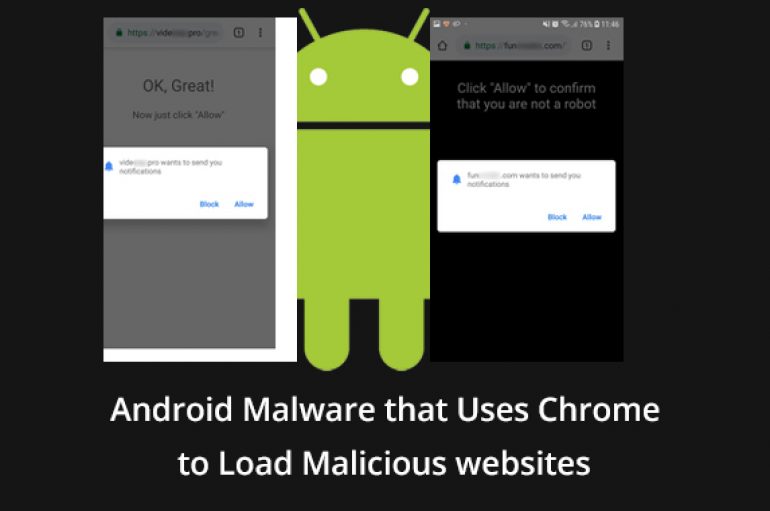
New malware spotted on Google play that directs users to malicious websites and subscribes users to advertising notifications. The malware is distributed hidden under the official software of well-known brands. The web push notification is the feature that allows websites
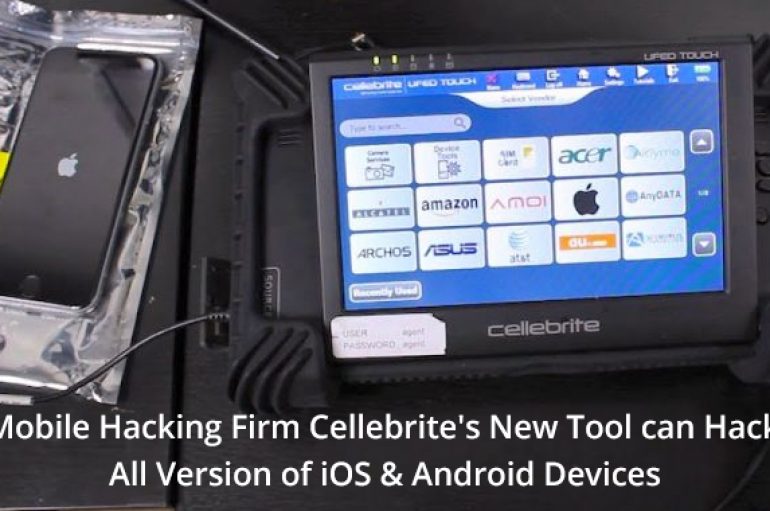
Israeli forensics firm and well-known Law enforcement contractor Cellebrite released a public statement that they can hack any iOS and High-end Android devices for law enforcement agencies. Cellebrite Mobile Synchronization is an Israeli company that manufactures data extraction, transfer and
On Friday, security experts at Microsoft warned of a new Linux worm, spreading via Exim email servers, that already compromised some Azure installs. Bad actors continue to target cloud services in the attempt of abusing them for several malicious purposes,
Hackers Delivering WSH Remote Access Tool (RAT) via Phishing Campaign to Attack Banking Customers
Researchers discovered a new wave of a phishing campaign that delivering a new variant of Houdini Worm named as WSH Remote access tool to attack commercial banking customers. Malware authors initially released this tool on June 2, 2019, and the
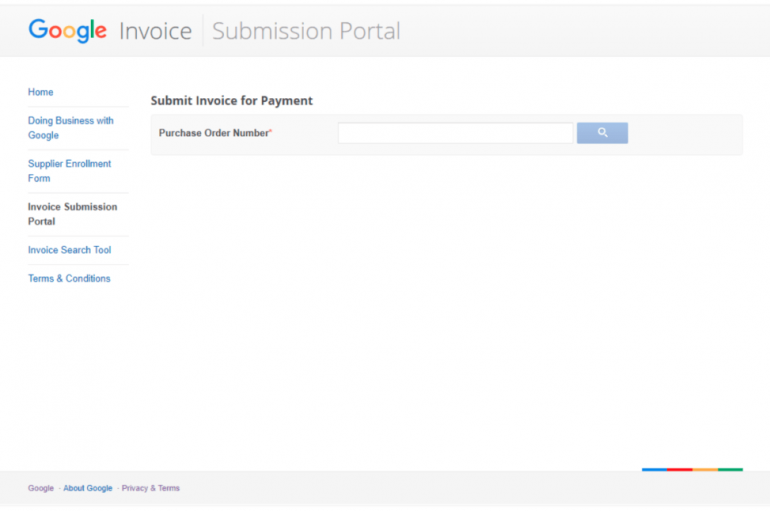
XSS Flaw Would have allowed Hackers Access to Google’s Network and Impersonate its Employees
Bug hunter Thomas Orlita discovered an XSS vulnerability in Google’s Invoice Submission Portal that would have allowed attackers access to Google’s internal network The Czech researcher Thomas Orlita discovered an XSS vulnerability in Google’s Invoice Submission Portal that would have
The infamous XENOTIME Hacking group expanded its target beyond oil and gas to the electric utility sector. XENOTIME threat actor group responsible for TRITON malware that is capable of causing physical damage and inadvertently shut down operations. XENOTIME group uses
New Version of Echobot Botnet using 26 Powerful Exploits to Attack Oracle, D-Link, Dell Apps
New Mirai level Botnet Echobot using 26 different exploits for the infection vectors that leveraging the vulnerabilities in Oracle, D-Link, Dell, LINKSYS, REALTEK, Vmware applications and take control of it. Since 2016, Mirai variant spreading via hundreds of campaigns, similarly
Experts at Dragos firm reported that Xenotime threat actor behind the 2017 Trisis/Triton malware attack is targeting electric utilities in the US and APAC. Xenotime threat actor is considered responsible for the 2017 Trisis/Triton malware attack that hit oil and
Free Open Source Penetration Testing Distro BackBox Linux 6 Released with New Hacking Tools
BackBox Linux is a free Open Source penetration testing and security assessment oriented Linux distribution providing a network and systems analysis toolkit. It has been developed to perform penetration tests and security assessments. Designed to be fast, easy to use